Case Studies
Explore our confidential case studies where Xpert Forensics uncovered digital fraud, insider threats, data leaks, and cyber misconduct using advanced forensic tools and investigative techniques. Each case reflects our commitment to precision, discretion, and delivering actionable insights that drive resolution.
Window Forensics: Imaging, Processing and Analysis Using Magnet Axiom
This article explores the powerful capabilities of Magnet AXIOM in conducting a complete Windows forensic investigation — from forensic imaging and evidence acquisition to advanced digital evidence processing and deep data analysis. Using a sample .E01 forensic image, we demonstrate how Magnet AXIOM identifies and lists multiple partitions, including system, restore, and user-defined volumes, offering granular control over the data to be processed.
With its advanced artifact parsing, keyword searching, and reporting features, Magnet AXIOM simplifies computer forensics and helps investigators uncover critical insights in complex cases. Whether you are handling cyber forensics investigations, data recovery in Windows environments, or comparing tools like FTK vs Magnet AXIOM, this guide highlights why Magnet AXIOM is one of the most effective digital forensics tools for professionals worldwide.
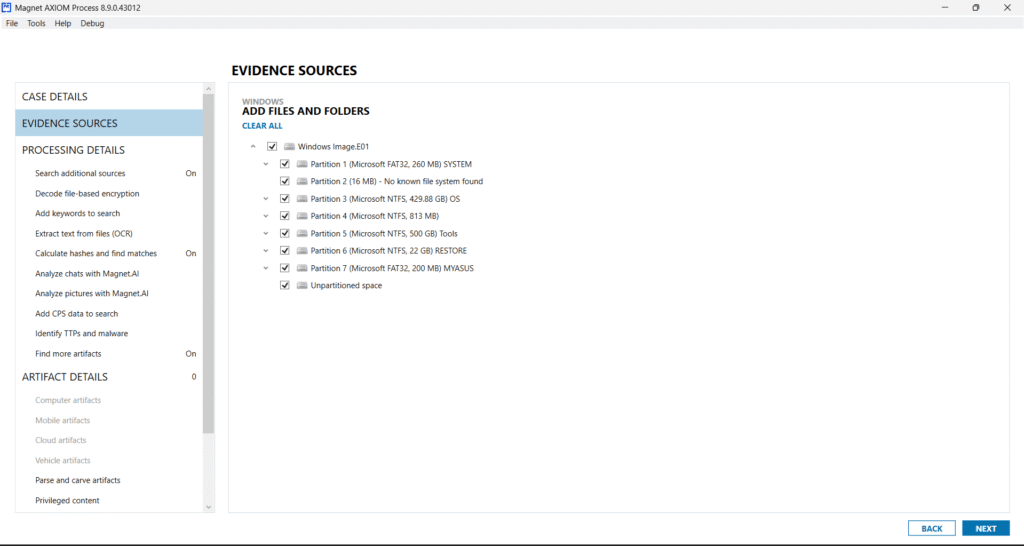
The screenshot showcases the Evidence Sources screen, where an investigator selects partitions from a Windows image file. The tool automatically detects filesystem types like FAT32 and NTFS and categorizes them accordingly – e.g., SYSTEM, Tools, RESTORE, and MYASUS. Users can selectively include partitions based on relevance, optimizing processing time and efficiency
In the digital forensics field, analyzing a Windows system requires not just acquiring data but understanding it in its full context – down to deleted files, system metadata, and shadow copies. Magnet AXIOM enables forensic investigators to carry out a detailed end-to-end workflow involving image acquisition, targeted processing, and intelligent analysis of every partition on a Windows system.
Acquiring and Loading Forensic Images
Using a forensic image file (.E01), Magnet AXIOM automatically detects all partitions and volumes, including:
- System Reserved Partitions
- Primary OS Volumes
- Restore and Tools Partitions
- Recovery Environments
- OEM or Manufacturer Partitions
- Unpartitioned Space
The tool offers a user-friendly interface where each partition can be toggled for inclusion in the case, ensuring efficiency and relevance in evidence processing.
