Investigation Process
Understand the importance of computer forensics process
The rapid increase of cybercrimes has led to the development of various laws and standards that define cybercrimes, digital evidence, search and seizure methods, evidence recovery and the investigation process. The fragile nature of this evidence means that forensic investigators must be incredibly thorough to maintain its integrity and ensure it can be used in court.
Determine the phases involved in the investigation process

Pre-investigation Phase
- This crucial initial phase focuses on preparation before the actual investigation begins
- Involves setting up a specialized computer forensics lab, building a forensics workstation, developing an investigation toolkit, setting up an expert investigation team, getting approval from the relevant authority, etc.
Investigation Phase
- It’s the core of the process and involves handling digital evidence with extreme care.
- Involves acquisition, preservation, and analysis of evidentiary data to identify the source of crime and the culprit behind it.
Post-investigation Phase
- This final phase focuses on documenting the entire investigation process and presenting the findings in a clear and understandable manner
- Ensures that the report is well explicable to the target audience and provides adequate and acceptable evidence.
Understand the Pre-investigation Phase
During this phase, the investigation team collects all the necessary resources, documents, and tools required to conduct the investigation. This includes determining the required hardware, software, and other technical equipment, as well as legal clearance for conducting investigations.
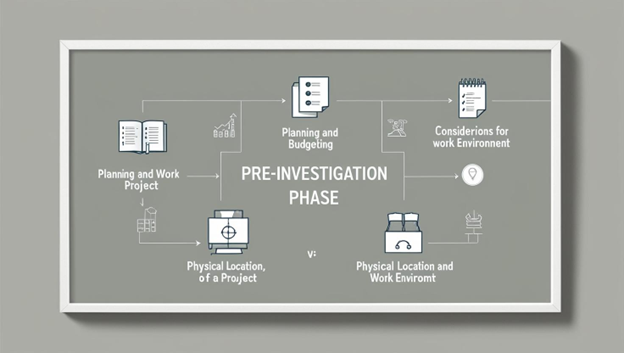
Establishing a forensics lab encompasses the following essential requirements:
Planning and budgeting
- The types of investigations to be prioritized, informed by analysis of previous year’s crime statistics and forecasts of future trends.
- Necessary software and hardware tools.
- Number of cases to be expected
- Numbers of investigators or examiners to be involved and their necessary training
- Forensic and non-forensic workstations requirements
- Safe locker to store and secure case original evidence
- LAN and Internet connection
- Space, equipment required, UPS and power supplies, etc.
- Storage shelves for unused equipment.
Physical location and structural design considerations
- Physical location requirements include convenient access to emergency services and a suitable site for the laboratory.
- Essential communication needs include a dedicated internet connection and multiple backup communication lines to ensure connectivity during emergencies.
- The environmental requirements include an appropriately sized room with good ventilation and effective air conditioning.
- Electrical requirements include a stable and reliable electricity supply, complemented by emergency power and lighting systems to ensure continuous operation.
Work Area Considerations
- The lab should be equipped with two forensic workstations and a general-purpose workstation with internet access or standard configuration.
- The specifications of the forensic workstations will be determined by the types of investigations conducted.
- The work area should have dedicated space for case discussions to take place among investigators.
- Investigators spend long hours in a forensics lab, so it is important to keep the lab environment comfortable.
- The lab’s design should consider factors like ceiling height, wall treatments, and flooring to enhance the overall atmosphere.
Physical Security Recommendations
- The lab should have a single point of entry to effectively manage access.
- An electronic sign-in/sign-out system should be implemented to record all visitor activity.
- All lab windows should remain closed and secured.
- An intrusion alarm system should be installed to provide an additional layer of security.
- A detailed visitor log should be maintained, including name, date and time of visit, purpose, and contact information.
- Guards should be deployed around the forensics lab premises.
- Visitors should be provided with identification badges to easily distinguish them from the lab staff and assigned personnel to guide them.
- Closed-circuit cameras should be placed in and out of the lab to monitor human movements.
Fire Suppression Systems
- Wet pipe system: Wet pipe sprinkler systems are constantly filled with pressurized water, providing immediate fire suppression.
- Dry pipe system: Dry pipe systems are used in areas subject to freezing temperatures. They use pressurized air to hold back water until a sprinkler is activated.
