Case Studies
Explore our confidential case studies where Xpert Forensics uncovered digital fraud, insider threats, data leaks, and cyber misconduct using advanced forensic tools and investigative techniques. Each case reflects our commitment to precision, discretion, and delivering actionable insights that drive resolution.
Mobile Forensics (Android): Full File System Extraction & Analysis Method Using Cellebrite UFED
Introduction
In the evolving world of digital forensics, mobile devices—especially Android phones—are a goldmine of evidence. From chat messages and emails to call logs and app data, the smartphone holds valuable insights. However, gaining access to and analyzing this data requires advanced tools and techniques. One of the most trusted solutions in the industry is Cellebrite UFED (Universal Forensic Extraction Device).
In this blog, we explore the complete process of Full File System Extraction and forensic analysis of Android devices using Cellebrite UFED. Whether you’re a forensic analyst, investigator, or cybersecurity professional, this guide will help you understand the real-world application of Android mobile forensics.
What is Mobile Forensics?
Mobile forensics involves the recovery, acquisition, and analysis of digital evidence from mobile devices. Unlike traditional computers, smartphones have complex file systems, encryption layers, and app data containers—making extraction and analysis more challenging.
For more information about Mobile forensics read this article: Mobile Forensics
Cellebrite UFED: A Trusted Tool in Forensics
Cellebrite UFED is one of the most popular tools used by law enforcement and forensic professionals globally. It allows:
- Physical and logical extractions
- Advanced app data recovery
- Full file system access (including hidden or deleted files)
- Cloud and SIM data acquisition
- Bypassing lock screens (on supported devices)
Steps for Full File System Extraction (Android) Using Cellebrite UFED
Step 1: Launch Cellebrite UFED
Open UFED 4PC and connect the Android device via USB.
Step 2: Select Device Profile
UFED will auto-detect or prompt you to manually select the device model.
Step 3: Choose Extraction Method
Select “Full File System Extraction” if supported. If not available, UFED may suggest alternative options like:
- File-based extraction
- Physical (chip-off or JTAG)
- Logical
Mobile Device Properties in Cellebrite UFED Software
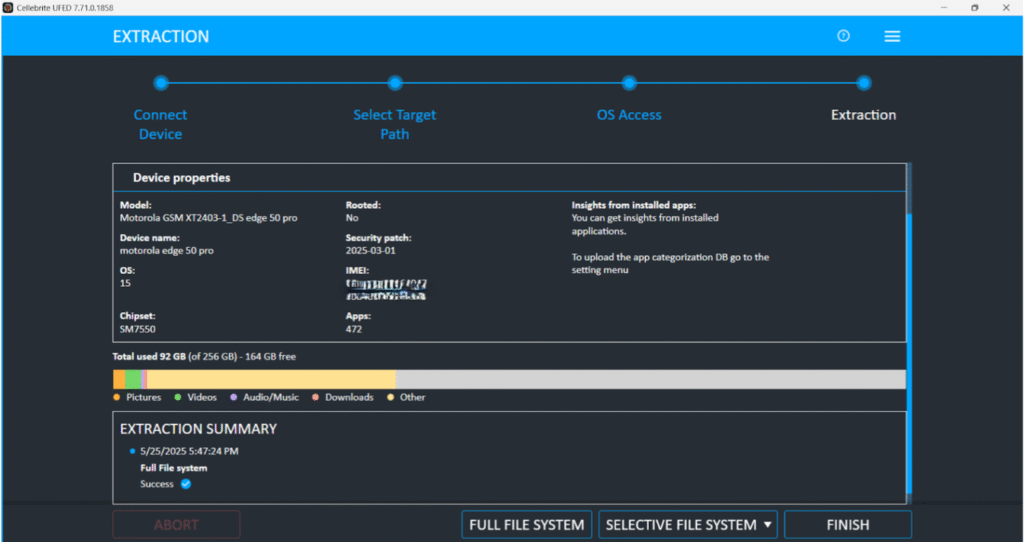
Mobile Device Properties in Mobile Phone
Make & Model: Motorola edge 50 pro
Model number: XT2403-1
Operating System ver: 15
Security Patch Level:1 March 2025
Storage: 79GB / 256GB
Introduction to Cellebrite Physical Analyzer
Cellebrite Physical Analyzer (PA) is a powerful forensic analysis tool designed to parse and visualize raw mobile data. It supports hundreds of app structures, encrypted data formats, and decoding scripts. With its intuitive interface and in-depth artifact analysis capabilities, it’s widely used by law enforcement, corporate investigators, and private forensic examiners.
Importing Full File System Extraction
After the extraction is completed via UFED:
- Open Cellebrite Physical Analyzer
- Choose “Open Extraction”
- Load the extracted full file system folder (e.g., .ufdx, .zip, or raw file dump)
- Let PA parse the structure, identify file types, and decode common artifacts automatically
The tool will map system and user-level data into categories like chats, contacts, media, system logs, and applications.
Key Features for Android Data Analysis
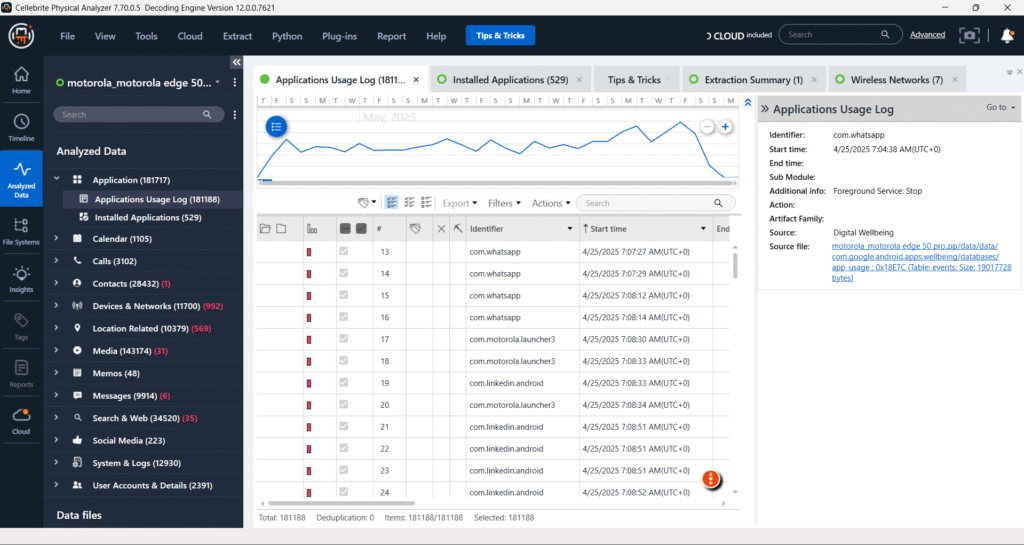
Application usage Log
It shows application usage logs from a Motorola Edge device. It captures activity for apps like WhatsApp, Kotak Mahindra Bank, Paytm, Instagram, MX Player and LinkedIn, including precise start times, durations, and source paths. These logs provide crucial insights into user app behavior and session timelines.
Installed Application
The screenshot shows the “Installed Applications” section in Cellebrite Physical Analyzer. While multiple chat applications like Gmail, Instagram, LinkedIn, WhatsApp, Telegram, and Tango are installed on the device, only a subset (e.g., 5 out of 8 chat apps) have been successfully decoded and extracted by the tool. This reflects Cellebrite’s selective decoding capability, which may vary based on app data accessibility and encryption.

In this screenshot from the “Installed Applications” section of Cellebrite Physical Analyzer, the device contains various browser and privacy-focused apps like Brave, Chrome, and Via. While three browsers are detected, only 2 out of 3 have been decoded by Cellebrite. Categories such as “Hide files,” “Clean mobile,” and “Spy camera” show installed apps but none have been decoded, highlighting limitations in decoding certain privacy or security tools.
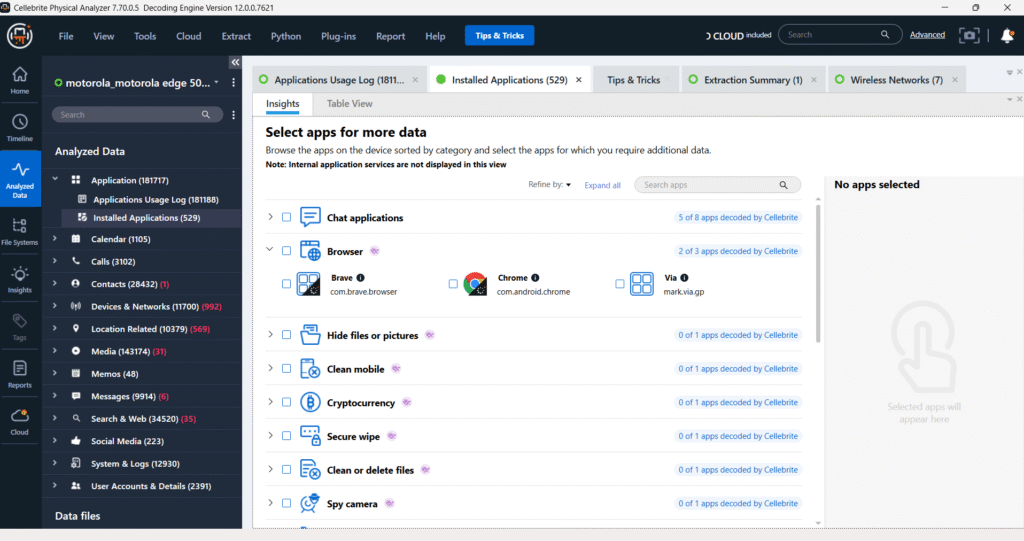
In the “Installed Applications” section of Cellebrite Physical Analyzer, only a few lifestyle apps are decoded while many remain unsupported. This happens because Cellebrite only fully supports popular or high-priority apps with specific decoding plugins. Many lifestyle apps like Zepto or Meesho are cloud-based, store minimal local data, or use encryption, making extraction difficult. Additionally, modern Android restrictions and app sandboxing further limit access to internal app data. To gather more insights, investigators can manually examine app directories, cached files, or system logs.