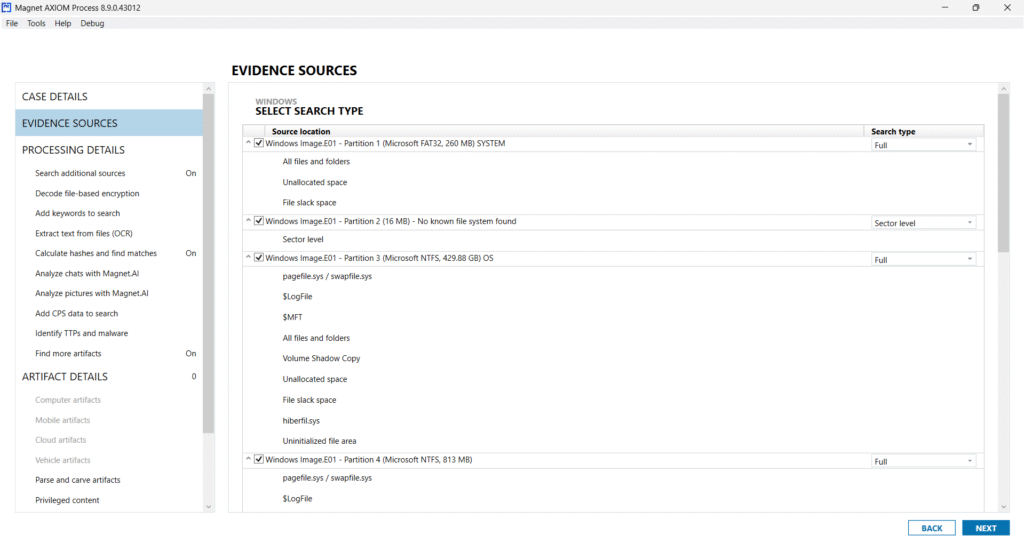
Advanced Search Type Configuration
Screenshots reveal AXIOM’s powerful partition-level control, where forensic analysts can set search scopes per partition. Search types include:
- Full Scan
- Sector-Level Search
- Volume Shadow Copy
- File Slack Space
- Unallocated Space
- System Metadata Artifacts (MFT, $LogFile, $Recycle.Bin)
- Pagefile, hiberfil.sys, and Event Logs
Computer artifacts
Once the evidence source and partition-level search configurations are complete, Magnet AXIOM moves into one of its most powerful phases: Artifact Selection. This allows forensic analysts to define exactly which types of digital evidence (artifacts) they want to extract and analyze from the loaded image.
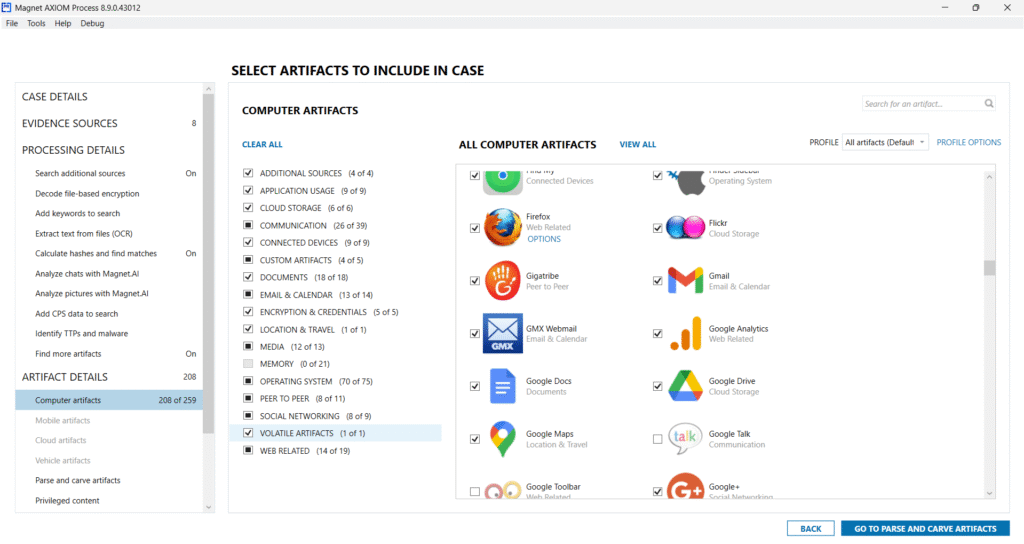
The screenshot showcases the Computer Artifacts interface, where AXIOM categorizes evidence sources under themes such as:
- Application Usage
- Operating System Artifacts
- Communication
- Cloud Storage
- Credential Data
- Web-Related Activity
- Media Files
- Memory Artifacts
- Peer-to-Peer Transfers
- Volatile Data
Parse & Carve artifacts
After selecting the relevant computer artifacts, Magnet AXIOM moves to the Parsing and Carving phase, where it begins actual data extraction from the selected partitions and filesystems.
