Why Computer Forensics needs in Today’s World
Understand Computer Forensics
Computer Forensics is a type of digital forensics that deals with crimes committed across computing devices such as computers, networks and digital storage media. It refers to a set of methodological procedures and techniques for identifying, gathering, preserving, extracting, interpreting, documenting, and presenting evidence from computing equipment, such that the discovered evidence is acceptable during legal or administrative proceedings in a court of law.

In summary, computer forensics deals with the process of finding admissible evidence related to digital crimes to identify responsible person and initiate legal action against them.
Objectives
- Identify, gather, and preserve evidence of cybercrime.
- Interpret, document, and present evidence that is admissible during prosecution.
- Find vulnerabilities and security loopholes that help attackers to breach data.
- Recover deleted data, carved data, hidden data, and temporary data were used as evidence.
- Perform incident response to prevent further loss of intellectual property, reputation, and finances during an attack.
- Support incident response procedures by identifying the scope of cybercrime, its origin, and recovery methods.
- Follow the first responder’s procedure and access the victim’s computer/Laptop.
- Reveal the intention behind the crime and identify the culprit.
- Make protocols at a crime scene that help preserve digital evidence without corruption.
- Minimize tangible (physical present) and intangible (imaginary) losses to the organization.
- Protect organizations from similar incidents in the future.
Why and When Do You Use Computer Forensics?
Computer forensics is required when a computer-based crime occurs, such crimes are increasing globally. When the complexity of cybercrimes increases, there will be a need for computer forensic expertise to identify perpetrators, preserve evidence, investigate, report and bring them to legal processes. Additionally, computer forensics is crucial for investigating cybercrime and safeguarding organization against future threats.
Scope of computer Forensics

Computer forensics has a wide scope for investigating, analyzing, reporting and extracting data from digital evidence acquired from crime scenes. This is growing rapidly as the use of digital technology increases.
The following are some of the important areas the computer forensics has huge scope:
- Digital Crime Investigation: Computer forensic techniques are very helpful in investigating digital crimes such as online fraud, cyberstalking, spoofing, phishing emails, unauthorized access, and data breaches. It also helps in identifying the culprit by analyzing digital evidence and performing further investigations.
- Data Recovery: Data recovery is also a part of computer forensics, in which forensic tools and techniques are used to recover lost/deleted/corrupted data from digital devices. This data recovery method can also be used to recover important digital artifacts that are relevant to the investigation, using specialized tools and techniques.
- Incident Response: Computer forensics plays an essential role in responding to security incidents and cyberattacks. Forensic investigators use computer forensic techniques and tools while analyzing cyberattacks to determine the root cause of an incident.
- eDiscovery: Forensic investigators use eDiscovery as a part of computer forensics to identify, collect, preserve, analyze and report digital evidence in support of regulatory compliance and litigation.
- Malware Analysis: Malware analysts use computer forensic tools to analyze malware infected digital devices and examine malware samples to determine their behavior and effects on the infected digital devices.
- Network Forensics: Computer forensics helps in investigating network traffic, detect unauthorized access to organization assets, and track attack paths.
- Data Analysis: Computer forensics helps in analyzing digital evidence, reconstructing events, establishing timelines, correlating data, and drawing conclusions based on the data analysis.
- Corporate Investigations: Most corporate sectors have separate computer forensics departments to handle cyberattacks, such as data breaches, privilege escalation, intellectual property theft, and financial crimes.
Understand Cybercrimes and their Investigation Procedures
Understand Cybercrimes
Cybercrime refers to any illegal act involving digital devices, computing systems, applications, or networks/servers. The type of cybercrime committed is identified based on the nature of the crime and depends on the tools & techniques of the crime and its target.
Types of Cybercrimes
Cybercrimes can be classified as internal/insider attacks and external attacks.

Internal/Insider Attacks
Internal or insider attacks originate from people within the organization, such as frustrated employees, current or terminated employees, business associates, contractors, and under training staff. These insiders have legitimate access to computer devices and the organization’s data and use such access negatively to harm the organization. Because they occur within an organizational network and utilize authorized access, insider attacks can be difficult to detect.
Examples: Theft of Intellectual Property, Manipulation of the records, Spying.
External Attacks
External attacks are attacks that originate from external sources. Such attacks occur when the information security policies and procedures are compromised. Attackers from outside the organization attempt to gain unauthorized access to the organization’s computing devices, networks, and informational assets. External attacks are often conducted by cybercriminals who target protected information of an organization by exploiting security vulnerabilities or using other social engineering tools & techniques.
