Case Studies
Explore our confidential case studies where Xpert Forensics uncovered digital fraud, insider threats, data leaks, and cyber misconduct using advanced forensic tools and investigative techniques. Each case reflects our commitment to precision, discretion, and delivering actionable insights that drive resolution.
Mobile Forensics (Android): Advanced Logical Extraction & Analysis with Cellebrite UFED
Introduction
In this case study, we delve into the practical application of Cellebrite UFED for Mobile Forensics (Android): Advanced Logical Extraction & Analysis. The objective was to retrieve essential digital evidence, including messages, call logs, media files, and app data, in a legally sound and forensically valid manner.
What Is Mobile Forensics?
Mobile forensics is a branch of digital forensics that involves the recovery, analysis, and presentation of data from mobile devices, typically for use in legal or investigative contexts. This includes smartphones, tablets, SIM cards, and memory cards.
When it comes to Android forensics, the challenge lies in dealing with multiple device manufacturers, security features, encryption, and ever-changing app ecosystems. Mobile forensics uses specialized tools and techniques to access both visible and hidden data without compromising the integrity of the evidence.
Why Logical Extraction?
Logical extraction refers to the method of accessing data using the device’s standard APIs and backup services—without altering the original data or requiring root access. It is ideal for situations where device integrity must be preserved and rooting is not allowed or possible.
Logical extraction retrieves:
Contacts, call logs, SMS/MMS
App data (e.g., WhatsApp, Instagram, Facebook, Telegram)
Photos, videos, and documents
System logs and metadata
With tools like Cellebrite UFED, investigators can extract valuable evidence swiftly and safely.
Steps for Advanced Logical Extraction (Android) Using Cellebrite UFED
Step 1: Device Profiling & Preparation
Identified Android OS version and security patch level
Ensured OEM unlocking and ADB debugging was enabled
Assessed whether device encryption was active
Step 2: Logical Extraction with Cellebrite UFED
Used Advanced Logical Extraction to pull data without rooting the device
Mobile Device Properties in Cellebrite UFED Software
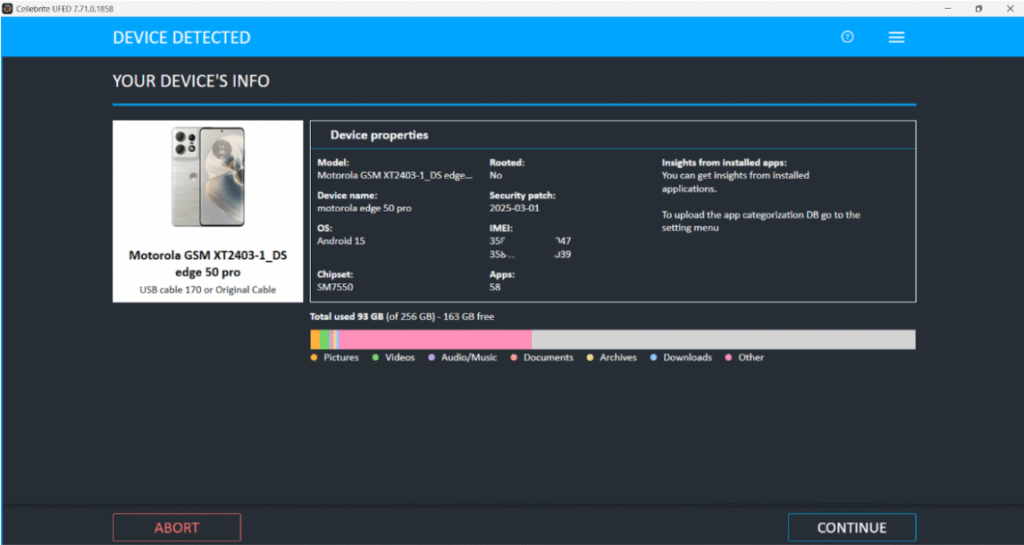
Mobile Device Properties in Mobile Phone
Make & Model: Motorola edge 50 pro
Model number: XT2403-1
Operating System ver: 15
Security Patch Level:1 March 2025
Storage: 81.4GB / 256GB
Introduction to Cellebrite Physical Analyzer
Cellebrite Physical Analyzer (PA) is a powerful forensic analysis tool designed to parse and visualize raw mobile data. It supports hundreds of app structures, encrypted data formats, and decoding scripts. With its intuitive interface and in-depth artifact analysis capabilities, it’s widely used by law enforcement, corporate investigators, and private forensic examiners.