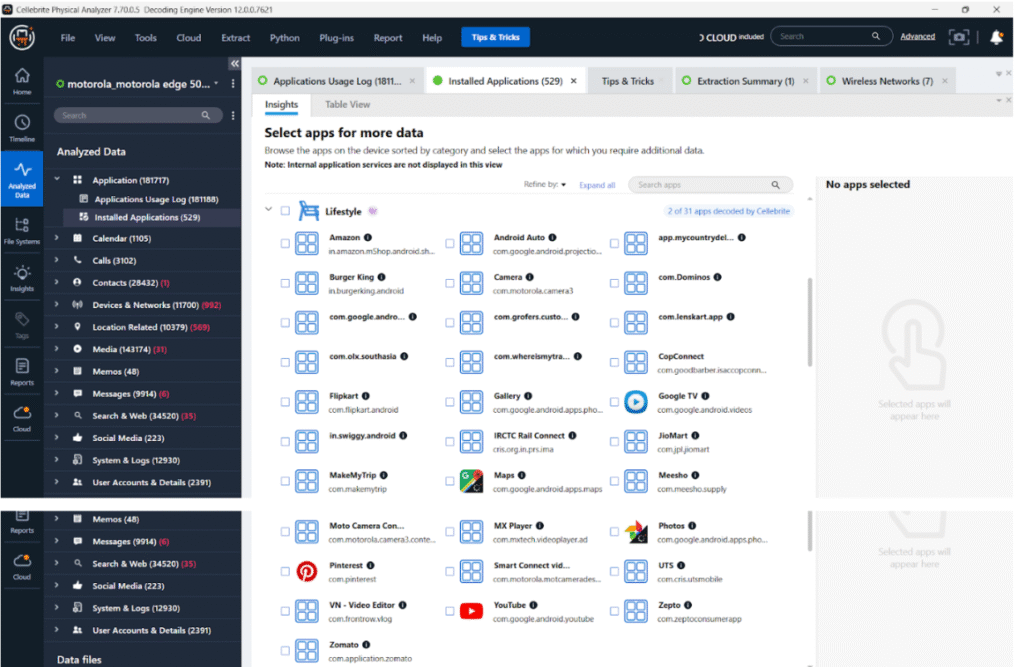
In the “Finance” category of the Installed Applications section, Cellebrite Physical Analyzer shows many popular apps like Paytm, PhonePe, GPay, SBI Card, and Axis Mobile. However, none of these apps are actually decoded by the tool. Most financial applications are highly secure, use end-to-end encryption, and store minimal data locally, which limits data extraction. Additionally, the note “0 of 16 apps decoded by Cellebrite” highlights the challenge forensic analysts face with decoding secure finance apps on modern Android devices.
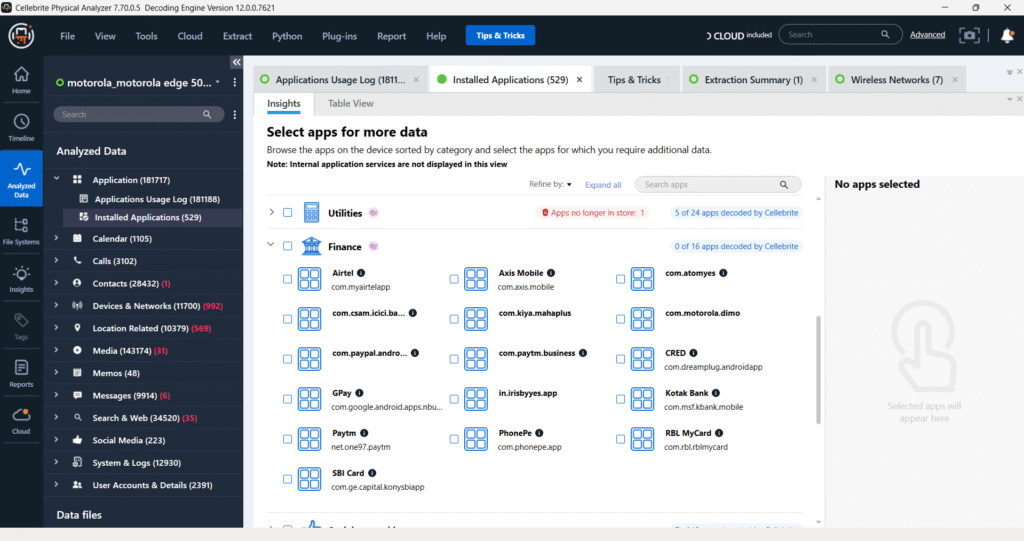
The “Installed Applications” section displays a list of various utilities found on the device. However, only a subset of these applications has been extracted by the software, as indicated by the “5 of 24 apps decoded by Cellebrite” message. This suggests that while 24 utility applications were identified, the tool was only able to fully process and present data for 5 of them, leaving the remaining utilities as either partially processed or not decoded.
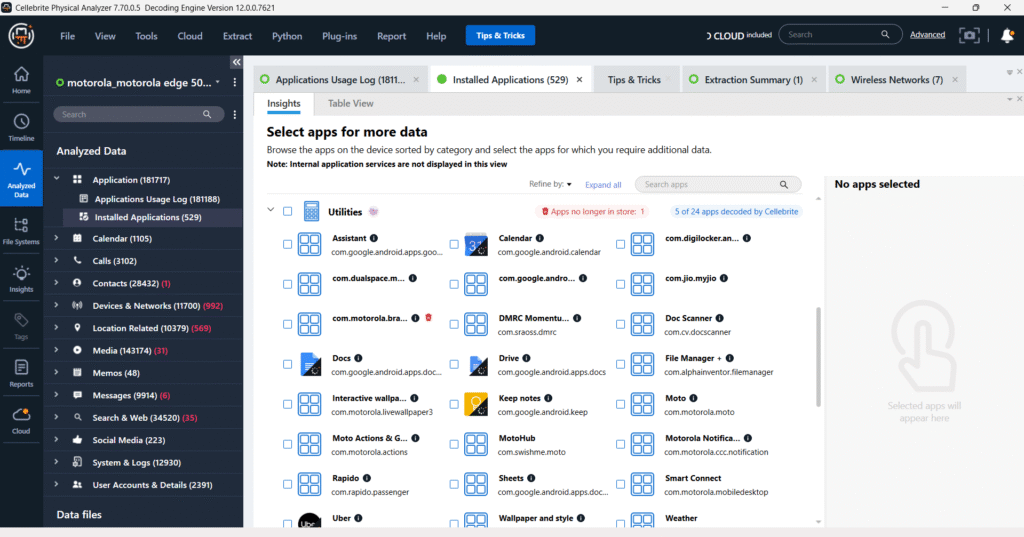
In the Cellebrite Physical Analyzer screenshot, Telegram appears under the Social Networking category with a status indicating no data was backed up. However, when examining the Messages section, there are 260 entries attributed to Telegram. Despite the presence of these entries, none of the messages are readable. This discrepancy often occurs when app data is stored in encrypted formats or on secure cloud servers, preventing successful decoding or content extraction by forensic tools.

Calendar
The screenshot from Cellebrite Physical Analyzer displays calendar data extracted from a device. It reveals multiple calendar entries sourced from various Google accounts. One notable entry titled “Amazon Prime membership end date” is selected, showing its details on the right panel. It was created using Google Calendar, and includes metadata such as event creator email, source file, and service identifier.