Examples: SQL attack, Identity theft, Phishing/Spoofing, Denial of Service Attack.
Examples of Cybercrimes
- Theft of Intellectual Property: Intellectual property theft involves the stealing or unauthorized usage of any unique idea or crucial information such as copyrights and trade secrets from any individual or organization.
- Manipulation of Data: It is a type of fraud that involves secret modification of organizational data to gain advantages. Attackers can intentionally tamper with the data of the organization to damage a company’s reputation or commit crimes.
- SQL-Injection Attack: This attack involves the insertion of a malicious SQL query through the input data into an application database or URL, which allows the attacker to read and modify the database content illegally.
- Brute-force Attack: Attackers perform this attack to crack the login credentials or encryption keys of the target user to gain unauthorized access using the trial-and-error method.
- Phishing/Spoofing: Phishing attacks involve attempts to steal sensitive information, whereas spoofing involves identity theft. In a phishing attack, an attacker sends malicious links via email/messages to lure target users to click on them and steal the required information. However, spoofing attacks involve attackers that mimic trusted attackers to gain trust and install malware for malicious activities.
- Cyber Defamation: This involves publishing false statements against a target individual using the Internet or cyberspace to disgrace his or her reputation.
Cyber Attribution
Cyber Attribution is a process of technical methods for discovering and tracing individuals or groups responsible for cyberattacks. Organizations conduct investigations to attribute cyberattacks to attackers and obtain a complete procedural report of attack to bring them to the front of justice. These cyber attributes are frequently assessed under the guidance of official investigators appointed by relevant law enforcement agencies.
Cyber Attribution Techniques
Investigators use different cyber attribution techniques; some are as follows.
- Various forensic analysis and recovery tools, programming scripts, and applications have been used to obtain relevant and important information regarding cyberattacks. This may include programming language, libraries, time of execution, attack methods used, and appropriate tools.
- Analyze information such as metadata, origin of attack IP address, emails, servers used, domain registration, and other data from third-party sources. However, this information can be fake or impersonated by an attacker.
- Examine the attack methods, social engineering techniques and procedures to identify attackers.
- Threat intelligence is used to collect and analyze data related to various cyberattacks and attribute cyberattacks to known threat groups.
- Understand past attacks to analyze the behavior of threat actors and build threat-actor profiles for attribution.
- Understand the attacker’s motives, such as spying, server compromise, and breach of organization sensitive data.
Challenges of Cyber Attribution
During the investigation of cyberattacks for cyber attribution, investigators face many challenges in obtaining the most accurate information about both the attack and attacker. Some of the challenges faced by organizations are as follows:
- Unavailability of proper resources and expertise to find cybercriminals, leading to hiring third-party forensic experts for investigation.
- Sometimes, it becomes difficult to determine the attackers by analyzing digital evidence, attack objectives, and motives, as attackers do not carry out attacks from their own house and devices.
- Tracing attackers becomes challenging because they are using sophisticated techniques such as IP address spoofing, proxy servers, and Tor protocols. These techniques frequently change attacker’s IP address and mask their online activities to avoid traditional detection mechanisms.
- Different countries have their own legal enforcement and jurisdictional limitations. This limits the investigation of cross-border cyberattacks.
- Attacks originated from some countries may not always cooperate with investigators for investigations.
Cyber Crime Investigation

Cybercrime investigation is the process of examining a digital crime, its impact, and other details to identify the sources and perpetrators of the attack and prove their guilt. It involves the collection of clues and forensic evidence, analysis of the evidence, reconstruction of the incident, and presentation of the evidence in a manner admissible by the court of law.
Because the crime is digital, at least one electronic device relevant to the crime will be found during the investigation; the device may be a laptop, computer, mobile device, printer, or IoT device. Skilled investigators should analyze such devices with care, as they may have critical importance for the investigation and reveal valuable evidence to help resolve cases. Therefore, the investigator must perform a forensic analysis of the information contained in the device and present it in a manner suitable to the court of law.
Understanding Digital Evidence and eDiscovery
Digital evidence is defined as “any information that is either stored or transmitted in a digital form”. Digital information can be gathered while examining digital storage media, monitoring the network traffic, or making duplicate copies of digital data found during forensics investigation.