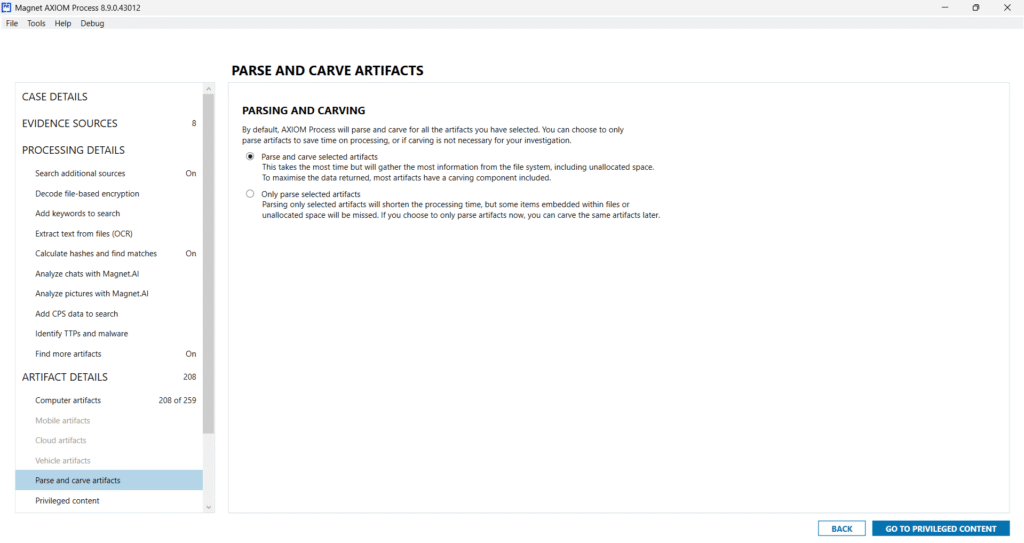
This interface gives forensic analysts control over how AXIOM should proceed with the data recovery process:
Options Available:
- Parse selected artifacts only: This is the fastest method, focusing solely on user-selected artifacts (e.g., browser history, chat messages, login credentials).
- Parse and carve for all artifacts: A more comprehensive method where AXIOM scans for both existing and deleted evidence types – even from unallocated or partially overwritten areas.
This screenshot shows the final and critical phase of the forensic workflow in Magnet AXIOM — the “Analyze Evidence” stage.