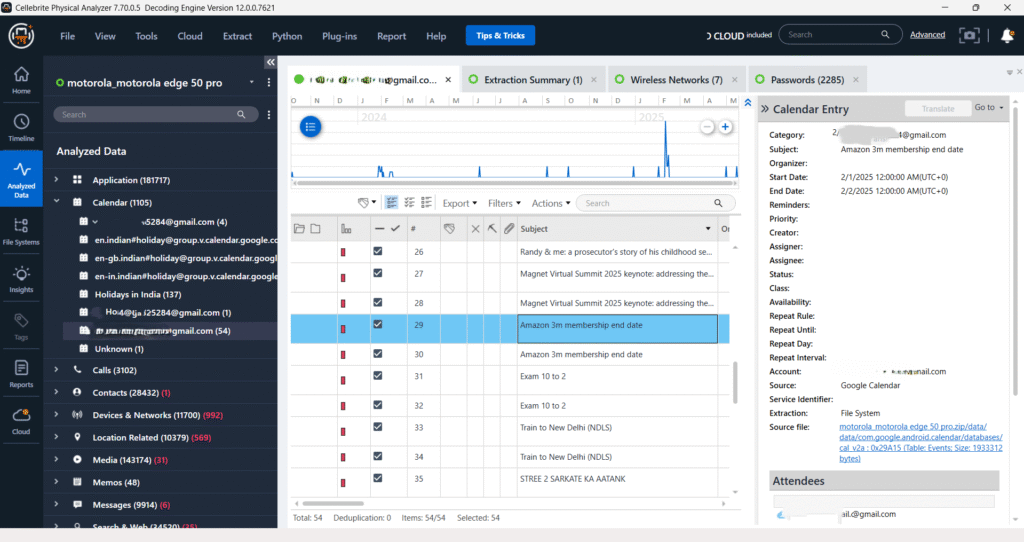
Call Logs – Facebook
The screenshot shows the Facebook call log data extracted using Cellebrite Physical Analyzer from a device. The interface displays several incoming and outgoing call records associated with Facebook Messenger, complete with timestamps, call directions, and duration. On the right panel, the metadata reveals details such as message ID, sender and receiver IDs, country code, and source file path. These call logs serve as vital evidence for analyzing communication behavior on social media platforms.
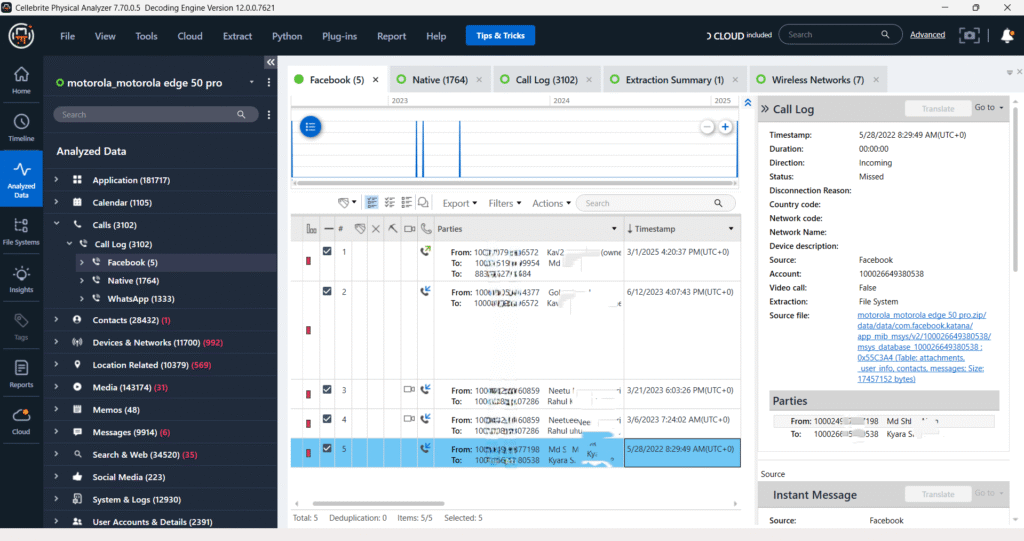
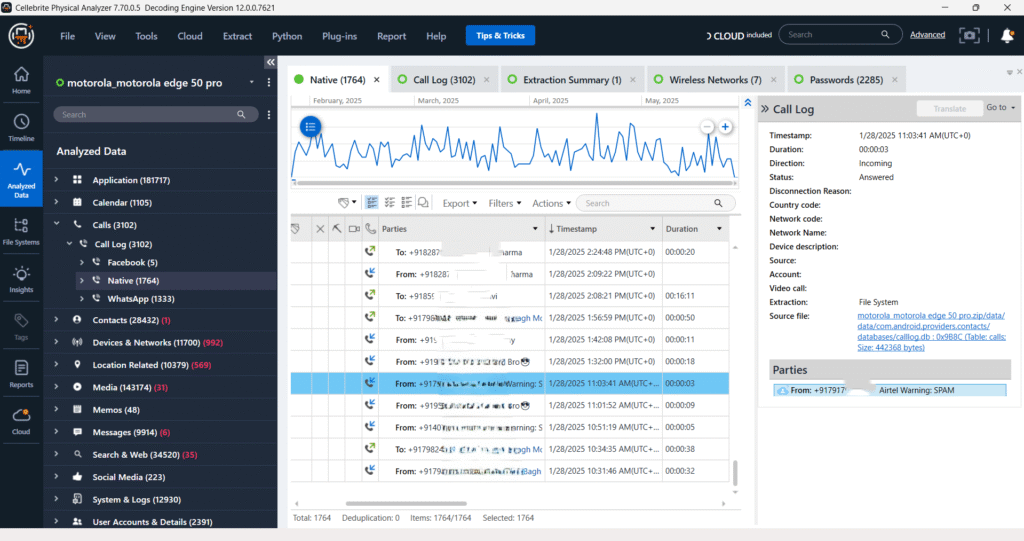
Call Logs – Native
The native call log data from the Device reveals a total of 1,764 call entries, including incoming, outgoing, and missed calls. One highlighted call shows an incoming call from a contact saved as “Arun Vannraj SKNM,” answered on January 2, 2023, with a duration of 3 seconds. This log is essential for establishing communication patterns in the forensic investigation.
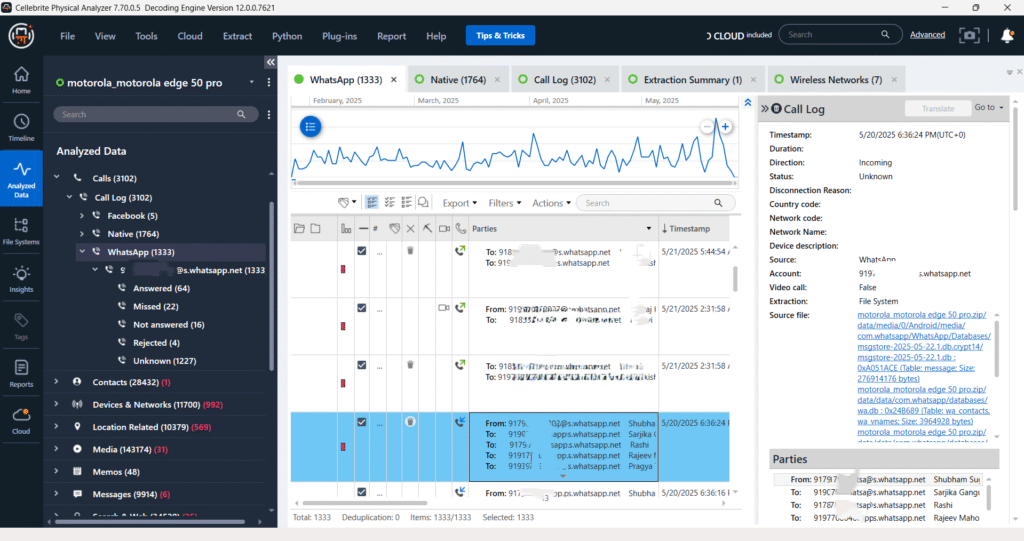
Call Logs – Whatsapp
The WhatsApp call logs from the Device reveal a total of 1,333 entries, including both voice and video calls. These logs contain key details such as timestamps, call direction (incoming/outgoing), and involved parties. One sample shows a call to a contact saved as “Shubham Singh” on May 2, 2023, at 6:26 AM, marked as an incoming call with an unknown duration. The call data is sourced from the wa.db file, supporting the analysis of communication patterns over WhatsApp.
Contacts
The contact data extracted from the device displays a total of 28,432 contact entries, including those from WhatsApp, SIM, Google, and other messaging platforms. Each contact contains attributes such as name, number, organization, and interaction status.The interface also provides interaction statuses (e.g., blocked or friend) and source details linking to the original application database such as wa.db.
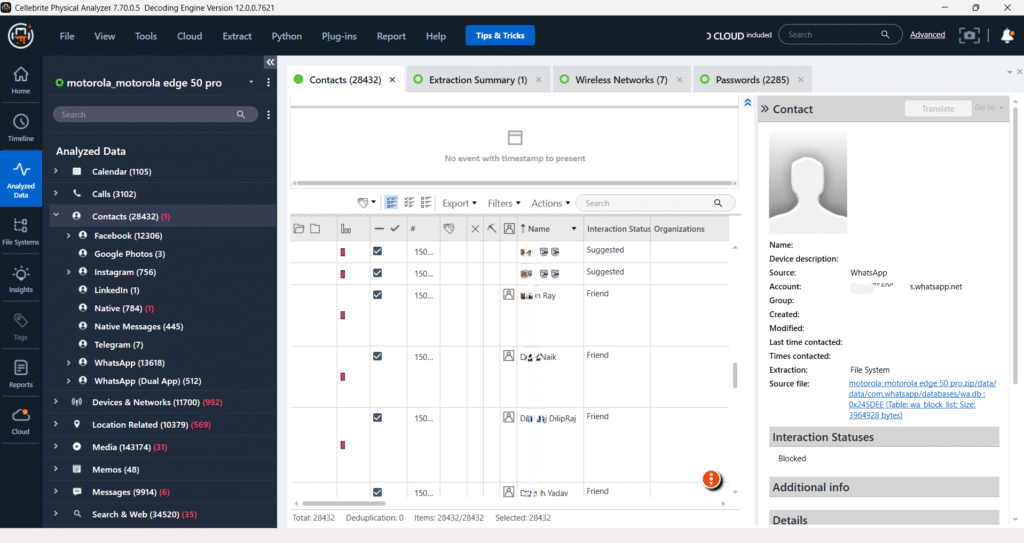
Devices & Networks – Device Connectivity
The Device Connectivity data from the Device reveals interaction logs with 1,657 devices or platforms. Key entries show connections to external devices like “Scoti Auto Anton” via Bluetooth, and applications like “Google Chrome” on different dates. Each connectivity event includes a timestamp, artifact source, and connection method, offering insight into the user’s paired or recognized devices.