- Clean agent fire suppression system: Clean agent fire suppression systems are designed to minimize damage to sensitive equipment by using non-conductive and residue-free agents.
- Inert gas suppressors: Reduces the oxygen content to an extent where fire cannot be sustained
- Fluorine compound suppressors: Removes heat faster than it can be generated during ignition
- Chemical suppression systems: These systems use dry or wet chemicals to suppress fires, often targeting specific types of fires like those involving flammable liquids or cooking oils.
Evidence Locker Recommendations
- The containers used to store evidence must be secured and designed to prevent unauthorized access.
- They should be made of steel and equipped with a robust locking mechanism.
- All evidence containers must be monitored and always locked when not in use.
- The containers must be in a restricted area that is only accessible to lab personnel.
- There must be a limited number of duplicate keys so that authorized access is limited.
Auditing the Security of a Forensics Lab
- Regular audits should be conducted to ensure compliance with established security protocols.
- Forensics labs should be constantly under surveillance to protect it from intrusions or unauthorized access.
- Regularly inspect and maintain all fire safety equipment, including fire extinguishers.
- Conduct monthly inspections of the building’s structure, including ceilings, floors, roof, and exterior walls, to identify any signs of compromise.
- Examine the doors to ensure they are functioning correctly.
- Examine the log register to make sure all entries are accurate and complete.
Building a Forensics Workstation
The computer forensics workstation should have facilities and tools to:
- Support hardware-based disk cloning for local and remote drives.
- Ensure the ability to validate data integrity using cryptographic hashes.
- Provide tools to identify and analyze file metadata, including MAC times (MAC times refers to Modified, Accessed, and Created times).
- Identify the deleted files and recover them.
- Provide connectivity and software support for analyzing various removable storage devices.
- Offer tools for examining free space and unallocated clusters on storage devices.
Build a Computer Forensics Toolkit
Computer forensics tools can be divided into two types:
Hardware
- Specialized cables
- Write blockers
- Drive duplicators
- Media sterilization tools
- Other equipment that allows forensics software tools to work
Software
- Operating Systems
- Data discovery tools
- Password cracking tools
- Acquisition tools
- Data recovery tools
Build the Investigation team
- Maintain a small, tightly controlled team to minimize the risk of breaches of confidentiality.
- Identify team members and assign a responsibility to each team member to ensure accountability and efficient workflow.
- Ensure that every team member has the necessary clearance and authorization to participate in the investigation.
- Assign one team member as the technical lead for the investigation
People Involved in an Investigation Team
- Photographer: Captures visual documentation of the scene and evidence, adhering to forensic photography standards.
- Incident Responder: Responsible for initial containment and recovery efforts following an incident.
- Decision Maker: Responsible for authorization of a procedure for the investigation process.
- Incident Analyzer: Conducts root cause analysis and determines the extent of an incident.
- Evidence Examiner/Investigator: Conducts forensic analysis of digital or physical evidence.
- Evidence Documenter: Documents all the evidence and the phases present in the investigation process
- Evidence Manager: Ensures the proper handling and preservation of evidence to maintain its integrity and admissibility.
- Evidence Witness: Provides expert testimony in legal proceedings based on technical expertise.
- Attorney: Provides legal counsel and ensures compliance with relevant laws and regulations.
Forensics practitioner Certification and Licensing
- In the field of computer forensics, digital evidence plays an important role in tracking the perpetrator. The evidence must not be tampered with in any way from start to the end point of a forensics investigation process, for it to be admissible in the court of law.
- The success of a computer forensics lab depends on continuous learning, knowledge sharing, and investing in human resources.
- To ensure investigations are conducted properly, forensic practitioners require appropriate credentials, including:
Certification
- Most of the computer forensics laboratories expect job candidates holding a degree or certificate in the field of forensics science and crime scene investigations.
- Having a certificate in the field of digital forensics investigation validates both the extent of knowledge and the hands-on proficiency of an individual.
- Also, it is important for an individual to maintain their certification by staying up-to date in the field of digital forensics.
Licensing
- Many states and local law enforcement agencies require forensic practitioners to be licensed in accordance with the state’s licensing standards.
- To get a formal license, forensic practitioners must review the state’s licensing board regulations.