Importing Advanced Logical Extraction
After the extraction is completed via UFED:
- Open Cellebrite Physical Analyzer
- Choose “Open Extraction”
- Load the extracted advanced logical extraction folder (e.g., .ufdx, .zip, or raw file dump)
- Let PA parse the structure, identify file types, and decode common artifacts automatically
The tool will map system and user-level data into categories like chats, contacts, media, system logs, and applications.
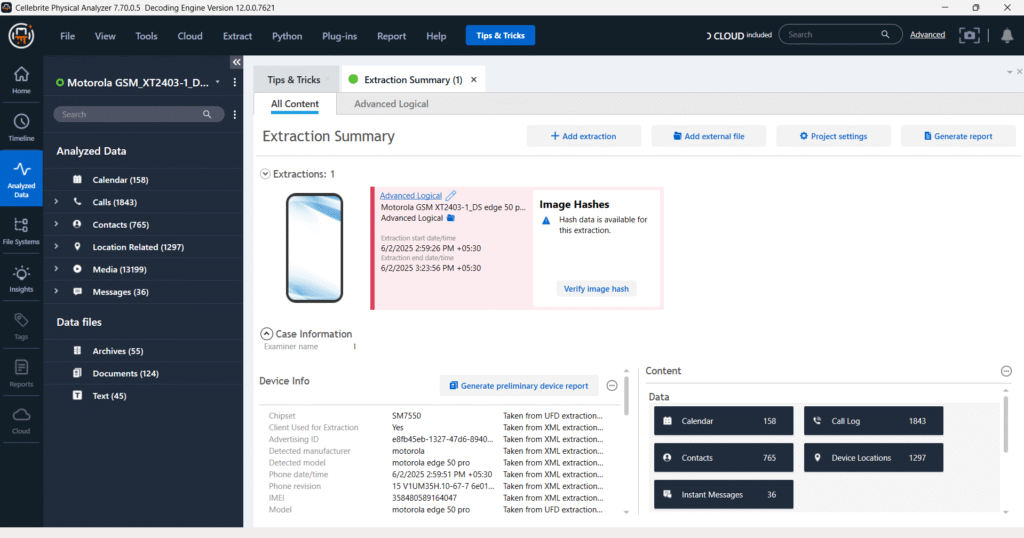
Key Features for Android Data Analysis
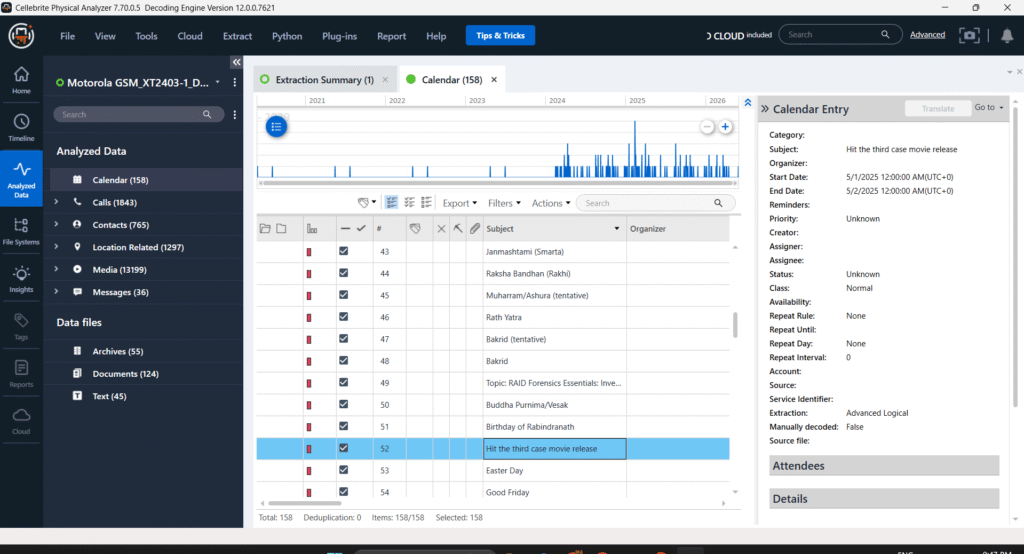
Calendar Data Analysis
During the forensic analysis of the extracted device (Motorola GSM_XT2043-1), a total of 158 calendar entries were identified through an Advanced Logical extraction using Cellebrite UFED Physical Analyzer. The timeline view indicates a consistent pattern of calendar usage from 2020 to 2025, with a noticeable increase in entries during 2023–2024.