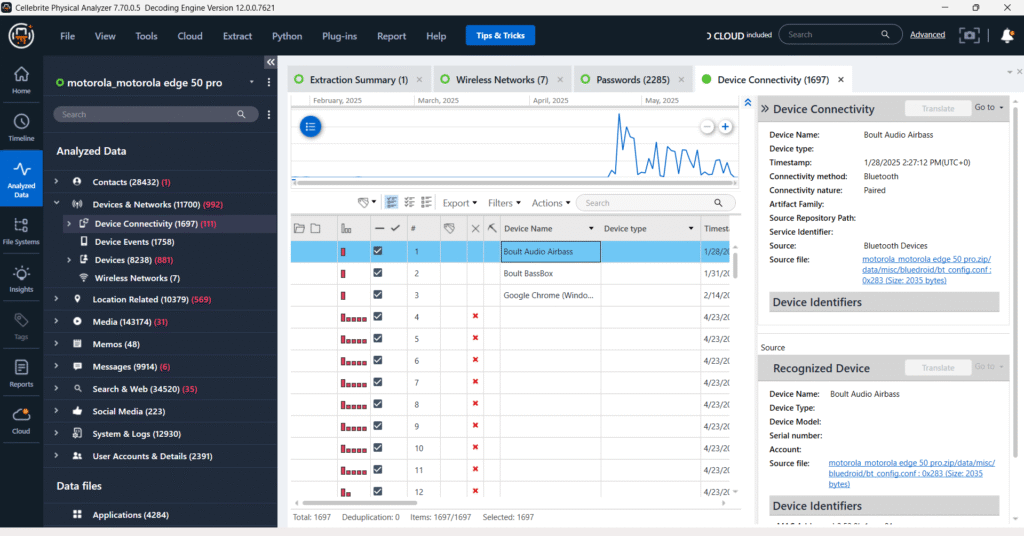
Devices & Networks – Wireless Networks
The Wireless Networks section in the device analysis reveals that the device is connected to several Wi-Fi networks. One notable entry is for the SSID “ApexUser_5192”, using WPA/PSK security and showing the password in plain text as ar9867. This is a critical forensic insight, as the exposure of plaintext Wi-Fi credentials can highlight poor security practices and potential unauthorized access points.
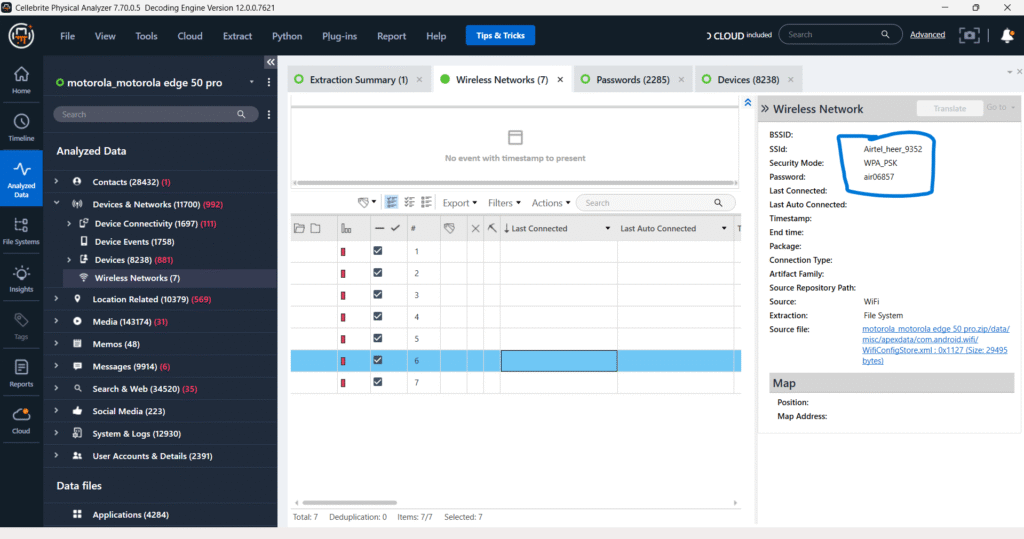
Device Locations
The Device Locations tab provides GPS data linked to the device, extracted from Google Location History. The records include detailed timestamps, coordinates, and origin metadata, such as “Visited” status. A highlighted entry from 5/25/2025 at 12:28 PM shows a location associated with a known hotspot (“Hotspotnet 100”) with coordinates pointing to a specific map location. This data can be instrumental in tracking user movements and establishing presence at specific places and times during an investigation.
Media – Images
The Media – Images tab displays a comprehensive thumbnail gallery of over 130,000 images extracted from the Device. This includes user photos, screenshots, WhatsApp media, and saved files. Each image is accompanied by metadata such as creation date, file path, and file type, as shown in the preview panel on the right. The image previewed here features storage containers, likely cataloged under product or shopping-related content, which may assist in profiling the user’s interests, habits, or recent activities.
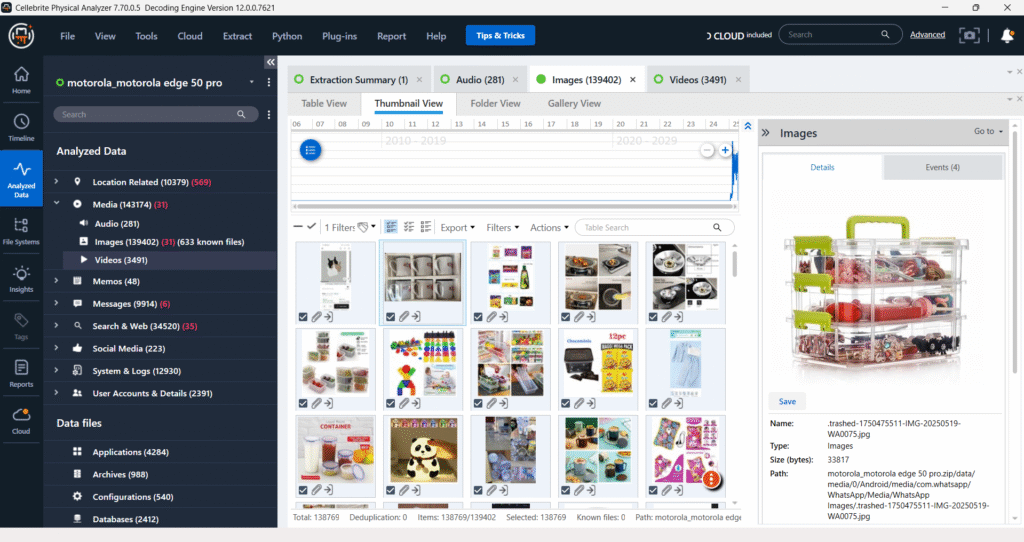
The “Videos” section, when viewed in thumbnail mode, displays a visual overview of extracted video files. On the right panel, detailed information for a selected video, such as file path, type, size, and creation/modification dates, is presented, offering a comprehensive view of its metadata.
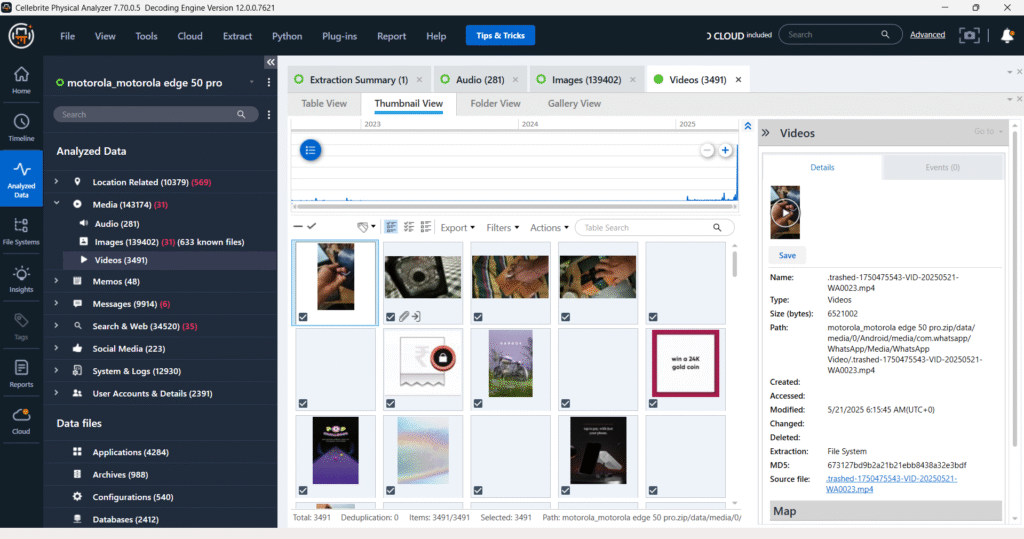
The “Videos” section, when viewed in the folder view, presents a hierarchical structure of video files, organized by their location within the device’s file system. This allows users to navigate through various directories, including those from messaging apps like WhatsApp and Instagram, to locate and examine video evidence.