- Some states do not have specific licensing regulations but have a legal code of ethics set as criteria for digital forensics investigation.
Review Policies and Laws
- Understand the Laws: It is essential to understand the laws that apply to the investigation, including the internal organization policies before starting the investigation process
- Identify Possible Concerns: Identify possible concerns related to applicable Federal statutes such as the Electronic Communications Privacy Act of 1986 (ECPA) and the Cable Communications Policy Act (CCPA), both as amended by the USA PATRIOT ACT of 2001, and/or the Privacy Protection Act of 1980 (PPA), State statutes, and local policies and laws.
Forensics Laws
Given below are some of the forensics laws and rules specific to The United States of America:
- 18 USC §1029 – Fraud and related activity in connection with access devices
- 18 USC §1030 – Fraud and related activity in connection with computers
- 18 USC §1361-2 – Prohibits malicious mischief
- Rule 402 – General Admissibility of Relevant Evidence
- Rule 901 – Authenticating or Identifying Evidence
- Rule 608 – Evidence of character and conduct of witness
- Rule 609 – Impeachment by evidence of a criminal conviction
- Rule 502 – Attorney-Client privilege and work product; Limitations on waiver
- Rule 614 – Calling and interrogation of witnesses by court
- Rule 701 – Opinion testimony by lay witnesses
- Rule 705 – Disclosure of facts or data underlying expert opinion
- Rule 1002 – Requirement of original
- Rule 1003 – Admissibility of duplicates
Examination\Investigation Goals
- Investigators should have a clear idea about the goals of the examination prior to conducting the investigation.
- They should have an in-depth technical understanding about the inner workings of what is being examined.
Checklist to Prepare for a Computer Forensics Investigation
- Do not turn the computer off or on, run any programs, or attempt to access data on the computer. An expert should have the appropriate tools and expertise to prevent data overwriting and damage from static electricity.
- Secure any relevant media including hard drives, mobile phones, DVDs, flash drives, etc.
- Once the system is secured, obtain information about the system.
- If possible, obtain passwords to access encrypted or password-protected files.
- Compile a list of names, e-mail addresses, and other identifying information of those with whom the subject might have communicated recently.
- If the computer is accessed before the forensic expert can secure a mirror image, note the users who accessed it, what files they accessed, and when the access occurred.
- Maintain a chain of custody for each step of original media.
First Responder
- The term first responder refers to a person who first arrives at a crime scene and accesses the victim’s computer system once the incident has been reported.
- The first responder may be a network administrator, law enforcement officer, or a crime investigating officer.
- The first responder is responsible for protecting, integrating, and preserving the evidence obtained from the crime scene.
- The first responder should have complete knowledge and expertise of the investigation process and procedures and must investigate the crime scene in a lawful manner so that any evidence obtained is admissible in the court of law.
Roles of First Responder
As the first person to arrive at the crime scene, the first responder plays an important role in computer forensics investigation. The main responsibilities of first responders are described below.
- Identifying Crime Scene: After arriving at the crime scene, the first responder identifies the scope of the incident and establishes the perimeter. The first responder begins listing the computer systems involved in the incident that could be used to collect as digital evidence.
- Protecting Crime Scene: The first responder secures all electronic devices and prevents access until a search warrant or other legal authorization is obtained.
- Preserving Temporary and Fragile Evidence: In the case of temporary and fragile evidence such as a running program that could change or disappear, the first responder does not wait for the case officer in charge; they take photographs of all evidence.
- Collecting Information About the Incident: The first responder conducts preliminary interviews with all persons present at the crime scene to gather the initial details of the incident.
- Documenting All Findings: The first responder documents all information about the collected evidence in the chain of custody document.
- Packaging and Transporting Electronic Evidence: Evidence is packaged in appropriate containers designed to protect against physical damage, environmental factors, and electromagnetic interference, and then transported securely to the forensic lab.
- Gathering Preliminary Information from Crime Scene: At the time of an incident, the first responder secures the crime scene and surrounding areas to avoid evidence tampering. Preliminary information on the incident provides the basis for forensic investigations; moreover, evidence collection becomes easier in the absence of third-party interference.