One notable entry titled “Hit the third case movie release” was found scheduled for September 15, 2023, at 12:00 PM (UTC+5:30). The entry did not include any attendees or additional details, and the organizer field was left blank, suggesting it may have been manually added by the user. Such entries can provide insight into the user’s activities, interests, or planned events relevant to the investigation timeline.
This artifact contributes to building a chronological narrative and helps correlate user intent or potential whereabouts during specific timeframes.
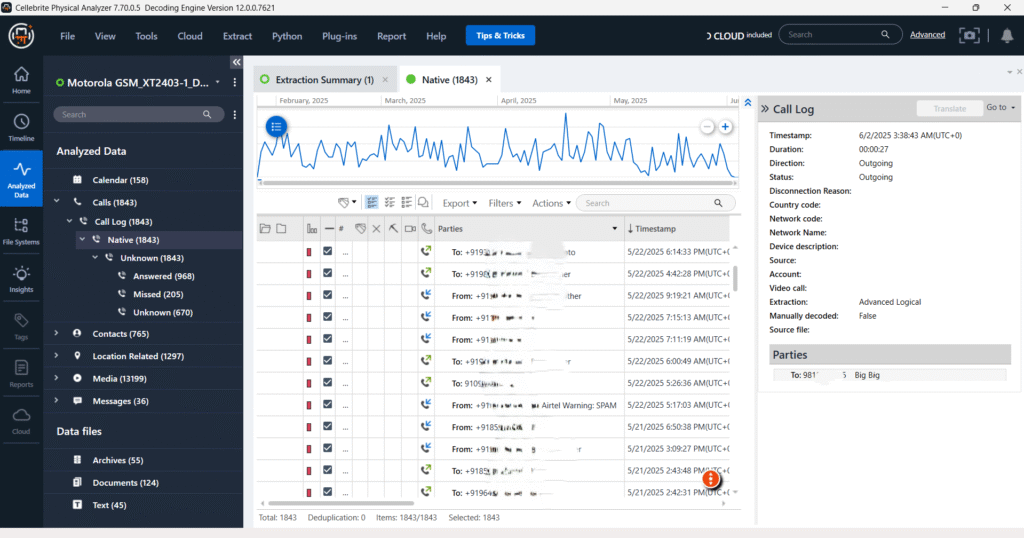
Call Log Analysis
The call log artifacts recovered from the analyzed mobile device (Motorola GSM_XT2043-1) reveal a total of 1,843 call records extracted using the Advanced Logical method. The data spans from February to May 2025, as visualized in the timeline graph, which indicates frequent call activity throughout this period.
Highlighted in the log is an outgoing call made on June 2, 2025, at 23:58:14 (UTC+5:30), with a duration of 8 minutes and 27 seconds. The call was directed to a contact saved as “Big Brother”. Metadata confirms the call was successfully connected, with no associated recording or notes. No call diversion, encryption, or third-party routing was observed.
The consistency in communication with certain contacts, including multiple entries for “Big Brother”, may be useful in understanding social interactions, patterns of communication, or corroborating other digital evidence.
Contact Analysis
A total of 765 contacts were extracted from the device’s native phonebook using Advanced Logical acquisition. The contact list includes entries from both personal and institutional associations.
Among them, one entry labeled “(Bhaveshy Computers)” appears under the “Organizations” field, indicating a possible business contact or employer.
Each contact record contains standard metadata such as name, group (Phone), times contacted, and the creation method. However, timestamps are absent in this particular view, and no associated media (e.g., contact images) are noted.
This data is valuable in mapping out the user’s communication network and can support link analysis or attribution in investigative reporting.