Investigators should take care when gathering and extracting digital evidence because such evidence is fragile. This makes it difficult for forensic investigators to trace criminal activity. Investigators should be trained and skilled in extracting, handling, and analyzing such evidence. A forensic investigator can extract different types of digital evidence from digital devices, such as files, documents, emails, logs, images, videos, metadata, instant messages, and data from other types of digital and IoT devices.
Challenges of Digital Evidence
- Data preservation: Appropriate procedures must be followed to ensure that digital evidence is collected, preserved, and protected from tampering.
- Admissibility: Digital evidence must meet certain legal standards for admissibility in court. These include issues related to authenticity and relevance.
- Chain of custody: A documented chain of custody is essential to establish that evidence has been handled and maintained properly from collection to presentation in court.
- Privacy and consent: Obtaining digital evidence may involve consideration of privacy and consent, particularly when personal data are involved.
- Technical expertise: Analyzing digital evidence may require specialized technical knowledge such as computer forensics.
Types of Digital Evidence
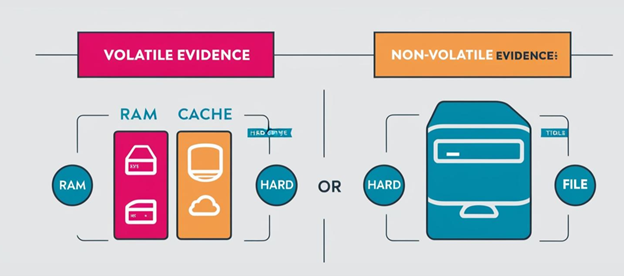
Volatile Data: Data that is lost as soon as the device is powered off.
Examples include system time, logged-on users, open files, network information, process information, process memory, clipboard contents, service information, command history, etc.
Non-volatile Data: Persistent data that is stored on secondary storage devices such as hard disks and memory cards.
Examples include hidden files, slack space, swap file, unallocated clusters, unused partitions, hidden partitions, registry settings, event logs, etc.
Characteristics of Digital Evidence
Before legal proceedings, evidence to be presented in court must comply with the five basic rules of evidence.
Admissible: Evidence must be related to the fact being proved.
Authentic: Evidence must be real and related to the incident in a proper manner.
Believable: Evidence must be clear and understandable by the judges and lawyers.
Complete: The evidence must prove the attacker’s actions or his innocence.
Reliable: There must be no doubt about the authenticity of the evidence.
Roles of Digital Evidence
Digital evidence plays an important role in the legal and investigative contexts. Some of the roles of digital evidence are as follows:
- Proof of an act: Digital evidence can be used to prove that a specific action has taken place, such as unauthorized access, malware injection, or data exfiltration.
- Linking evidence: Digital evidence links suspects to crime scenes, victims, or other suspects. For example, shared digital artifacts can link two devices that are part of the same cyberattack.
- Exculpatory evidence: evidence that can clear someone from blame. For example, digital records may show that an accused person is not active on their device at the time of an alleged crime happens.
- Lead information: Digital evidence can guide investigations. For example, a recovered deleted chat log may provide new leads or people of interest for an investigation.
- Timeline construction: System or application logs, metadata, and other timestamps can help investigators construct sequences of events or timelines.
Sources of Potential Evidence
User-Created Files
- Notes
- Database files
- Media (images, graphics, audio, video, etc.) files
- Documents (text, spreadsheet, presentation, etc.) files
- Internet bookmarks, favorites, etc.
Computer-Created Files
- Backup files
- Log files
- Configuration files
- Printer spool files
- Swap files
- System files
- History Files
- Temporary files
Best Evidence Rule
The best evidence rules state that the court only allows the original evidence of a document, photograph, or recording at trial and not a copy. However, the duplicate may be accepted as evidence provided that the court finds the party’s reasons for submitting the duplicate genuine.
For example, if the evidence is destroyed, lost, or inaccessible for some reason (e.g., the original being destroyed or being in possession of a third party), the court will be willing to accept a copy of the evidence if a witness can testify and confirm that the submitted copy is in fact an actual copy of the evidence.
Federal Rules of Evidence (United States)

Rule 101: Scope
Rule 102: Purpose
Rule 103: Rulings on Evidence
Rule 608: A Witness’s Character for Truthfulness or Untruthfulness
Rule 614: Court’s Calling or Examining a Witness
Rule 705: Disclosing the Facts or Data Underlying an Expert’s Opinion
Rule 901: Authenticating or Identifying Evidence
Rule 1002: Requirement of the Original
Rule 1003. Admissibility of Duplicates
Handling Digital Evidence
In forensic investigations, relevant digital data identified at a crime scene should be collected and preserved safely to maintain evidential integrity while being presented to a court of law. Investigators should forensically sound evidence gathering and preservation techniques to avoid the tampering with or destruction of electronically stored information.