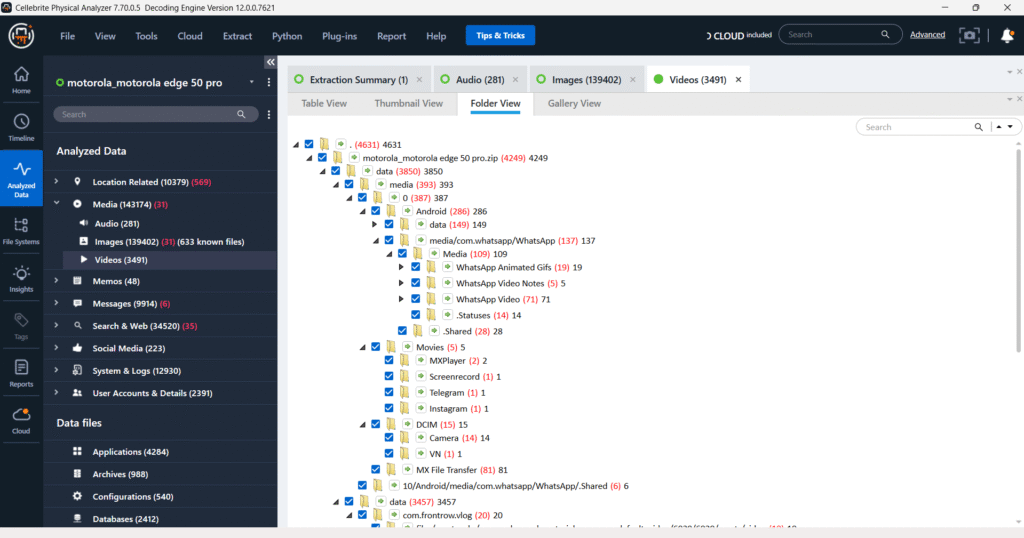
Notes – Keep
The “Notes – Keep” section displays extracted notes, likely from Google Keep, showing details such as creation time, modification time, and a preview of the note’s body. The right panel provides comprehensive metadata for the selected note, including its source, account, and associated file system path.
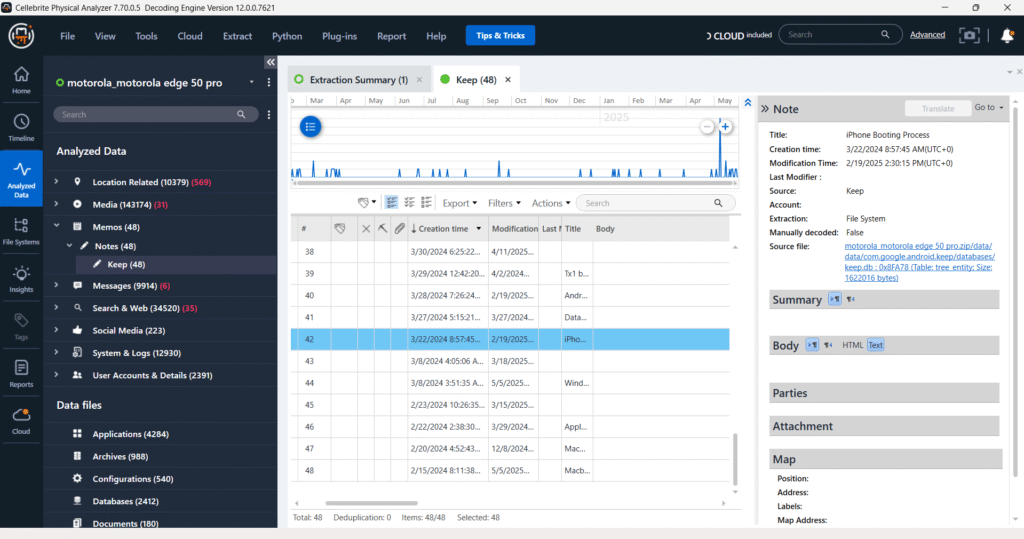
Messages – Chats – Facebook
In the “Messages – Chats – Facebook” section, Cellebrite Physical Analyzer categorizes Facebook Messenger chats. The circled area indicates different chat threads, each potentially representing a conversation with a specific Facebook account. While the image doesn’t explicitly state how many unique Facebook IDs are logged in, each listed chat thread likely corresponds to a distinct participant or group conversation within Facebook Messenger, allowing for analysis of communications tied to those specific accounts.
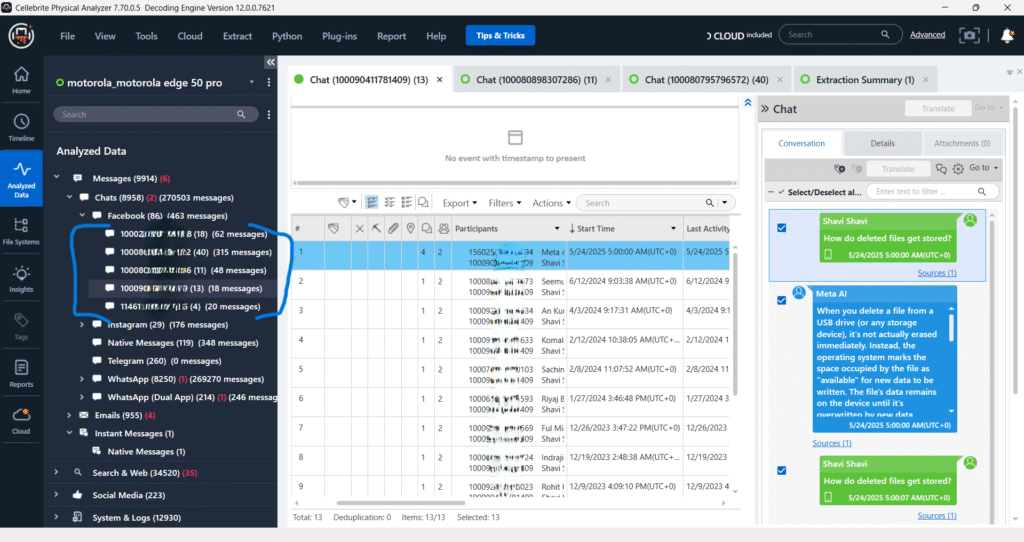
Messages – Chats – Instagram
The “Messages – Chats – Instagram” section shows different Instagram chat threads. The two highlighted entries (322 with 161 messages and 7851 with 18 messages) represent distinct conversations. It is highly probable that each of these entries corresponds to a different Instagram account or direct message conversation being analyzed, suggesting the presence of at least two different Instagram user IDs within the extracted data.
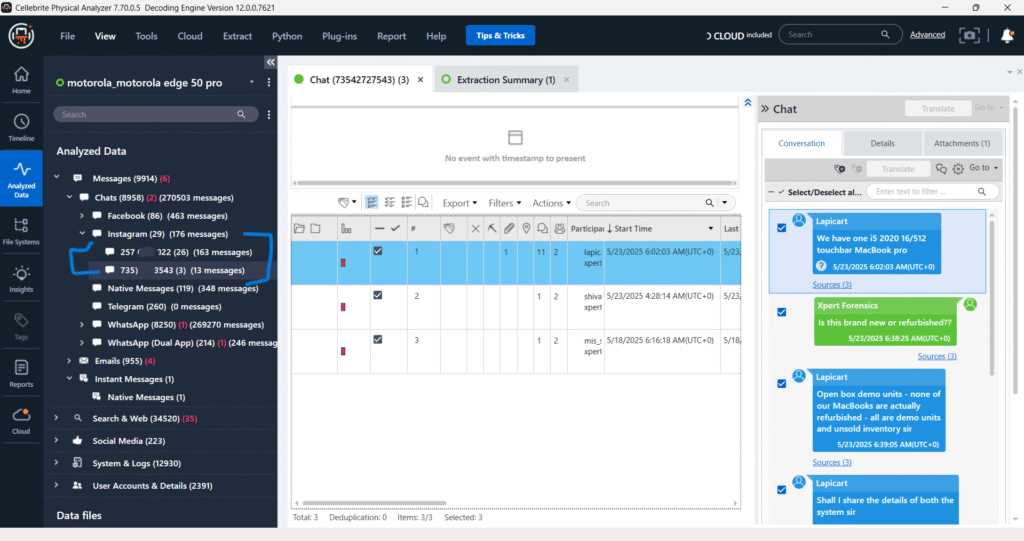
Messages – Chats – Native messages
The “Messages – Chats – Native Messages” section displays SMS/MMS conversations extracted from the device. Each entry represents a native chat thread, showing the participants and a timestamp. On the right panel, the content of the selected message is displayed, providing details of the communication.