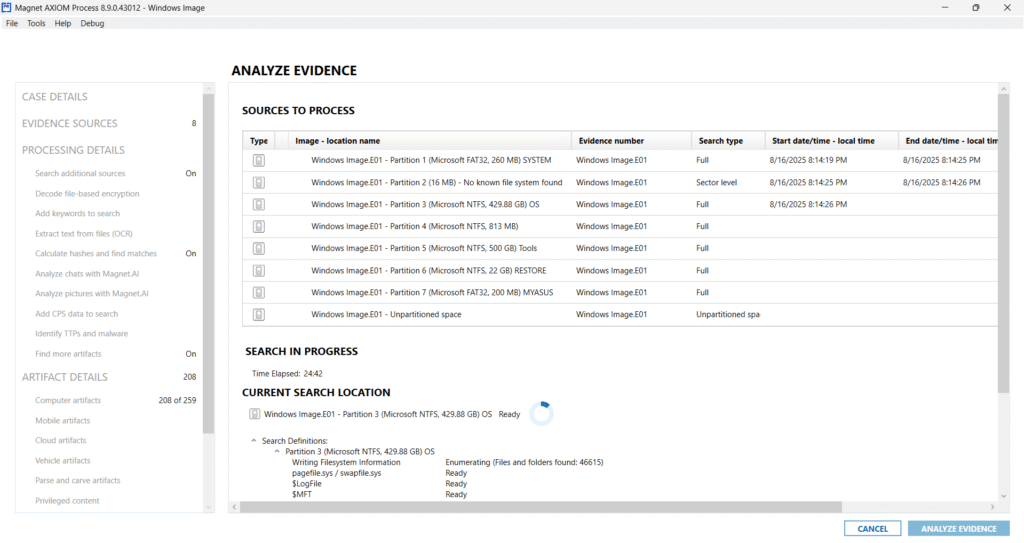
With partitions selected, artifacts defined, and carving rules applied, Magnet AXIOM proceeds to the Analyze Evidence phase — where the actual forensic search is executed, scanning through every selected data source to extract digital artifacts and reconstruct events.
Once all selected partitions have been processed and artifacts parsed and carved, Magnet AXIOM provides a concise summary of the search results, marking the end of the evidence analysis phase.
Search Completion Summary:
- Start Time: Shows when AXIOM began processing.
- End Time: Marks when the analysis concluded.
- Total Duration: Full time taken — in this case, over 6 hours of intensive forensic processing.
- Search Status: Displays as “Completed”.
- Notes & Exceptions: AXIOM flags any anomalies, errors, or skipped files (e.g., encrypted files or corrupted sectors), helping the examiner take corrective action or note them in reports.
Analyzing Extracted Evidence in Magnet AXIOM Examine
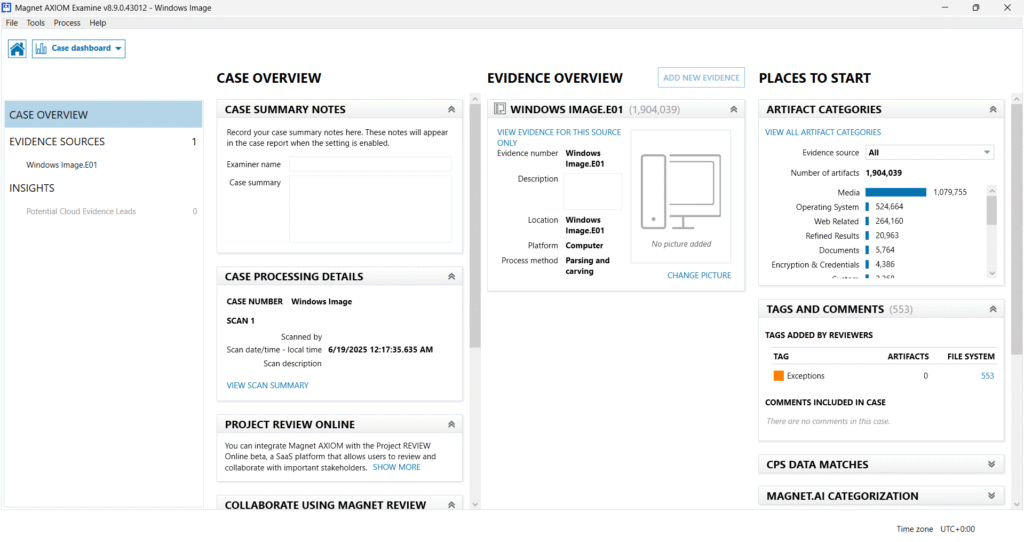
The Case Dashboard provides a centralized view of:
- Evidence summary and metadata (E01 image name, scan timestamp, scan method used)
- Artifact count: This case produced 1,904,039 artifacts.