Some best practices for forensic investigators to secure the handling of the electronic evidence are given below.
- Maintain a detailed record of every individual who has had access to that evidence.
- Document the date, time, purpose, and actions taken when evidence is accessed.
- Establish a digital log that records and tracks all events related to the evidence to maintain the chain of custody.
- Electronic evidence from Internet connections is isolated to prevent evidence erasure.
- Photographs of evidence collected from a crime scene. The location from where the evidence was obtained, and nearby areas should be visible during capture.
- Use forensically sound tools and techniques to acquire digital evidence.
- Conduct forensic investigations Imaging or cloning of electronic evidence images to keep the original evidence undamaged.
- Generate hash values for each device of electronic evidence during the collection and preservation phases to maintain the integrity and authenticity of the evidence.
- Capture photographs of the powered-on device screen to avoid the failure of relevant volatile evidence.
- Document each step in the process of identifying, collecting, and seizing electronic evidence at a digital crime scene.
- Power off the collected mobile devices, keep them uncharged, or put them in airplane mode to avoid wiping or overwriting the evidential data.
- Store original evidence in a secure location with restricted access to prevent tampering or destruction.
- Use writes blockers when accessing any electronic evidence to prevent accidental data writes.
- We used hashes (e.g., MD5, SHA-1, or SHA-256) to verify the integrity of the digital evidence. We ensure that the hash of the copied evidence matches that of the original evidence.
- Store and document these hash values for future reference (for court of law).
- The collected digital electronic devices were packed in appropriate evidence bags and labeled for unique identification.
- Store digital evidence in anti-static or faraday bags.
- Use secure methods, such as encryption, to protect sensitive data.
- Determine the appropriate method for returning digital evidence in line with organizational policies and legal requirements.
Roles and Responsibilities of Forensics Investigator
Using their skills and expertise, computer forensic investigators help organizations and law-enforcement agencies identify, investigate, and prosecute perpetrators of cybercrimes. Upon arrival at the scene, the investigator inspects the suspect’s devices, extracts and acquires evidentiary data and analyzes them using the right forensic tools to determine the root cause of the security incident.
- Recovers data of investigative value from computers/mobiles involved in crimes.
- Gathers evidence in a forensically sound manner.
- Ensures that the evidence is not damaged in any way.
- Creates an image of the original digital evidence without tampering with it to maintain the original digital evidence’s integrity.
- Reconstructs the damaged disks or other storage devices and uncovers the hidden information on the computer.
- Analyzes the evidence data.
- Prepares the analysis report.
- Updates the organization about various attack methods and data recovery techniques and maintains a record of them.
- Addresses the issue in a court of law.
What makes a Good Computer Forensics Investigator?
Forensic investigators should be familiar with all operating systems like Linux, MacOS, and Windows platforms. They should also develop and maintain contact with computing, networking, and investigative professionals.
- Interviewing skills to gather information about the case from client or victim, witnesses, and suspects.
- Researching skills to know the background activities pertaining to client or victim, witnesses, and suspects.
- Patience and the willingness to work long hours/days.
- Excellent writing skills to detail findings in the report.
- Strong analytical skills to find the evidence and link it to the suspect.
- Excellent communication skills to explain their findings to the audience or court of law.
- Be updated with new methods, techniques and forensic technology.
- Well versed in more than one computer platform (includes Windows, Macintosh, and Linux)
- Knowledge of various technologies, hardware, and software.
Understand Code of Ethics
Code of ethics are the principles stated to describe the expected behavior of an investigator while handling a case.
Computer forensic investigator should:
- Perform investigations based on well-known standard procedures.
- Examine the digital evidence carefully within the scope of the agreement.
- Ensure integrity of the digital evidence throughout the investigation process.
Computer forensic investigator should not:
- Refuse any digital evidence because that may cause failure in the case.
- Expose confidential matters without having any authorized permission.
- Present the training, credentials, or association membership in a wrong way.
Understand the Challenges Faced in Investigating Cybercrimes
Computer forensic investigators must identify, extract, preserve, and document digital evidence, which is a challenging task. However, other challenges and issues make the work of forensic investigators even more challenging.