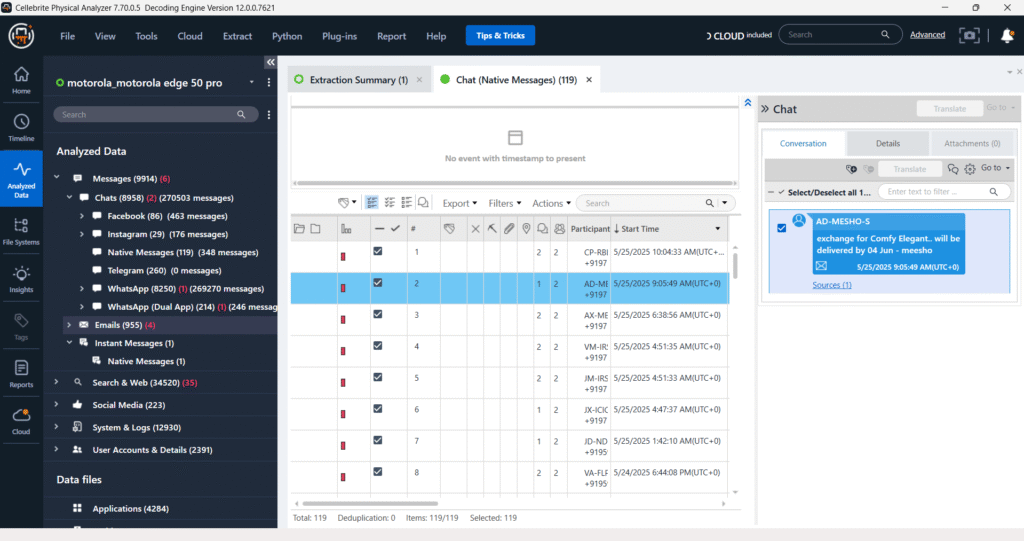
Messages – Chats – Telegram
The “Messages – Chats – Telegram” section is designed to display extracted Telegram conversations. However, as indicated by “Telegram (260) (0 messages)“, there are 260 Telegram-related entries found, but currently, no message content is visible or decoded for these entries. The right panel for “Chat” remains empty, signifying that the chat data for Telegram is either not present, corrupted, or not yet processed by the software.
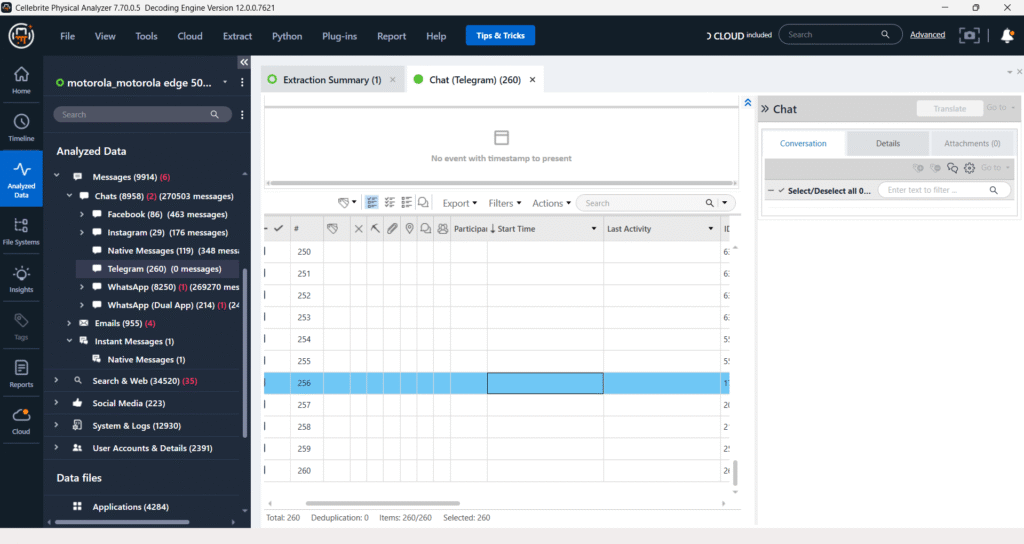
This indicates that while 260 Telegram-related entries or artifacts were found during the extraction, no actual message content was detected or successfully decoded from these entries.
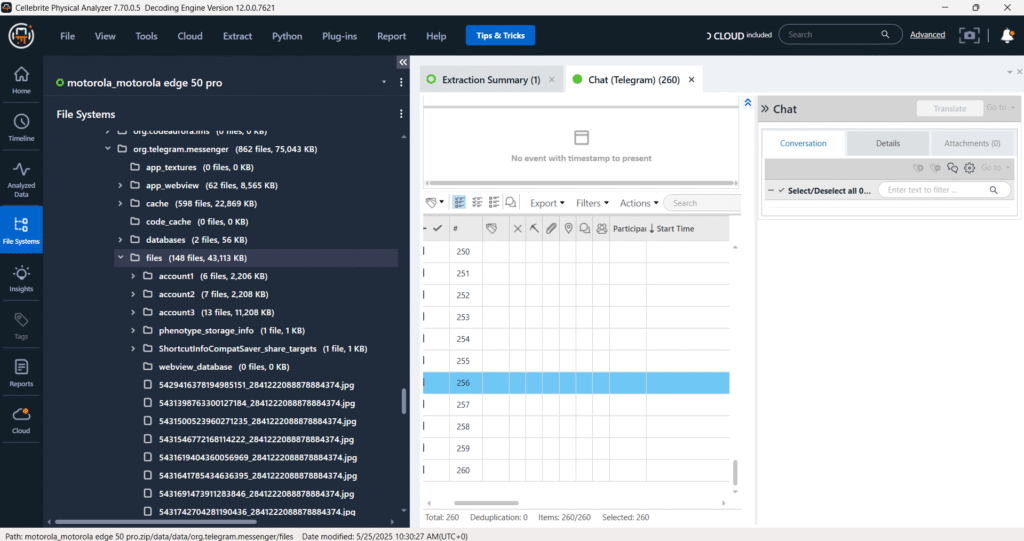
The image shows the “Messages – Chats – Telegram” section within Cellebrite Physical Analyzer. Although the tool identified 260 Telegram-related entries, denoted by “Telegram (260)“, it explicitly states “(0 messages)“, indicating that no actual chat content was successfully extracted or decoded. This highlights a common challenge in digital forensics where an application’s presence is detected, but its encrypted or deleted data remains inaccessible for analysis.
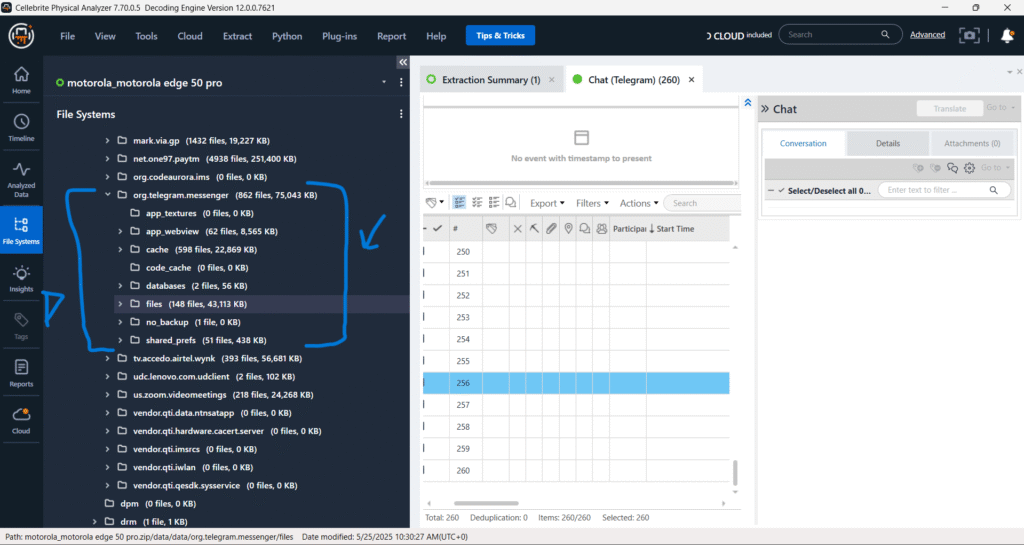
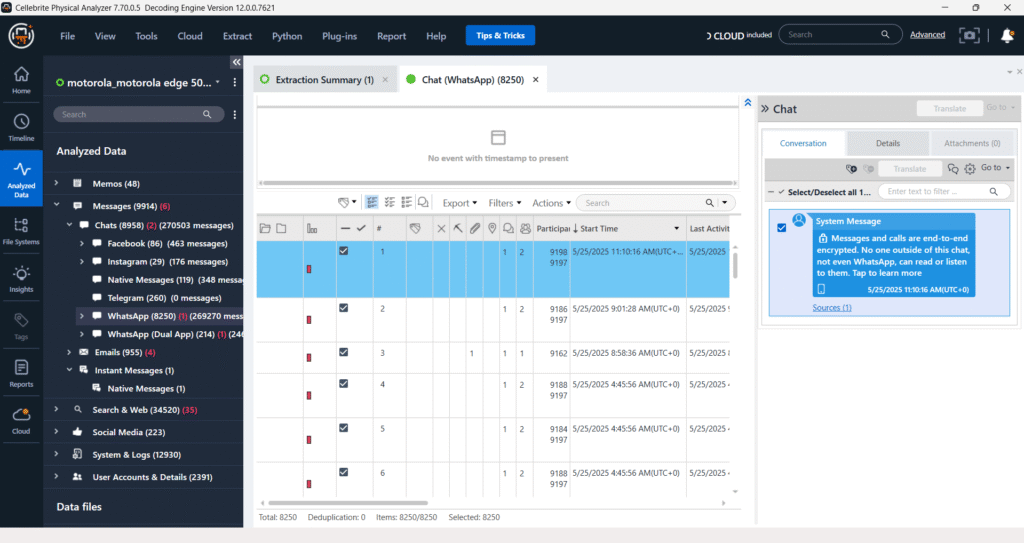
Messages – Chats – Whatsapp
The image confirms that Cellebrite UFED successfully extracted data from two separate WhatsApp installations. This is indicated by “WhatsApp (8250) (260270 messages)” and “WhatsApp (Dual App) (214) (248 messages)“. This capability allows forensic examiners to analyze communications from both the standard WhatsApp application and any cloned or “dual app” versions present on the device.