AXIOM helps the examiner prioritize analysis using:
Artifact Categories: Organize evidence by type (media, OS, documents, credentials, etc.)
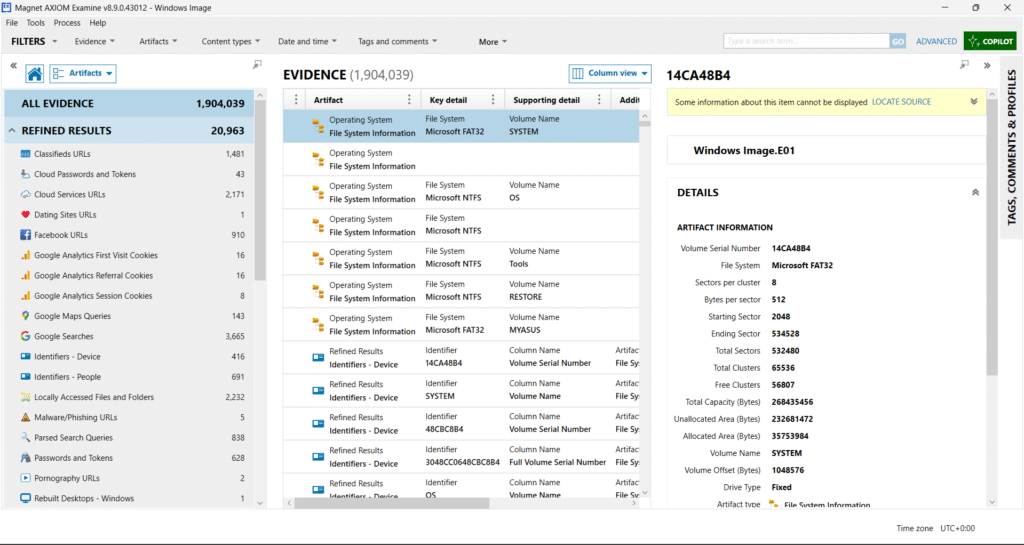
In the screenshot above, we can see that the forensic image (Windows Image.E01) has been successfully loaded and processed inside the forensic tool. At this stage, all evidence artifacts are listed — including file system details, refined results like social media URLs, search queries, passwords, and device identifiers. This initial parsing is important because it gives the investigator a broad overview of what is contained in the evidence.
However, when the evidence size is huge (as shown here with over 1.9 million artifacts), manually reviewing each entry is not practical. This is where keyword searching becomes the next crucial step.
Moving to Keyword Searching
After loading and categorizing the data, investigators proceed to keyword searching to filter through the massive evidence set and uncover items that are most relevant to the investigation.
Here’s how the process works:
- Identify What to Search For
Based on the case type, the investigator creates a list of targeted words or phrases.- In a financial fraud case: words like “transfer,” “bank,” “PIN,” or “account.”
- In a corporate investigation: “confidential,” “leak,” “password.”
- In cybercrime cases: email addresses, usernames, or even malware file names.
- Apply the Keywords Across the Evidence
The forensic tool scans through:- Documents, spreadsheets, and databases.
- Internet artifacts like search history, cookies, or social media activity.
- Deleted or unallocated space, which may still hold valuable traces of evidence.
- Analyze the Keyword Hits
Each keyword hit is displayed with its context, showing the file or artifact where it was found. This allows the examiner to quickly validate whether the result is relevant. - Tag, Bookmark, and Report
Relevant hits can then be tagged and organized for reporting. This ensures that when presenting findings in court or to stakeholders, the evidence is clear, focused, and directly tied to the investigation.
Why This Step Is Important
Without keyword searching, investigators would have to manually navigate through millions of artifacts, which is time-consuming and inefficient. By jumping from the broad evidence overview (as shown in the image) directly into targeted keyword searches, investigators can quickly move from “everything” to “exactly what matters.”
How Magnet AXIOM Makes Evidence Discovery Easier for Investigators – And How Xpert Forensics Can Help
In today’s digital investigations, one of the biggest challenges is the sheer volume and complexity of data. Modern devices contain millions of files, hidden artifacts, deleted records, and encrypted data. For investigators, manually sorting through this information is nearly impossible. This is where Magnet AXIOM, a leading digital forensics platform, changes the game.