- Increased data accessibility speed: Advancing technology and speed of accessing data have boosted confidence in cybercriminals to commit cybercrime.
- Anonymous identity: Cybercriminals can easily hide their identity from other entities or hide their IP addresses using proxies.
- Evolving tools and technologies: With the rise of various technologies and tools, cybercriminals are targeting organizations in different ways, making them more complex for investigators.
- Poor attribution: In addition to commonly used techniques, attackers use malware-infected systems or remote access techniques to maintain their anonymity, which further challenges investigators in identifying the perpetrator and the device that hosted the attack.
- Volatile nature of evidence: Most digital evidence, such as logs, records, and radio signals, can easily be lost because they are volatile. Special tools are required to quickly identify, gather, handle, interpret, and present volatile data as they may not be available for a long time.
- Evidence size and complexity: The diverse nature of digital devices results in an increased size and complexity of evidence data, making it more difficult to analyze and find appropriate information regarding the case.
Understand Legal Issues
- Digital evidence is fragile in nature, which makes it susceptible to changes during the investigation process rendering it inadmissible in the court of law.
- Legal system differs from one jurisdiction to the other, which makes the task of an investigator difficult as different legal systems have different rules for acquiring, preserving, investigating, and presenting the digital evidence in the court.
- Every legal system has a slightly different approach towards the issues related to authenticity, reliability, and completeness of digital evidence.
Understand Privacy Issues
- When retrieving evidence from a particular electronic device, investigators must be cautious to avoid charges against unlawful search and seizure, i.e., they need to be following the Fourth Amendment of the U.S. Constitution
- The Fourth Amendment states that government agents may not search or seize areas or things in which a person has a reasonable expectation of privacy without a search warrant.
- When dealing with evidence related to Internet usage, investigators must preserve other users’ anonymity while determining the identity of the few involved in illegal activities or crime.
Understand Various Standards and Best Practices Related to Computer Forensics
Computer forensic investigations must be conducted in accordance with international standards, procedures, and frameworks acceptable by the court of law. These standards and frameworks provide recommendations, guidelines, and best practices for the investigation.
This section outlines important standards and best practices that influence forensic computer investigation procedures.
ISO Standards
ISO/IEC 27000 Series
ISO/IEC 27000 is an information security standard developed and published by the International
Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It provides a global framework for effective information security management in all types of organizations.
ISO/IEC 27000:2018
ISO/IEC 27000:2018 is the latest revision and provides an overview of information technology, security techniques, information security management systems, and vocabulary.
ISO/IEC 27037
ISO/IEC 27037 is a standard for digital forensics that provides recommendations for specific activities in the process of handling digital evidence, such as the identification, collection, acquisition, and preservation of digital evidence, for maintaining the integrity of the evidential value and acceptability by the court of law.
ISO/IEC 27037:2012
ISO/IEC 27037:2012 provides guidelines for organizations in different situations that they may encounter during the process of handling digital evidence.
ISO/IEC 27041
ISO/IEC 27041 is a standard that deals with the investigation of information security incidents by ensuring that the methods and processes used in the investigation are “fit for purpose.” It also provides the best practices for defining requirements, describing methods, and implementing methods to satisfy these requirements.
ISO/IEC 27042
ISO/IEC 27042 provides guidelines for the interpretation and analysis of digital evidence to address issues of continuity, validity, reproducibility, and repeatability. It provides best practices for the selection, design, and implementation of analytical processes and guidance on appropriate mechanisms for demonstrating the proficiency and competence of the investigative team.
Understand Laws and Legal Compliance in Computer Forensics
Computer forensic investigations must be conducted according to the organization policy, applicable laws, and regulations of local jurisdictions. Legal compliance in computer forensics ensures that any digital evidence collected and analyzed is admissible in a court of law. This section outlines the role of local and international agencies during cybercrime investigations, along with important laws, regulations, and standards from across regions that might influence the forensic investigation procedure.
Computer Forensics and Legal Compliance
Forensic investigators should be aware of the legal implications of such activities. Investigators should comply with the security policies of the organization where the incident has occurred and act in accordance with applicable state laws and federal laws. Legal compliance ensures that any digital evidence collected and analyzed is admissible in a court of law.
reference
1. Ec-Council CHFI ebook

Informative article about daily life forensics.
Thank you for your feedback! 😊 We’re glad you found the article on daily life forensics informative. We aim to make forensic concepts relatable and easy to understand for everyone. Stay tuned for more practical insights and real-world examples!
Very Informative