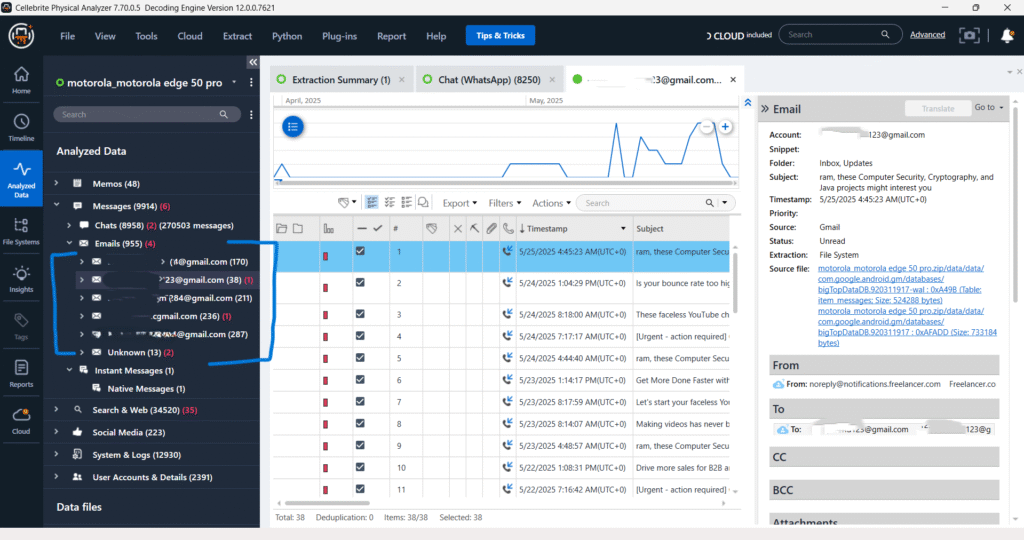
Messages – Chats – Emails
In the “Emails” section, multiple email accounts have been extracted, as indicated by the various email addresses listed (e.g., Gmail accounts). The “Unknown (1)” entry likely refers to an email that the software could not attribute to a specific known account or a forwarded email whose original sender is not directly associated with the extracted accounts. This category serves as a catch-all for emails that don’t fit neatly into the recognized email accounts, potentially including those forwarded from external sources to one of the device’s registered emails.
Search & Web
The “Search & Web” section in Cellebrite Physical Analyzer offers a granular view of a user’s online activities. It meticulously breaks down internet usage into categories like browser history, cookies, downloads, and general web history, predominantly from Chrome. This detailed classification, coupled with specific metadata for each entry, such as timestamps and source applications, provides a robust framework for digital forensic investigators to reconstruct Browse patterns and identify relevant downloaded content.
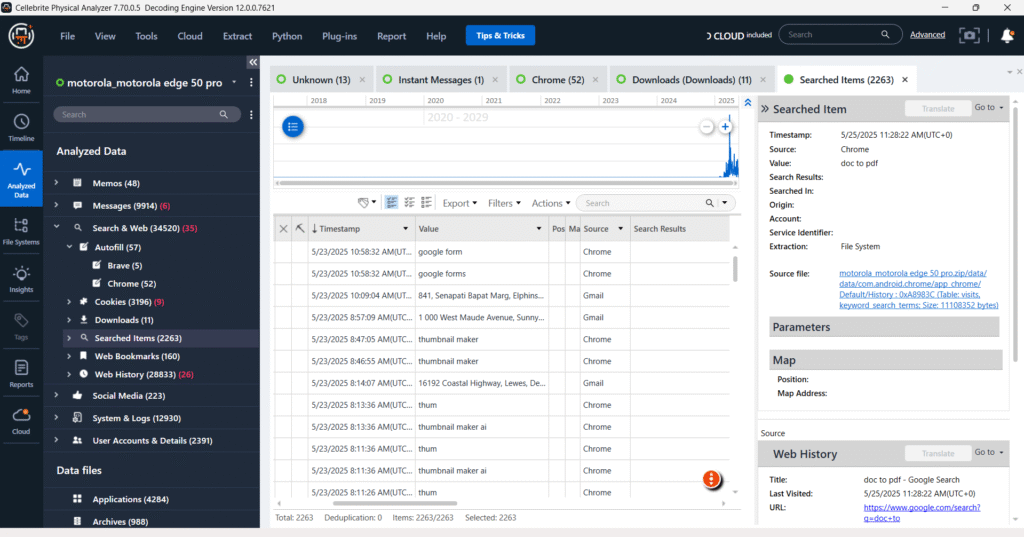
Social Media
The “Social Media” section within Cellebrite Physical Analyzer consolidates data from various social networking applications found on the device. As seen in the provided images, this includes detailed extractions from platforms like Facebook and Instagram, showing both chat conversations and potentially other social media interactions. This centralized view allows investigators to analyze communication patterns and user activity across multiple social platforms.
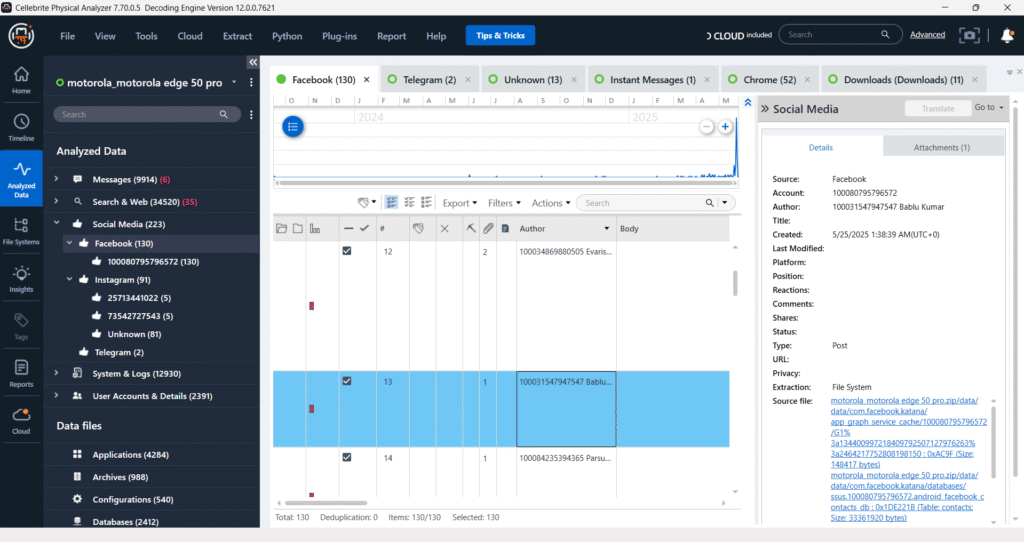
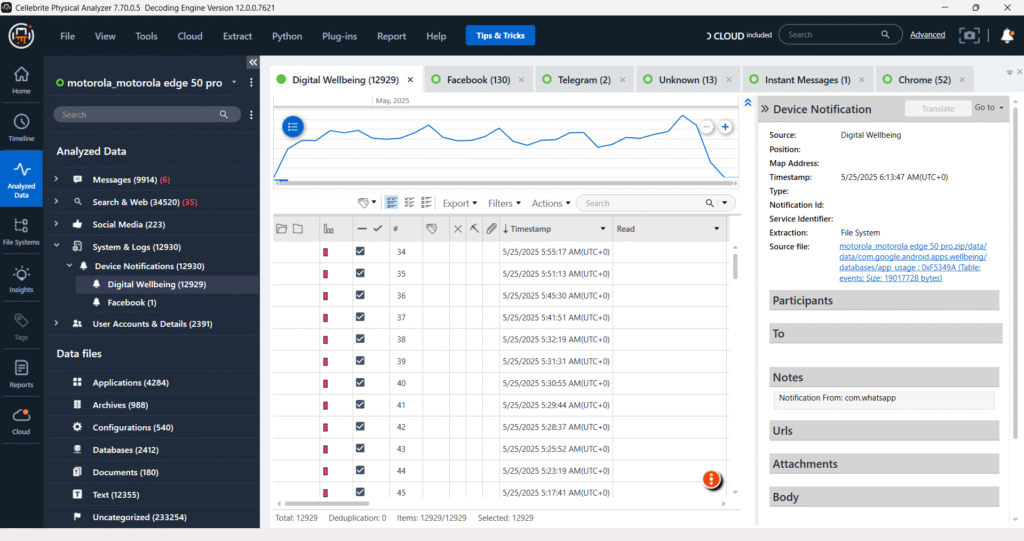
System & Logs
The “System & Logs” section provides crucial forensic data by detailing various system-level activities and logs. This includes “Device Notifications,” which can reveal app interactions and user behavior, and other system-generated records.