How Magnet AXIOM Simplifies Investigations
- Unified Evidence Processing: Magnet AXIOM allows investigators to acquire and analyze data from multiple sources in one platform: computers, mobile devices, cloud storage, and IoT systems. Instead of using separate tools, examiners can process everything in a single interface.
- Powerful Artifact Parsing: The software automatically extracts and organizes digital artifacts such as:
- Chats and social media messages.
- Call records and contact lists.
- Browser history, cookies, and saved credentials.
- Deleted or hidden files.
This saves countless hours by turning raw technical data into human-readable evidence.
- Keyword and Filter Searches: With advanced keyword search and filtering options, investigators can quickly move from millions of artifacts to the exact pieces of evidence relevant to a case. Whether it’s a password, a suspicious URL, or a financial keyword, AXIOM makes it easy to pinpoint results.
- Visualization Tools: Investigators can use Magnet AXIOM’s timeline, chat thread, and connection graphs to visualize how events unfolded. This makes complex digital activity easier to understand and present in court.
- Court-Ready Reporting: AXIOM automatically generates clear, detailed, and customizable reports. These reports make it simple to share findings with law enforcement, legal teams, or corporate stakeholders.
How Xpert Forensics Adds Value
At Xpert Forensics, we combine the power of Magnet AXIOM with our expertise and investigative experience to deliver actionable results for clients.
- Case-Specific Approach: We don’t just rely on the software. We interpret results in the context of your case, whether it involves fraud, insider threats, financial crimes, or cyber investigations.
- Comprehensive Services: From mobile forensics and computer forensics to cloud investigations and malware analysis, we provide a complete end-to-end investigation service.
- Clear Reporting: We transform complex technical findings into easy-to-understand reports, so decision-makers can act quickly and confidently.

Excellent read! The section on keyword searching and evidence partitioning is very well presented. This will definitely help investigators save time during casework.
Thank you so much for your kind words! 😊 We’re glad to know you found the section on keyword searching and evidence partitioning helpful. At Xpert Forensics, we aim to create content that provides practical tips and techniques to help investigators work more efficiently and save time during casework. Stay tuned for more insights and best practices in digital forensics!
As a student learning digital forensics, this article gave me clear insights into how professional tools like Magnet AXIOM are used in real cases. It’s both technical and easy to understand.
Thank you so much for your thoughtful feedback! 😊 We’re delighted to know that the article helped you gain clearer insights into how professional tools like Magnet AXIOM are used in real-world digital forensics cases. Our goal is to make technical concepts easier to understand while keeping the content practical and relevant for learners and professionals alike. Stay tuned for more detailed guides and case studies!
I liked how the article highlighted not just the tool, but also the investigator’s role in interpreting results. It shows the perfect balance of technology and expertise.
Thank you so much for your valuable feedback! 😊 We’re glad you enjoyed the article and appreciated the focus on both the tool and the investigator’s role in interpreting results. At Xpert Forensics, we believe the right balance of technology and expertise is essential for accurate and efficient investigations. Stay tuned for more insightful content!
This article is a great resource for training new investigators. It covers everything from imaging to reporting in a structured manner that’s easy to teach and apply.
Thank you so much for your thoughtful feedback! 😊 We’re glad to hear that you found the article useful for training new investigators. Our goal is to provide well-structured and practical resources that make learning and applying digital forensics concepts easier. Stay tuned — we’ll continue sharing more guides and tutorials to support investigators at every stage!
I enjoyed reading this article because it simplified such a complex process. Magnet AXIOM’s role in digital evidence analysis is clearly explained and backed with real examples.
Thank you so much for your wonderful feedback! 😊 We’re glad to hear that you found the article helpful and that our explanation of Magnet AXIOM’s role in digital evidence analysis was clear and easy to understand. We’ll continue sharing more practical insights and real-world examples to make complex forensic processes simpler for our readers. Stay tuned for more!