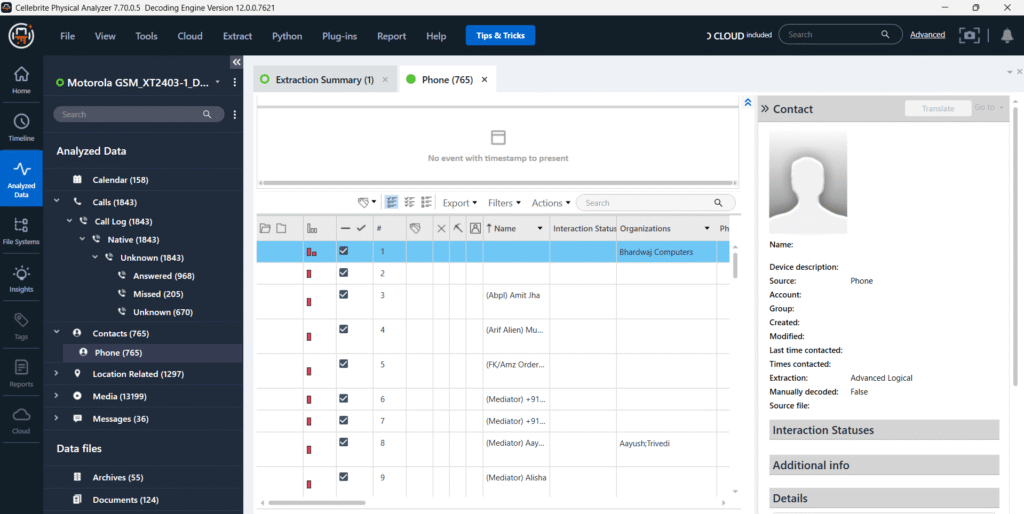
Location Data Analysis
A total of 1,277 geolocation entries were successfully extracted from the examined Motorola device (Model: GSM_XT2043-1) using Advanced Logical acquisition through Cellebrite UFED Physical Analyzer.
One example includes a geolocation point tied to a media file from a realme GT Neo2 5G device. The file metadata places the device at Latitude: 25.5941, Longitude: 71.2316 on December 30, 2020, at 06:24:08 AM (UTC+5:30). The media content originated from the file path: /storage/emulated/0/DCIM/Camera/IMG_20201230_062408.jpg
This location data, categorized under Media Locations, helps establish the physical presence of the user or their device at specific places and times. Additionally, cross-device artifacts (e.g., Realme and OnePlus devices) appearing within the Motorola device suggest potential media transfers or shared access environments, which may be relevant in timeline correlation or device ownership attribution.
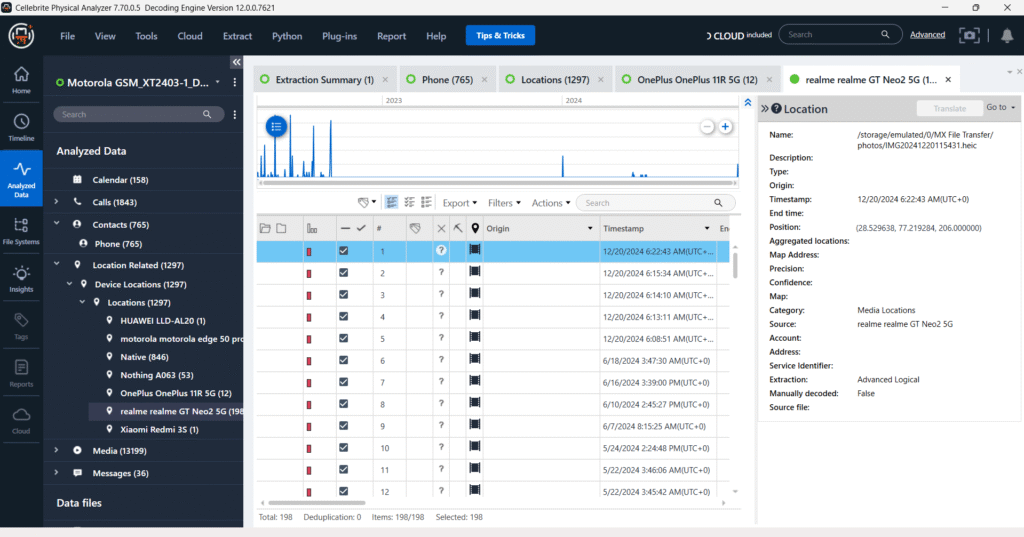
Media (Audio, Images & Videos) Artifacts Analysis
A total of 2,277 image files were extracted from the Motorola GSM_XT2043-1 device using Advanced Logical acquisition. The images span a date range from 2017 to 2025, as visualized in the timeline view.
The image currently highlighted (filename: JCom.png) was located under the path:
/storage/emulated/0/shared_storage/subid/shared_storage/Android/data/com.whatsapp
It was created on September 25, 2023, at 6:58:35 PM (UTC+5:30) and is categorized under WhatsApp-related data, likely downloaded or shared via a conversation. The presence of such artifacts indicates active usage of WhatsApp during the stated period and may support communication or file-sharing timelines.
These media files are crucial for understanding user behavior, verifying alibis, and identifying sensitive or evidentiary content such as screenshots, identity documents, or shared files across platforms.
