Email Forensics
Understand Email Basics
Email is becoming the primary means of communication for an increasing number of businesses. Email-related criminal activity has increased in tandem with this growing reliance on email. The structure and operation of email networks, as well as the different parts that go into sending an email from the sender to the recipients, must therefore be thoroughly understood by forensic investigators.

Introduction to an Email System
- Email systems are based on a client-server architecture.
- An email system consists of servers that send and receive emails over a network as well as email clients that let users view and compose messages.
- The mail is sent from the client to a central server, which reroutes it to its intended destination.
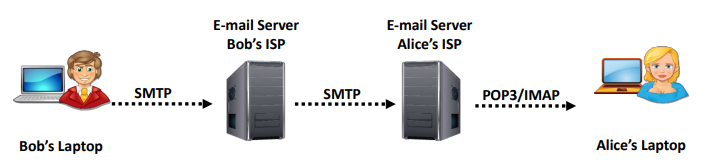
Components Involved in Email Communication
There are several components of email communication that play specific roles when an email message is transmitted from a sender to a recipient.
Email Clients/Mail User Agent
A computer application designed for organizing and accessing emails is called an email client, sometimes referred to as a mail user agent (MUA).
E-mail clients perform the following functions:
- Display all the messages in a user’s inbox. The message header usually displays the date, time, subject of the mail, sender of the mail, and the mail’s size.
- It also enables the user to create and send emails, select messages, and access the data contained within them.
- It also enables the user to attach files to messages and save attachments received in other messages.
The most popular email clients are:
- Standalone – such as Microsoft Outlook and Thunderbird
- Web-based – such as Gmail and Yahoo! Mail
Mail Transfer Agent (MTA) – A mail transfer agent (MTA) is an important component of the email transmission process. It is primarily a type of mail server that receives the email message from the mail submission agent and decrypts the header information to see where the message is going. Once determined, it passes on the message to the next MTA server. The SMTP protocol is used by all the MTA servers to communicate with one another. Some examples of MTA include Sendmail, Exim, and Postfix.
Email Server/Mail Delivery Agent
Multiple email clients are connected to and served by an email server. An email server functions as follows:
- There are multiple email accounts on an email server; normally, everyone has one account.
- The server maintains a text file for each account. All the messages for that account are contained in this text file.
- When a user clicks the send button in their email client, the client connects to the email server and sends the message along with all its supporting data, including the sender and recipient, to the server.
- The information is formatted by the server and appended to the bottom of the users.txt file that is received. The time, date of receipt, and subject line are also saved by the server in the txt file.
- The user must use the email client application to submit a request to the server to read the messages using email applications.
An e-mail server comprises of 3 components:
- POP3
- SMTP
- IMAP
SMTP Server
- The Internet protocol known as Simple Mail Transfer Protocol (SMTP) is used to send emails over IP networks.
- The SMTP servers listen on port 25 and manage all outgoing e-mails.
- When a user sends an e-mail, the sender’s host SMTP server interacts with the receiver’s host SMTP server.
- For instance, suppose a user with an account on myicc.com wishes to send an email to ram@rainy.com using a program like Microsoft Outlook.
This is how the process operates:
- When the user clicks on the Send button, Outlook establishes a connection with the server of myicc.com via port 25.
- The client provides the SMTP server with the sender’s address, recipient’s address, and body of the message.
- The SMTP server breaks the recipient’s address into the following parts:
- The recipient’s name (ram)
- The domain name (rainy.com)
- The SMTP server contacts the DNS (Domain Name Service) server and queries about the IP address of the SMTP server for rainy.com.
- The SMTP server from myicc.com connects to the SMTP server for rainy.com using port 25 and sends the message to it. The SMTP server at rainy.com receives the message and transfers it to the POP3 server.
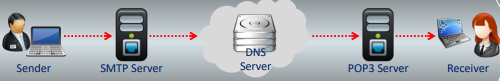
POP3 Server
Post Office Protocol version 3 (POP3) Server
- POP3 is an Internet protocol that is used to retrieve emails from a mail server.
- A POP3 server handles incoming mails.
- The server has one text file for each email account.
- The POP3 server acts as an intermediary between the e-mail client and the text file
- When a message arrives, the POP3 server appends that message to the bottom of the recipient’s text file, which can be retrieved by the e-mail client at any preferred time
- Email clients connect to POP3 servers via port 110.