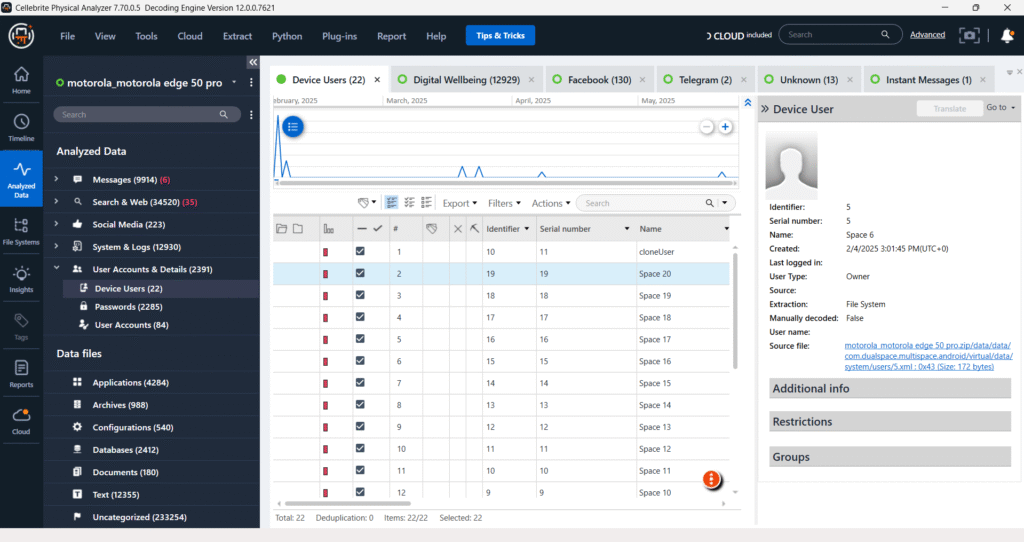
User Accounts & Details – Device Users
The “Device Users” section of the forensic analysis shows multiple entries with identical application names like “Space 20” and “Space 19,” but distinct serial numbers. This indicates the presence of several cloned application instances or separate user profiles/spaces on the analyzed device, likely a Device. This is a common finding in mobile forensics, often due to features allowing users to create parallel app installations for different accounts or to segregate personal and professional data.
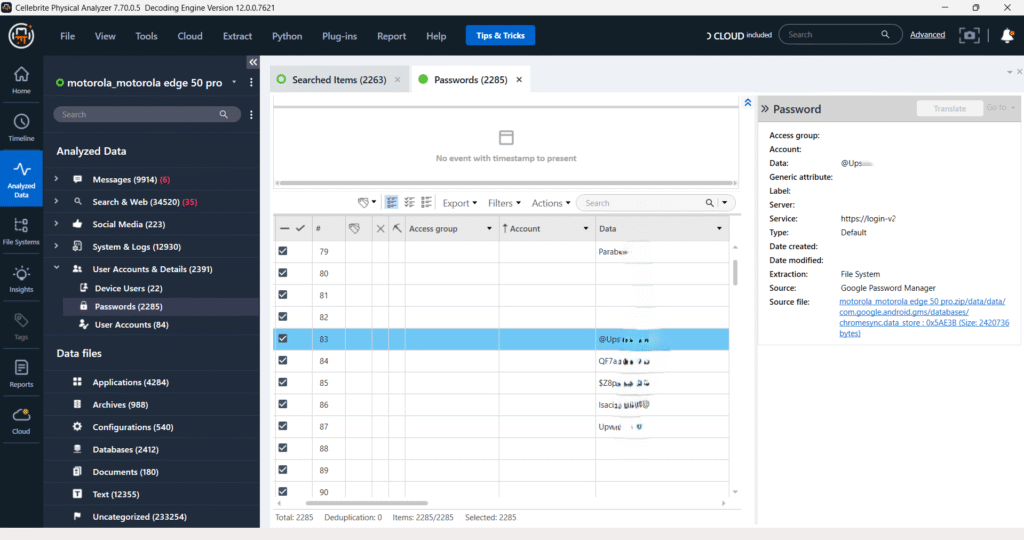
User Accounts & Details – Passwords
This screenshot from Cellebrite Physical Analyzer details the extraction of 2,285 password entries from a Device. Crucially, many of these credentials, including one for “https://www.google.com/search?q=google.com,” are identified as originating from the “Google Password Manager.” The presence of file paths pointing to Chrome’s login_data and Login Data SQLite databases confirms that these are browser-saved passwords, providing significant insight into the user’s online accounts and activities.
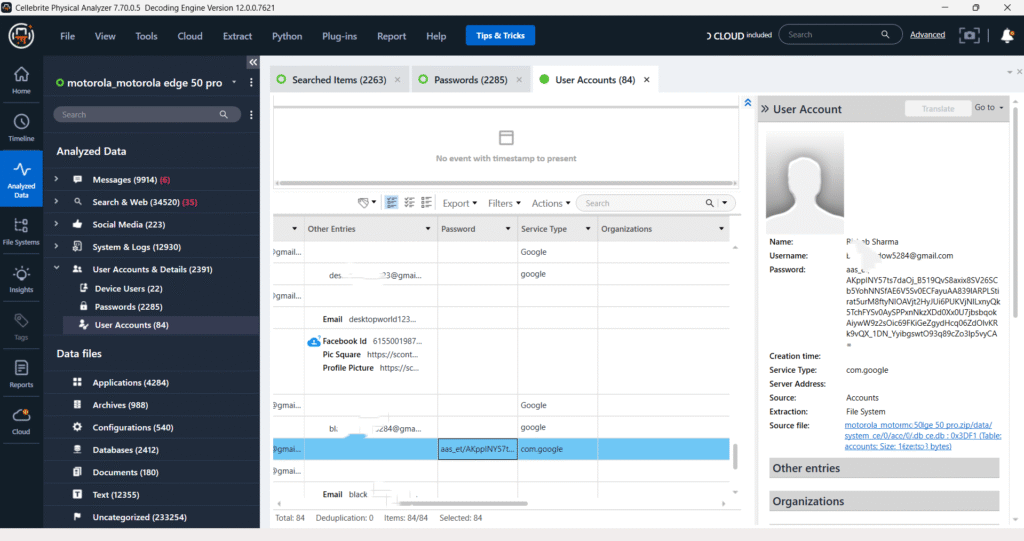
User Accounts & Details – User Accounts
The “User Accounts” section reveals 94 distinct user accounts, including Google and Facebook, linked to the device. Details like usernames and associated service types are displayed, alongside crucial metadata such as Android and Google IDs. While passwords are shown as obscured, their presence in the separate “Passwords” section, recovered from sources like Google Password Manager, completes the forensic picture of the device user’s digital identities and activities. Passwords are not in the plain text.
Generating Reports for Legal & Corporate Use
Once analysis is complete:
- Select relevant artifacts or entire datasets
- Export reports in:
- PDF (narrative and visual)
- Excel (structured)
- HTML or UFDR format (interactive)
All reports maintain chain-of-custody metadata and court-admissible formatting.
Conclusion
Full File System Extraction and Analysis of Android devices using Cellebrite UFED offers forensic investigators a deep look into digital behavior. With smartphones becoming central to both criminal and civil cases, mastering tools like UFED is essential for digital forensics professionals.
By following structured methods and maintaining forensic soundness, experts can uncover crucial evidence that might otherwise remain hidden.
Need Help with Mobile Forensics?
If you’re facing a case involving mobile data, chats, deleted files, or Android apps, our team can help you with professional forensic analysis using Cellebrite UFED. Contact us to learn more.

Thanks for this article, it helps a lot.
You’re very welcome! 😊 We’re glad to hear the article was helpful to you. Stay tuned for more informative content and practical insights from Xpert Forensics!
How can I download cellebrite UFDR reader as you used for making a ufdr file and make a report out of it for my project, I want to get a ufdr file for project purpose can you help me out ?
Either guide me for UFDR file or help me make a file from my device?
The Cellebrite UFDR Reader is specifically designed for viewing and creating reports from a .ufdr file, and it is available for free from Cellebrite.