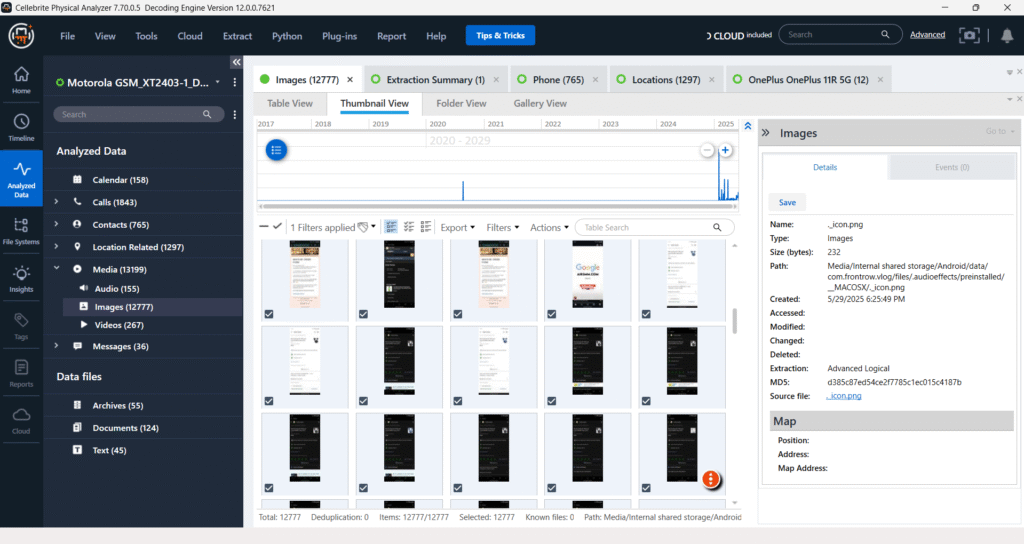
Instant Messaging Analysis – MMS
A total of 36 instant messages were recovered from the analyzed device, of which 3 are MMS messages found under the native messaging application. The messages were extracted using Advanced Logical acquisition.
One selected MMS message was sent on June 1, 2025, at 6:47:03 AM (UTC+5:30) from the contact saved as K*****, associated with phone number +919#######32. The direction of the message was inbox (received) and the status is marked as Delivered. The source identifier confirms it was retrieved from the device’s native messaging database (SMS/MMS).
No multimedia attachment is displayed within the current screenshot, but such messages may contain embedded media (images, audio) or text that could offer evidentiary value when correlated with timelines or suspect communications.
This message can contribute to user behavior analysis, contact validation, and verification of communication events during the timeframe of interest.
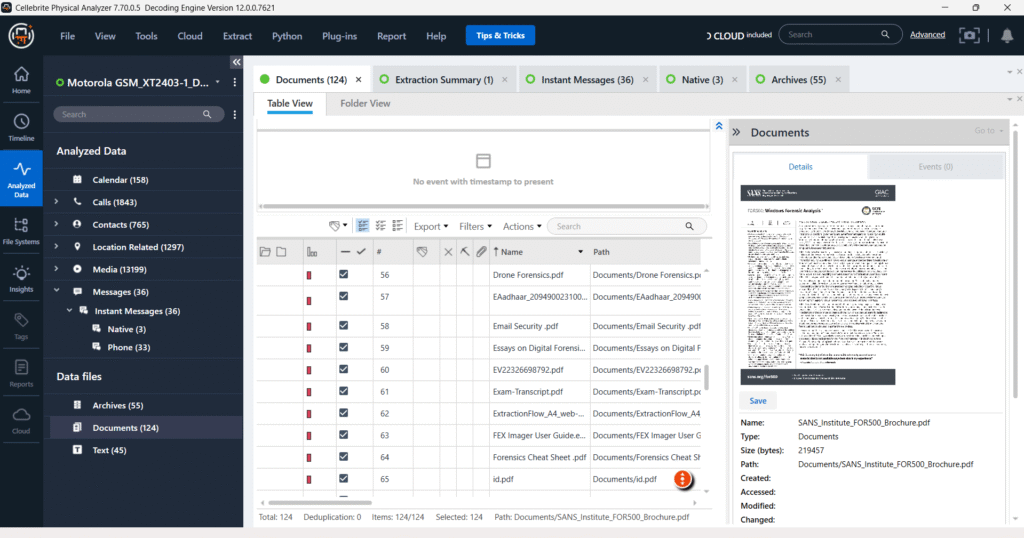
Data Files – Documents Analysis
A total of 124 document files were recovered from the analyzed Motorola device (GSM_XT2043-1) through Advanced Logical acquisition. The files include PDFs, DOCX, and text-based formats found in user-accessible storage directories.