- The POP3 downloads the emails to a single device (computer, tablet, smartphone, etc.) and then typically deletes them from the server.
- Drawback of POP3 is that the emails can be accessed only from one device
IMAP Server
- The Internet protocol known as Internet Message Access Protocol (IMAP) was created specifically for mail server email access.
- IMAP servers are like POP3 servers, as it manages all the incoming mails like POP3.
- An e-mail client connects to an IMAP server via port 143.
- Unlike POP3, this protocol keeps e-mails on the server even after the user has already downloaded them, thus enabling the user to use multiple devices to check the email.
- In IMAP, the user can also save the folders on the server and organize emails into folders.
How Email Communication Works?
When a user sends an email message to any recipient, it goes through several stages before reaching its recipient. A scenario is presented below to explain on these stages:
- Let us say that Ram, an email user, wishes to send Ramesh, another email user, a message. Using his email program, MUA (mail user agent), or web-based email service like gmail.com, he composes a message, enters Ramesh’s email address, and presses the send button.
- An MTA server receives the email message via SMTP, decrypts the header data, and looks up Ramesh’s email address’s domain name. By using this technique, the MTA server may identify the mail server that the message is intended for and forward it to the appropriate MTA.
- During the mail distribution process, an MTA server updates the header data of each message it receives. It is forwarded to the MDA upon reaching the final MTA, who retains the message in Ramesh’s mailbox.
- Ramesh’s MUA then retrieves the message using either POP3 or IMAP, and Ramesh is finally able to read the message.
Importance of Electronic Records Management
Electronic records management is the branch of management sciences, which is responsible for the efficient and systematic control over the process of creation, receipt, maintenance, use and disposal of electronic records, including the processes for capturing and maintaining digital evidence and data for legal, financial, administrative, and other business purposes.
Electronic records management is important for the following reasons:
- It makes electronic communications non-repudiable, meaning that no one can deny being the source of a certain communication.
- It acts as a deterrent for abusive and indecent contents in e-mail messages.
- It helps in the investigation and prosecution of e-mail crimes.
Understanding the Parts of an Email Message
An informal, short text message transmitted or received over a network is called an email. Emails are just plain text messages with the option to attach spreadsheets and image assets. Email messages can be sent to several recipients simultaneously.
Email messages comprise the following main sections:
Message Body
The message is communicated in the email’s body, which occasionally ends with a signature block. The header and body are separated by a blank line. The text or body of an email always follows the header lines.
The email’s body, which includes text, pictures, hyperlinks, and other information (like attachments), is its primary message. Separate attachments are shown in the email body, aligned with the text. There are no restrictions on the size of an email’s body imposed by the Internet email standard. Message sizes are limited by individual mail servers, though.
Attachments
Attachments are files sent along with an email message. They can be documents, images, audio, video, or any other type of files. Attachments are not technically part of the email’s body; they are encoded and transported with the email, then decoded upon receipt.
Signature
Provides information to the recipients about the identity or designation of the senders. Email programs can be set to enter this line automatically on all the emails sent.
Headers for Security
Headers such as SPF, DKIM, and DMARC records are used for authenticating the sender and ensuring the email message has not been tampered with during transit. These are critical for protecting against attacks such as spam and phishing.
Message headers
The message header includes the following fields:
- To specifies to whom the message is addressed. Note that the “To” header does not always contain the recipient’s address.
- Cc stands for “carbon copy.” This header specifies additional recipients beyond those listed in the “To” header. The difference between “To” and “Cc” is essentially connotative; some mailers also deal with them differently in generating replies.
- Bcc stands for “blind carbon copy.” This header sends copies of emails to people who might not want to receive replies or appear in the headers. Blind carbon copies are popular with spammers because they confuse many inexperienced users who receive an email that does not have their address or does not appear to be for them.
- From specifies the sender of the message.
- Reply-To specifies an address for sending replies. Though this header has many legitimate uses, it is also widely used by spammers to deflect criticism. Occasionally, a native spammer will solicit responses by email and use the “Reply-To” header to collect them, but more often, the address specified in junk email is either invalid or that of an innocent victim.
- Message-ID is a unique identifier assigned to each email for tracking.
- Sender is unusual in the email (“X-Sender” is usually used instead) but appears occasionally, especially in copies of Usenet posts. It should identify the sender; in the case of Usenet posts, it is a more reliable identifier than the “From” line.
