Case Studies
Explore our confidential case studies where Xpert Forensics uncovered digital fraud, insider threats, data leaks, and cyber misconduct using advanced forensic tools and investigative techniques. Each case reflects our commitment to precision, discretion, and delivering actionable insights that drive resolution.
Telegram Data Extraction & Backup Explained | Digital Forensics Investigation Guide
Introduction
Telegram has become a critical source of digital evidence in modern investigations involving cybercrime, financial fraud, extremist communication, drug trafficking, data leaks, and organized crime.
From a forensic perspective, Telegram differs significantly from applications like WhatsApp or Signal due to its cloud-centric architecture and selective end-to-end encryption.
This article provides a detailed, step-by-step explanation of:
- How Telegram data is stored
- How investigators can export, extract, or backup Telegram data
- Tools used in real investigations
- Key artifacts
- Limitations and legal challenges
Why Telegram Data Is Important in Investigations
Telegram evidence may contain:
- Private and group chats
- Media files (images, videos, documents)
- Channels and broadcast messages
- Contact lists and usernames
- Timestamps and metadata
- Deleted messages (in limited cases)
Telegram’s cloud-based architecture allows access across devices, but also introduces forensic challenges.
Telegram Data Storage Architecture (Forensic Overview)
Before attempting any extraction, investigators must understand how Telegram stores data.
Cloud Chats (Default Chats)
- Stored on Telegram servers
- Accessible from multiple devices
- Includes:
- One-to-one chats
- Group chats
- Channels
- Not end-to-end encrypted by default
This makes cloud chats exportable using authorized login methods.
Secret Chats (End-to-End Encrypted)
- Enabled manually by users
- Stored only on the device
- Not synced to cloud
- Cannot be accessed from another device
Forensic Impact
Secret chats:
- Cannot be exported via Telegram Desktop
- Are usually irrecoverable once deleted
- Require live device access
Media Storage
Media may exist in:
- Telegram cloud
- Device cache
- External storage (Android)
This dual storage creates partial recovery opportunities during mobile forensic analysis.
Telegram Desktop Export (Official & Court-Safe Method)
This is the most reliable and legally defensible method.
Tool Used
- Telegram Desktop (Official Application)
Preconditions
- Valid mobile number
- OTP / Telegram verification code
- Consent or legal authorization
Step-by-Step Export Process
- Install Telegram Desktop
- Login using mobile number
- Verify OTP received on registered device
- Navigate to:
Settings → Advanced → Export Telegram Data - Select export categories:
- Account information
- Contact list
- Story archive
- Music on Profiles
- Personal Chats
- Private chats & channels (Untick the only my messages)
- Public chats and channels (only my messages can export)
- Photos, videos, voice & video messages, Files (set the size limit to 4000 MB)
- Miscellaneous data
- Choose format:
- HTML – Human-readable
- JSON – Forensic analysis
- Select Both
7. Start export and document
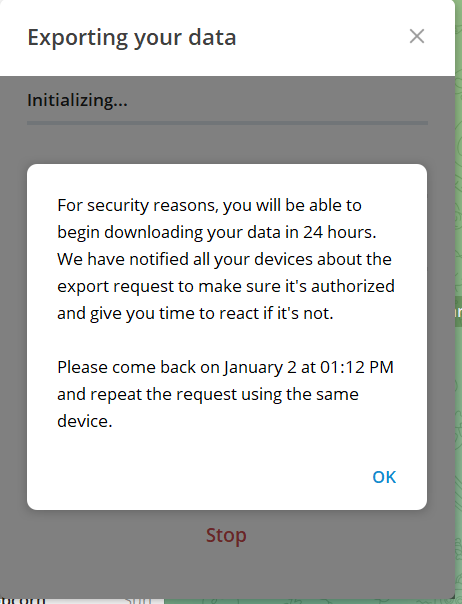
Note: You will receive this type of message (See the below image), click OK. Check the mobile phone where Telegram is login, Go to Chats – Telegram and allow the request. After this you can Export the Telegram Data.
Forensic Artifacts Generated
- Message content
- Sender & receiver usernames
- Message timestamps (UTC)
- Media files with original metadata
- Group and channel identifiers
- Message IDs (valuable for correlation)
Forensic Advantage
Telegram export preserves message sequence and metadata, making it court-admissible when properly documented.
Best for: Consent-based investigations, corporate cases, internal inquiries, training.
Limitations & Challenges in Telegram Forensics
Investigators must clearly understand:
- Secret chats are unrecoverable
- Deleted cloud data cannot be restored
- Strong encryption limits content visibility
- Telegram rarely cooperates with LEAs
- Phone numbers may be hidden
- Session hijacking is illegal and inadmissible
Legal & Court Considerations (India)
- Follow IT Act, 2000
- Obtain:
- User consent OR
- Court warrant
- Maintain Chain of Custody
- Hash exported data (MD5/SHA-1/SHA-256)
- Document:
- Tool versions
- System timestamps
Conclusion
Telegram data extraction requires a different forensic mindset compared to traditional messaging apps. Investigators must rely on official exports & mobile forensic tools while respecting encryption and legal boundaries.
Proper documentation and understanding Telegram’s architecture ensures court-admissible and defensible digital evidence.
How Xpert Forensics Can Help
At Xpert Forensics, we specialize in uncovering hidden digital trails, whether it’s corporate fraud, insider threats, or data breach investigations. Our certified forensic investigators use industry-leading tools and methodologies to ensure that every byte of evidence is discovered, validated, and reported.
Need expert digital forensic support or training?
📩 Feel free to connect with us today. | Email: service@xpertforensics.in