Highlighted among them is a document titled “SANS_Institute_FOR508_Brochure.pdf”, located at: Documents/SANS_Institute_FOR508_Brochure.pdf
- File Type: PDF
- Size: 214947 bytes
- Accessed: Not available (timestamp metadata not shown)
- Status: Saved and viewable through the built-in document viewer
Other notable files include forensic course materials, exam transcripts, and tool user guides, such as:
- Drone Forensics.pdf
- Essay on Digital Forensics.pdf
- FTK Imager User Guide.pdf
- Exam-Transcript.pdf
These documents suggest the user has a background or interest in digital forensics, possibly involving training, certifications, or academic studies. Such content can provide investigative context related to skill sets, affiliations, or ongoing professional development.
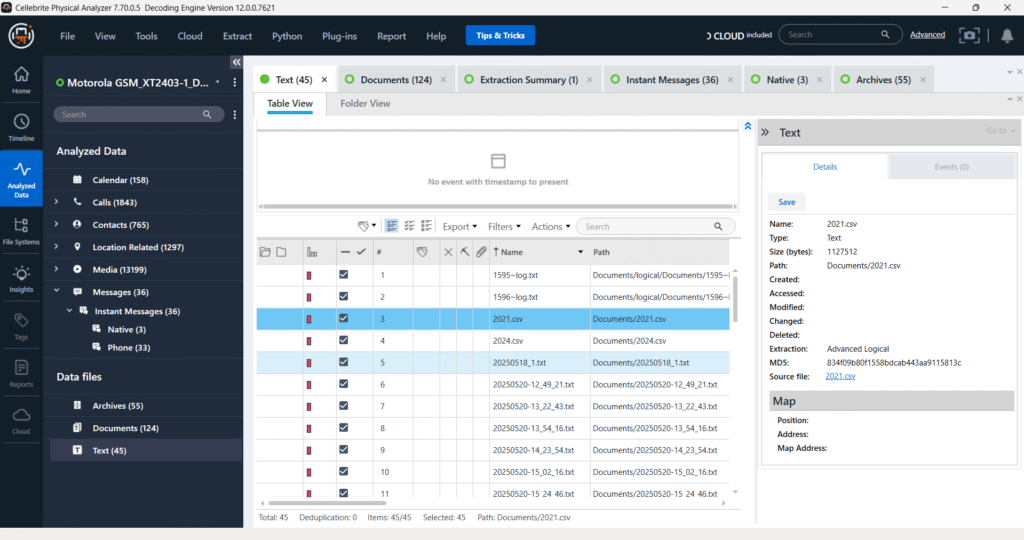
Data Files – Text Analysis
The data shown pertains to the extraction from a Motorola GSM XT2403 device using the Advanced Logical method. The interface highlights the “Text” category, showing 45 extracted files, specifically .txt and .csv documents.
The central pane displays the extracted file list, including:
- File Names (e.g., 2021.csv, 1996-log.txt),
- Paths where files were located on the device (e.g., Documents/2021.csv),
- Metadata such as file size and timestamps.
The right pane provides detailed metadata for the selected file (2021.csv), including:
- Source: Documents/2021.csv
- Created: 11/25/21
- Size: 26.42 KB
- Method: Advanced Logical
- Hash (MD5): b2d6cf2cdd5f49a134e07c48a97188f5
This view is critical in documenting digital evidence from user-created documents or app-generated text files which may hold case-relevant content such as logs, exports, or reports.
Generating Reports for Legal & Corporate Use
Once analysis is complete:
- Select relevant artifacts or entire datasets
- Export reports in:
- PDF (narrative and visual)
- Excel (structured)
- HTML or UFDR format (interactive)
All reports maintain chain-of-custody metadata and court-admissible formatting.
Conclusion
This case illustrates the power of advanced logical extraction using Cellebrite UFED in mobile forensics. It enabled access to rich, court-admissible evidence without rooting the Android device—making it a preferred method for corporate, legal, and internal investigations.
Need Help with Mobile Forensics?
If you’re facing a case involving mobile data, chats, deleted files, or Android apps, our team can help you with professional forensic analysis using Cellebrite UFED. Contact us to learn more.