- Subject is a completely free-form field specified by the sender to describe the subject of the message.
- Date specifies the date of creation and sending of the email. If the sender’s computer omits this header, a mail server or some other machine might conceivably add it, even along the route.
- MIME-Version is another MIME header that reflects the MIME protocol’s version.
- Priority is an essentially free-form header that assigns a priority to the mail. Most software ignores it. Spammers often use it to get their messages read.
- Received includes a log of each server through which the email passed.
- Content-Type specifies the format of the email (plain text, HTML, etc.).
- Attachments include a reference to any files attached to the email.
Introduction to Email Crime Investigation
Email crime investigation involves the extraction, acquisition, analysis, and revival of email messages related to any cybercrime. Investigators can obtain important information by carefully examining email communications, including the sender’s and recipient’s real IP addresses, the time and date of the message’s transmission, and the spoofing technique employed.
Investigators need to use many forensic tools to extract metadata from email headers. This helps them to track down the criminal responsible for the crime and report the results so that they can be prosecuted in court.

Investigations of criminal activities or violations of policies related to emails are like other kinds of computer crime investigations.
Types of Email Crimes
E-mail crime can be categorized in two ways:
- Crimes committed by sending e-mails
- Spamming
- Phishing
- Mail bombing
- Mail storms
- Crimes supported by e-mails
- Identity Fraud
- Cyber-stalking
- Child pornography
- Child abduction
Steps to Investigate E-mail Crimes and Violations
E-mail systems and chat applications allow criminals to perform various malicious activities. Under these circumstances, a criminal’s email and chat history may reveal their identify and serve as proof in the case of cybercrimes.
Steps involved in investigating e-mail crimes and violations:
- Obtain a Search Warrant
- Seizing the computer and email accounts
- Acquiring the email data
- Examining email messages
- Retrieving email headers
- Analyzing email headers
- Recovering deleted email messages
Step 1: Obtain a Search Warrant and Seize the Computer and E-mail Account
- A search warrant application should include the proper language to perform on-site examination of the suspect’s computer, and the e-mail server used to send the e-mails under investigation
- Seize all computers and e-mail accounts suspected to be involved in the crime
- Email accounts can be seized by just changing the existing password of the email account, either by asking the suspect his or her password or obtaining it from the mail server
Step 2: Seizing the Computer and Email Accounts
An investigator should apply for a search warrant in the proper language to examine the computer and email server on-site. Then, as specified in the warrant, they ought to do a forensics examination on the authorized tools. Seizing every computer and email account thought to be connected to crime is necessary. By changing the email account’s current password, the investigator can take control of the account. They can do this by asking the victim for their password or by getting it from the mail server.
If the victim is a business entity, the investigator should engage with the internal network and system administrators to comprehend their rules and follow their data safety regulations, as well as get approval from the relevant authorities.
Step 3: Acquiring the Email Data
The next step is to obtain the email data for forensic investigation after the computer and email accounts have been confiscated. The following conditions must be met to gather email data:
- The suspect has been accessing emails via desktop-based email clients such as Outlook and Mozilla Thunderbird.
- The suspect has a web-based email account that they accessed through a browser.
- The investigator needs to choose the acquisition process as per the situation at the crime scene.
Acquiring email data for forensic analysis is a sensitive and complex task that requires a balance between technical proficiency, legal knowledge, and ethical considerations. Properly acquired email data can provide crucial insights in various investigative scenarios, from cybersecurity incidents to legal disputes.
Acquiring Email Data from Desktop-based Email Clients
Many users prefer desktop-based email clients such as Microsoft Outlook, Mozilla Thunderbird, and Apple Mail to send/receive emails. When an email crime is suspected to have occurred on a user’s machine using email clients, the key sources of evidence are the local folders and archived files stored by these programs that hold information on all email activities. The job of the forensic investigator is to locate the local folders and extract all email messages using the right forensic tool and store the copies in a safe location.
Local email files/databases created by email clients can be saved in various locations on the suspect’s computer. The investigator needs to carefully identify all the local email files and acquire the relevant email messages related to the crime.