First Responder Common Mistakes
when a computer crime incident occurs, the system or network administrator assumes the role of the first responder at the crime scene so he or she might make the following common mistakes:
- Shutting down or rebooting the victim’s computer. In this case, all volatile data is lost.
- Didn’t maintain the chain of custody.
- Not documenting the data collection process.
Investigation Phase
Documenting the Electronic Crime Scene
- Documentation of the electronic crime scene is a continuous process during the investigation that creates a permanent record of the incident.
- The incident should be documented in detail and comprehensively at the time of the investigation.
- Record the state of computer systems with their plugged cables, digital storage media, and electronic devices, including the power status of the computer.
- Take a photograph of the computer monitor’s screen and note what was on the screen.
Photographing the Scene

- On arrival, the first step taken by the forensics team should be to photograph the crime scene.
- It should be done in a way that will not alter or damage the crime scene, and everything should be clearly visible
- The best course of action is to take photographs from various angles of the crime scene.
- It is important to proceed all the way from the entire crime scene down to the smallest piece of evidence.
- Crime scene photographs should be taken of the work area, including equipment such as computer disks, handwritten documents, and other components of the system.
- Photos should also be taken of the back of the computer system to accurately show how cables are linked and what devices are connected to the systems.
- If this cannot be done on-site, then all cables must be labeled so the computer system can be reconnected at the forensics laboratory and photographed.
Conducting Preliminary Interviews
- Identify the persons present at the incident, conduct individual interviews, and note everyone’s physical position and his or her reason for being there.
- As part of the investigation process, first determine whether the suspect has committed a crime or has violated any departmental policies.
- Adhering to departmental policies and applicable laws, collect information and gather evidence from individuals such as:
- Web mail and social networking website account information
- Any off-site data storage
- Documents explaining the hardware or software installed on the system
- Actual holders and users of any electronic devices present at the incident
- Usernames and their Internet service providers
- Passwords required to access the system, software, or data
- Purpose of using this specific system
- If the suspect is present at the time of the search and seizure, the incident manager may consider asking some questions.
- If the system administrator is present at the time of the initial interview, he or she may help provide important information such as how many systems are involved, who is associated with a particular account, and what the relevant passwords are
- A person having physical custody of evidence is responsible for the safety and security of that evidence.
- Whenever possible, evidence must be secured in such a way that only a person with complete authority is allowed access.
Planning the Search and Seizure
A search and seizure plan should contain the following details:
- Description of the incident
- Incident manager dealing with the incident
- Case name of the incident
- Location of the incident
- Location of the equipment to be seized:
- Structure type and size
- Where the electronic devices are located
- Who was present at the incident?
- Details of what is to be seized (make, model, location, ID, etc.):
- Type of device and number
- If the seized computers were running or powered down
- Whether the computers were networked? If so, what type of network, where data is stored on the network, where the backups are held, if the system administrator is cooperative, if it is necessary to take the server down.
Obtain Search Warrant
A search warrant is a written order issued by a judge that directs a law enforcement officer to search for a particular piece of evidence at a particular location
- If agents remove the system from the premises to conduct the search, should they return the computer system, or copies of the seized data, to its owner before trial?
- To carry out an investigation, a search warrant from a court is required
- Warrants can be issued for an entire company, a floor, room, device, car, house, or any company- owned property.
- Is it practical to search the computer system on site, or must the examination be conducted at a field office or laboratory?
- Where will this search be conducted?
Searches Without a Warrant
In certain situations, a search without a warrant may be allowed:
- When destruction of evidence is imminent, a warrantless seizure of that evidence is justified if there is probable cause to believe that the item seized constitutes evidence of criminal activity.
- Agents may search a place or object without a warrant or, for that matter, without probable cause, if a person with authority has consented.
Collect Physical Evidence
- The physical evidence includes removable media, all computer equipment, items taken from the trash.
- Collect electronic devices or any other media found at the crime scene
- To preserve the integrity of the physical evidence, all the pieces of evidence collected should be handled carefully
- The objects identified as evidence should be tagged and the tag provides detailed information about the evidence.
Dealing with Powered on Computers
- When dealing with a powered-on computer, the investigator should content the RAM information. For example, data that is encrypted on the hard disk may be unencrypted in the RAM. Also, running process information is stored in the RAM.