Local Email Files in Microsoft Outlook
When an email account is synced with the Microsoft Outlook desktop application, it creates a local copy of all the email folders in the following two formats:
- Personal Storage Table (pst): Generally, pop accounts store all the email information in a .pst file format in Outlook. The email messages, contacts, calendar, and other task data are automatically downloaded from the mail server and saved locally on the hard disk. In Outlook 2013 and earlier versions, the .pst files were used by IMAP accounts. However, in Outlook 2016, email messages of all IMAP accounts are saved in the .ost file format. The default location of .pst files in Outlook is C:\Users\%USERNAME%\Documents\Outlook Files
- Offline Storage Table (ost): Account types such as Outlook.com, Outlook for Office 365, Microsoft Exchange, and IMAP copy all mailbox components in the .ost file format. As emails, contacts, calendar, and other data are not taken off the server such as pop accounts, users can access their emails even when they do not have an Internet connection. All mailbox information is updated when the connection is revived. By default, the .ost file in Outlook is saved at the following location: C:\Users\%USERNAME%\AppData\Local\Microsoft\Outlook
Acquiring Thunderbird Local Email Files via SysTools MailPro+
As a forensic investigator, you can use tools such as SysTools MailPro+ to acquire local email file data as stored by Thunderbird.
SysTools MailPro+: It allows investigators to load email data from multiple email files, preview them in multiple modes, analyze them, and export them into several file formats. This tool offers general and Wildcard search options for in-depth searches. It can also load corrupted data files and recover deleted data from them during the analysis. This tool can process most of the data files created using most available email applications including Mozilla Thunderbird, Microsoft Outlook, Apple Mail, Microsoft Exchange Server, etc.
Additionally, using SysTools MailPro+ will help investigators to select one or more mbox files or specific local email folders for forensic acquisition and analysis.
Acquiring Outlook Email Files: .ost to .pst File Conversion
Converting .ost into .pst file formats offers the investigators an easy way to acquire the email data stored by the Outlook email client. You can use tools such as kernel for OST to PST for this purpose.
Kernel for OST to PST
Kernel for OST to PST can easily convert OST files to PST and other file formats such as PST, EML, MSG, Office 365, and Exchange Server. This tool saves OST files to different email servers, web-based email clients that include Office 365. It comes with filters that help in selecting specific items for migration.
Acquiring Email Data from Web-based Email Accounts
While investigating an email crime, the first step for a forensic investigator is to acquire email data for performing forensic analysis. However, the forensic investigator needs to have the suspect’s credentials to be able to acquire email data from web-based email accounts. The investigator can use the following methods to acquire the email evidence for investigation:
- Use Google Takeout to generate an offline archive of the suspect’s Gmail account in the mbox file format.
- Synchronize the specific web-based email account with email clients such as Outlook or Thunderbird to generate local copies of the email data and acquire them with forensic tools. This process uses POP3/IMAP synchronization. It is important for a forensic investigator to ensure that the integrity of the data is not altered during or after synchronization with the email client.
Step 4: Examine E-mail Messages
- Once the email crime has been approved, detectives need proof to establish the crime and pinpoint the perpetrator.
- To gather evidence, detectives must have access to the victim’s computer so they may examine the email they received.
- The original data should not be analysed, as is the case with all forensic investigations. Therefore, before doing analysis, the investigator should take a picture of the victim’s PC.
- Then, the investigator should physically access the victim’s computer and use the same e-mail program the victim used to read the e-mail.
- If required, the investigator can get the username and password from the victim and logon to the e-mail server.
- If physical access to a victim’s computer is not feasible, the investigator should instruct the victim to open and print a copy of an offending message, including the header.
- The header of the e-mail message has a key role in tracing the e-mail, because it contains the unique IP address of the server that sent the message.
- Forensic investigators should closely examine the following areas while inspecting the acquired email messages:
- Subject: This field of an email informs the recipient about the message that the email intends to convey. Most of the spoofed emails are designed to create a sense of panic/urgency that induces the victim to open the mail and go through its contents.
- Sender Email Address: Attackers trick target users by making suspicious emails appear authentic. For example, an email appearing in the name of a bank, but which uses a Gmail account instead of the respective bank’s domain, is a strong indicator of spoofing.
- Email Body: The email body contains the main message of the email. A spoofed email body might include direct links/hyperlinks that lure users to provide sensitive details. The body of a spoofed email often has poorly structured language/sentences that do not appear professional.
- Email Attachment: Attackers usually send documents, PDFs, or image copies with extensions such as .exe, .vbs, .js, .wsf, and .zip as attachments in emails. These attachments are designed to execute hidden programs such as spyware and malware on the user’s computing system, which can compromise sensitive data.
Examining Email Logs
- It is important to confirm and validate the email addresses, sources, and paths associated with the suspicious emails in forensic investigations pertaining to emails.
- It is important to examine logs to figure out if the e-mail header has been tampered after the suspected incident
Examining System Logs
- By examining system logs, an investigator can verify the path that email has taken
Examining Network Equipment Logs
- By examining the router and firewall logs, it is possible for an Investigator to verify the times, and the IP addresses contained within the e-mail
- These logs provide e-mail message ID information, source address and destination address of the servers used to send the e-mail
Examining Microsoft Exchange E-mail Server Logs
- Microsoft Exchange uses the Microsoft Extensible Storage Engine (ESE)
- It uses Messaging Application Programming Interface (MAPI), which allows collaboration of various e-mail applications
- While investigating an e-mail sent via Microsoft Exchange server, an investigator should primarily focus on the following files:
- .edb database files (responsible for MAPI information)
- .stm database files (responsible for non-MAPI information)
- checkpoint files
- temporary files
- Checkpoint files help to find out if any data loss occurred after last backup, thus allowing the investigator to recover lost or deleted messages.
- Temporary files store the information received by the server when it was too busy to process it immediately. System retains these files that may be recovered for investigation purposes.
- Transaction log preserves and processes modifications done in the database file, so that it can be used to determine if the email has been sent or received by the server.
- Windows Event Viewer can be used to read:
- Tracking log (allows to view message content associated with the e-mail)
- Troubleshooting or diagnostic logs (records several events for each e-mail sent or received). In addition, Event Properties dialog box provides more information in forensic investigations
Step 5: Retrieving Email Headers
An essential part of an email that can assist investigators in determining the email’s origin is its header. These email headers include details about the sender and the recipient. The headers “From” and “To,” respectively, are used to communicate these facts about the sender and the recipient or recipients.
Once email communication has been acquired, investigators can recover its header information. If they have direct access to the suspect’s computer, they can view the emails using the same email application that the suspect uses. Every email program has a different process for recovering email headers.
Viewing the E-mail Headers in Microsoft Outlook.com
- Open Microsoft Outlook.com and log in. To view the headers for a received email, click on it. Then, use the Reply all drop-down menu to access the View message source option.
- Copy and paste the message header text in any text editor after selecting it from the message source box, then save the file.
Viewing the E-mail Headers in Apple Mail
- Open Apple Mail, then choose the received email that you want to view headers for.
- Select the text in the message headers, copy and paste it into any text editor, then save the file by going to View à Message à All Headers.
Viewing the E-mail Headers in Gmail
- Log on to Gmail. Click on the received mail for which you would like to see headers
- Click on the Reply drop-down button and navigate to the Show original option
- Select message headers text, copy and paste the text in any text editor and save the file.
Viewing the E-mail Headers in Yahoo Mail
- Log on to Yahoo Mail. Select the received email for which you would like to see headers
- Click on the …More drop-down button and navigate to the View Full Header option
- Select message headers text, copy and paste the text in any text editor and save the file.
Step 6: Analyzing E-mail Headers
Analyzing email headers is a crucial aspect of email crime investigations, as they store email metadata and other information. Investigators can analyze the following details in the email headers:
- Timestamp: This reflects the date and time when an email was sent
- From: This header reflects the sender’s email ID as seen at the recipient’s end. The “From” header can be forged in the case of spam emails.
- To: This header displays the recipient’s email ID
- Message ID: Each email message has a unique ID associated with it. No two emails, even in the same email chain, can have the same Message ID. These Message IDs are generated by the globally unique MTA/mail server of the sending mail system. The globally unique Message ID of an email message is an indicator of its authenticity. The part before the “@” in a Message ID denotes the timestamp associated with that email message. The part of the Message ID after “@” denotes the fully qualified domain name (FQDN), which reflects the domain name of any host that marks its unique presence online.
- Subject: This header displays the subject as provided by the sender
- MIME: Multi-Purpose Internet Mail Extension (MIME) allows email users to send media files such as audio, video, and images as a part of the email message
Examples of MIME Headers
MIME-Version: This header shows that the message is MIME formatted. By default, this header is set to a value of 1.0.
Content-Type: This header specifies the content type and sub-type in a message such as the following:
- Text/plain shows the type of message
- Audio/mp3, image/jpeg, video/mp4, respectively, represent email messages containing audio files, image files, and video files
- Multipart/signature shows that an email message has a signature
- Multipart/mixed indicates that an email has text along with attachments
Content Disposition: This header specifies how a message, or its body part, must be presented.