- All this information will be lost when the computer is shut down or when the power supply is removed
- If a computer is switched on and the screen is viewable, the investigator should photograph the screen, and document the running programs
- If a computer is on and the monitor shows a screensaver, the investigator should move the mouse slowly without pressing any mouse button, and then photograph and document the programs.
Dealing with Powered Off Computers
- If the computer is switched off – leave it in that state
- If only the monitor is switched off and the display is blank:
- Turn the monitor on, move the mouse slightly, observe the changes from a blank screen to another screen, and note the changes
- Photograph the screen
Note: If the screen does not change on moving the mouse slightly, do not press any keys
Dealing with Networked Computer
- Unplug the network cable from the router to prevent further attacks
- Photograph all devices connected to the victim’s computer such as a router, printer or scanner, take photographs of those devices as well.
Dealing with Open Files and Startup Files
When malware attacks a computer system, some files are created in the startup folder to run the malware program. The first responder can get information from these files.
- Open any recently created documents from the startup or system32 folder in Windows
- Document the date and time of the files and examine the open files for sensitive data such as passwords or images
- Search for unusual MAC (modified, accessed, or changed) times on folders, and startup files
Operating System Shutdown Procedure
- It is important to shut down the system in a manner that will not damage the integrity of any files
- Different operating systems have different shutdown procedures
- Windows 10, Windows 8.1, Windows 7, Windows Server 2012, Windows Server 2008
- Take a photograph of the screen
- Document any running programs and shut down.
- Mac OS X Operating System
- Record the time from the menu bar
- Click the apple logo then Shutdown.
Preserving Electronic Evidence

Steps that should be taken to preserve electronic evidence:
- Document the actions and changes observed in the monitor, system, printer, and other electronic devices
- Verify whether the monitor is on, off, hibernate mode or in sleep mode
- Remove the power cable if the device is off. Do not turn the device on
- Photograph the connections between the computer system and related cables, and label them individually
- For handheld devices such as cell phones, tablets, and digital cameras:
- Leave the device as it is if it is on
- Photograph the screen display of the device
Dealing with Smartphones or Other Handheld Devices
Special considerations are required when dealing with smartphones or other handheld devices during the collection of digital evidence.
- Photograph the device and its screen display
- Capture any volatile data on screen; incoming messages, call logs, or active applications can be time sensitive
- Collect information on whether any security features are enabled on the device such as pass patterns, passwords, or biometrics lock.
- Tag the evidence and note all important details of the seized item in the search and seizure evidence log.
- Keep the device charged as evidence might be lost if the device is turned off
- Enable flight mode to disable all network connections and preserve battery
- Place the device in a Faraday bag to block any signals that could erase data from the device
- Many handheld devices have external storage options such as microSD cards. These should be treated as separate pieces of evidence with proper documentation and packaging.
- SIM cards contain valuable data such as contacts and text messages. They should be carefully removed, documented, and stored separately.
- Modern smartphones often synchronize data using cloud services. Determine whether there is a need to collect evidence from associated cloud accounts.
- Smartphones have numerous applications, each of which provides valuable evidence. Consider specialized forensic tools or techniques for app-specific data extraction.
- Maintain a detailed chain of custody log for the device, noting all interactions, examinations, and transfers.
Evidence Management
- Evidence management helps in protecting the true state of the evidence by proper handling and documentation of the evidence.
- At the time of evidence transfer, both sender and receiver need to provide the document to uniquely identify any evidence and a chain of custody record.
Packaging and Transporting Electronic Evidence
Packaging Electronic Evidence
- Make sure the gathered electronic evidence is correctly documented, labeled, and listed before packaging.
- Pack magnetic media in antistatic packaging because they may produce static electricity.
- Make sure that all containers that contain evidence are labeled in the appropriate way.
Transporting Electronic Evidence
- Keep the electronic evidence collected from the crime scene away from magnetic sources such as radio transmitters and magnets.
- Store the evidence in a safe area.
- Maintain proper chain of custody on the evidence that is to be transported
Storing Electronic Evidence
- Store the electronic evidence in a secure and weather-controlled environment
- Protect the electronic evidence from magnetic fields, dust, vibrations, and other factors that may damage its integrity
Duplicate the Data (Imaging)
- Make a duplicate of the collected data to preserve the original and the data should be duplicated bit by bit to represent the same original data.