Content-Transfer Encoding: This header represents the encoding contained in the message.
Content Description: This is an optional MIME header used to provide additional information pertaining to the content of an email message.
Checking the E-mail Validity
- Email Dossier is a scanning tool that the investigator can use to verify the legitimacy of an email address.
- It provides information about e-mail address, including the mail exchange records.
- This tool initiates SMTP sessions to check address acceptance, but it never actually sends e-mail.
Other tools to check e-mail validity:
Email Address Verifier – https://tools.verifyemailaddress.io
Email Checker – http://email-checker.net
Examine the Originating IP Address
The following steps are involved in examining the originating IP address of an e-mail:
- Collect the IP address of the sender from the header of the received mail
- Search for the IP in the WHOIS database
- Look for the geographic address of the sender in the WHOIS database.
Trace the E-mail Origin
- Tracing the origin of an e-mail begins with looking at the message header
- All e-mail header information can be faked, except the “Received” portion referencing the victim’s computer (the last received)
- Once it is confirmed that the header information is correct, the investigator can use the originating e-mail server as the primary source.
Validating Header Information
- Once it is established that a crime has been committed, the investigator can use the IP address of the originating source to track down the owner of the e-mail address.
- The following are some acceptable sites that an investigator can use to find the person owning a domain name:
Tracing Back Web-based E-mail
- Web-based e-mail services (such as Gmail, Outlook etc.) can often make it complicated to trace the sender.
- A user can read and send this type of e-mail from any computer and from any part of the world.
- Web-based e-mail accounts are free, and no authentic information is required for creating an e-mail account.
- Criminals exploit this advantage and create e-mail accounts using false identities.
- In case a Web-based e-mail account is used for sending offending messages, the investigator can contact the provider of the account to find the IP address of the user who connected to the Web site to send the mail.
- After performing IP address authentication, the investigator can get the sender’s information.
- Received Headers: The Received header contains details of all the mail servers through which an email message travels while in transit. These headers are generated every time an email transmits through a mail server/MTA on its route to the recipient. Whenever any SMTP server receives an email message, a Received header is added to the email. Therefore, investigators need to start examining the Received header, as it reflects information about the sender’s mail server. Then, they can proceed with other data about the mail server and IP address associated with the recipient. The Received header is showing the domain name from which the email message originated, the associated IP address, and the date and time in PDT.
- Return-Path: This header is used to specify the email address to which an email message will be sent/returned if it fails to reach the intended recipient. When an email fails to reach the intended recipient, it bounces. That is, it is returned to the sender of the email, unless the sender specifies a different email address where bounced emails should be sent. If the return path address and the sender’s email address differ, it is an indicator of spamming/spoofing.
- Received-SPF: The sender policy framework (SPF) prevents sender address forgery. SPF allows organizations to designate servers that can send emails on behalf of their domains. The framework implements an SPF record, which refers to a DNS record added to the DNS zone of an organization’s domain. Within the SPF record, an organization can define the host names and/or IP addresses that are authorized to send emails from their domain. Through the implementation of SPF, the results for email exchanges can be as follows:
- Received-SPF: None: This means that no SPF record was found for the domain.
- Received-SPF: Neutral: This means that the sender’s IP address is neither authorized
- nor restricted from sending emails on behalf of the organization’s domain. A neutral result is treated in the same manner as a “None” result.
- Received-SPF: Pass: This means that the sender’s IP address is authorized to send emails from the domain.
- Received-SPF – fail, or hard fail: This means that the email was rejected by the recipient’s mail exchanger because the sender’s IP address is not authorized to send emails from the domain. The SPF hard fail is executed by adding an “-all” mechanism to an SPF record.
- Example: v=spf1 ip4: 207.84.200.37 -all
In the above example, “-all” means that the senders that are not listed in the mentioned DNS record should be treated as unauthorized and emails from them should be rejected. Only the IP address 207.84.200.37 is authorized to send emails.
- Received-SPF: Softfail: This means that there is a possibility that IP addresses might or might not have the authorization to send emails on behalf of the mentioned domain.