- Use industry standard or licensed hardware or software tools to duplicate the data
- Once a copy of the original data is made and verified, you can use the copy for further processing.
Verify Image Integrity
- Calculate the hash value of the original data and the forensic image generated, if there is a match it means that the forensic image is an exact replica of the original data.
- Tools for calculating hash value: HashCalc, MD5 Calculator, HashMyFiles
Recover Lost or Deleted Data
- Collect Data
- After committing a crime, a criminal usually deletes the files he or she used as a part of removing the traces of crime as an investigator, try to recover the lost or deleted files in the internal and external devices.
- Software used to recover the data (Data Recovery Tools)
- Forensic Toolkit
- Recuva
- EASEUS Data Recovery Wizard
Data Analysis

- Thoroughly analyze the acquired data to draw conclusions related to the case
- Data analysis techniques depend on the scope of the case or the client’s requirements
- This phase includes analysis of the file’s content, date and time of file creation and modification, users associated with file creation, access and file modification, and physical storage location of the file
- Forensics tools help in sorting and analysis of a large volume of data to draw meaningful conclusions
- Examples of data analysis tools: AccessData’s Forensic Toolkit (FTK), Guidance Software’s EnCase Forensic, Brian Carrier’s The Sleuth Kit (TSK).
Processing Location Assessment
- It is preferable to complete the examination in a controlled environment, such as dedicated forensics work area or laboratory
- Assessment considerations include:
- The impact on the business due to a lengthy search
- The suitability of the equipment, resources, media, training, and experience for an on-site examination
Collecting Evidence from Social Media
Social media forensics depends on limited set of data sources as acquiring the server’s hard drives is not possible and getting data needs the service operator’s cooperation
- Social media sites and apps such as Facebook, LinkedIn, Twitter, Google+, WhatsApp, Snapchat, etc. are widely being used nowadays for communication and information sharing purposes, because of which attacks through them are also increasing. Thus, social media sites and apps can be a treasure trove for forensics investigations to track a perpetrator.
- The information gathered from social media might help a forensic investigator to build a timeline of an attack.
- Generic data of interest for forensics investigations on social media networks or apps:
- The social footprint:
- Communication pattern
- Pictures and Videos
- Times of Activity
- Apps
- All the above information is solely stored by the social network operator
Social media websites create footprints in RAM, browser cache, page files, unallocated clusters, and system restore point of a computer.
Post-Investigation Phase

Writing the Investigation Report
Report writing is a crucial stage in the outcome of the investigation and the report should be clear, concise, and written for the appropriate audience
Information included in the report section is:
- Purpose of Report: Clearly explain the objective of the report, the target audience, and why the report was prepared
- Author of Report: List all authors and co-authors of the report, including their positions, responsibilities during the investigation, and contact details
- Evidence: Provide descriptions of the evidence that was acquired during the investigation
- Incident Summary: Introduce the incident and explain its impact; the summary should explain clearly what the incident was and how it occurred
Details
- Provide a detailed description of what evidence was analyzed and the analysis procedures that were used and explain the findings of the analysis.
- Include proof of your findings, such as utility reports and log entries.
Conclusion
- Summarize the outcome of the investigation and the conclusion should be clear and unambiguous.
Supporting Documents
- Include any background information referred to throughout the report, such as network diagrams and documents that describe the computer investigation procedures used, and overviews of technologies that are involved in the investigation and it is important that supporting documents provide enough information for the report reader to understand the incident comprehensively.
Testifying in the Court Room
Presenting digital evidence in court requires knowledge of new, specialized, evolving, and sometimes complex technology.
Closing the Case
- The final report should include everything the investigator did during the investigation, and what he or she found.
- The report should explain the computer and network processes, and should include the log files generated by the forensics tools to keep track of all the steps taken
- He or she should document all the proceedings related to the investigation so that the documentation can be used as proof of findings in a court of law
Maintaining Professional Conduct
- Consider all available facts that relate to the crime scene
- Follow these criteria to maintain professional conduct:
- Credibility
- Ethics and morals
- Standards of behavior
- Maintain objectivity and confidentiality
- Enriched technical knowledge
- Conduct with integrity
1. CHFI Ec-Council ebook