- Example: v=spf1 include: modprod.outlook.com ~all
11. DomainKeys Identified Mail (DKIM) Signature: It refers to an email authentication method that helps safeguard the senders and recipients of emails from phishing, spoofing, and spamming. The technique verifies that the email message received by the receiver has been sent from a legitimate mail server. This method of email authentication uses public key cryptography to detect and prevent the delivery of malicious emails. This digital signature is secured through encryption. DKIM also ensures that emails and their contents are not altered while in transit between the sender’s and the recipient’s servers. Most email service providers look for DKIM signatures in emails.
Step 7: Recovering Deleted Email Messages
The process of recovering a deleted email message differs based on the email client used to send the email:
Recovering Deleted Email Messages from Outlook PST
In Outlook, email messages, once deleted, are moved to the “Deleted Items” folder. The deleted emails are stored in the “Deleted Items” folder for 14 days (a default retention period that can be modified), after which the messages are automatically deleted from that folder. If these deleted emails are also removed from this folder, they become invisible to the user. However, they are not entirely deleted but moved to the unallocated space of the drive. The deleted email messages can be recovered if that unallocated space is not replaced with new data. These emails can be recovered with forensic tools such as Autopsy and Paraben’s Electronic Evidence Examiner (E3), if it has not been already overwritten.
Recovering Deleted Emails from Gmail and Outlook
Gmail
When an email is deleted in Gmail, it is tagged for deletion and moved to the Trash folder instead of being completely removed. These messages reside in the Trash folder until the user or service provider clears it.
Recovering deleted emails in Gmail:
- Log in to Gmail
- In the left pane, scroll down and find the Trash
Note: Expand the More drop-down list in the left pane if you do not find the Trash folder directly by scrolling down.
- Click on the Trash folder to view a list of deleted emails in the right windowpane.
- Select the deleted email you want to recover and click on the Move icon in the email toolbar.
- Select the location where you want to move this deleted email.
Outlook PST
Outlook stores emails, contacts, and calendar entries in the form of a personal storage table (PST). In MS Outlook, data deletion occurs in two categories:
- Soft deletion. When a user deletes emails from folders such as Inbox, Drafts, Sent Items, and Contacts, Outlook moves them to the Deleted Items
- Hard deletion. When a user deletes emails using Shift+Delete, Outlook deletes them permanently from the mailbox.
Recovering deleted emails in Outlook:
Investigators can recover deleted emails as follows:
- Log in to MS Outlook and open the Deleted Items
Note: If you cannot find the Deleted Items folder, it means that your account does not support the recovery function.
- The folder contains recently deleted items.
- Then, in the HOME tab, click on Recover Deleted Items from Server.
- The Recover Deleted Items window appears.
- Click on the email that you want to recover and select the Restore Selected Items radio button.
- Then, click
- Now, navigate back to the Deleted Items folder, where you will find the recovered email
U.S. Laws Against Email Crime: CAN-SPAM Act
The CAN-SPAM Act (Controlling the Assault of Non-Solicited Pornography and Marketing Act) is a law that sets the rules for sending e-mails for commercial purposes, establishes the minimum requirements for commercial messaging, gives the recipients of e-mails the right to ask the senders to stop e-mailing them, and spells out the penalties in case the above said rules are violated.
CAN-SPAM’s main requirements meant for senders:
- Do not use false or misleading header information
- Do not use deceptive subject lines
- The commercial e-mail must be identified as an ad
- The email must have your valid physical postal address
- The email must contain the necessary information regarding how to stop receiving e-mails from the sender in future
- Honor recipients opt-out request within 10 business days
- Both the company whose product is promoted in the message and the e-mailer hired on contract to send messages must comply with the law
Penalties:
All e-mails that are in violation of law are subject to financial penalties of up to $16,000, and depending on the case one or more persons may be held responsible for the violations.
For example, in case of violation of law by e-mails sent for the promotion of commercial products and services, both the company whose product is being promoted in the message and the company that originally sent the message may be held legally responsible
As per the CAN-SPAM Act, there are certain specified violations that may involve additional fines. Criminal penalties and imprisonment may be sentenced for:
- Accessing someone else’s computer to send spam mails without permission
- Using false information to register for multiple email accounts or domain names
- Relaying or retransmitting multiple spam messages through a computer to mislead others, about the origin of the message
- Harvesting email addresses or generating them through a dictionary attack (the practice of sending emails to addresses made up of random letters and numbers in the hope of reaching valid ones)
- Taking advantage of open relays or open proxies without permission
