Case Studies
Explore our confidential case studies where Xpert Forensics uncovered digital fraud, insider threats, data leaks, and cyber misconduct using advanced forensic tools and investigative techniques. Each case reflects our commitment to precision, discretion, and delivering actionable insights that drive resolution.
In-depth guide on analyzing Google Chrome browser artifacts using MAGNET AXIOM, focusing on selective RAW extraction, forensic timelines, user intent, and evidential value.
Learn how to change the iTunes iPhone backup location when the C drive has low storage. Simple, step-by-step guide for students and digital forensic investigators.
Understand Telegram backup and extraction techniques for investigations. Covers cloud chats, mobile artifacts, tools, and court considerations.
Learn how to acquire Outlook mailboxes in a forensically sound manner for legal and corporate investigations. This guide covers evidence-grade extraction methods, supported tools, data preservation, and best practices to ensure integrity and court admissibility.
Learn how to extract Gmail and Outlook emails using Mozilla Thunderbird with a complete forensic, step-by-step guide. Covers IMAP setup, offline email preservation, MBOX extraction, PST import, and forensic best practices for investigations, e-discovery, and legal evidence.
Learn how digital forensic investigators extract Gmail data using Google Takeout. Step-by-step procedures, export options, hashing & chain-of-custody best practices.
Discover the fastest and most reliable forensic method to calculate a folder hash using Windows CMD. Learn how the FSUTIL + CertUtil technique ensures accurate, repeatable, and lightning-fast results for digital investigations.
Accidentally imaged a BitLocker-encrypted drive? Learn how to retrieve the BitLocker recovery key using CMD to unlock forensic evidence.
Learn how digital forensics experts detect iPhone spyware using Cellebrite and iMazing. Step-by-step guide to forensic extraction, backup analysis, and spyware detection techniques.
Learn how to recover deleted photos, videos, WhatsApp chats, documents, and call logs from Android phones using Cellebrite UFED’s Full File System Extraction. Includes a real case study where 100% of deleted data was successfully recovered.
Learn why iPhone data extractions require almost double the storage space. Understand encryption, APFS snapshots, media files and best practices for efficient mobile forensics analysis.
Learn how Magnet AXIOM simplifies social media forensics by extracting and analyzing Facebook and Instagram data to solve cybercrime cases effectively.
Learn how to efficiently download, process, and analyze Instagram data using Magnet AXIOM for digital investigations. Discover key insights from chats, media, and account activity to strengthen your social media forensics workflow.
Discover how to perform Windows forensics using Magnet AXIOM. Learn imaging, evidence processing, and digital analysis for global investigations.
Discover the key differences between deleted and carved data in digital forensics, and learn how each recovery method helps retrieve critical evidence.
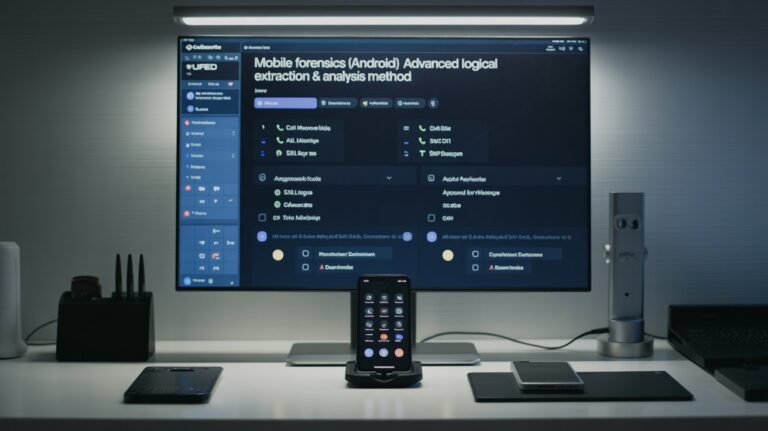
Explore Android mobile forensics using Cellebrite UFED. Learn advanced logical extraction techniques and data analysis methods for digital investigations.
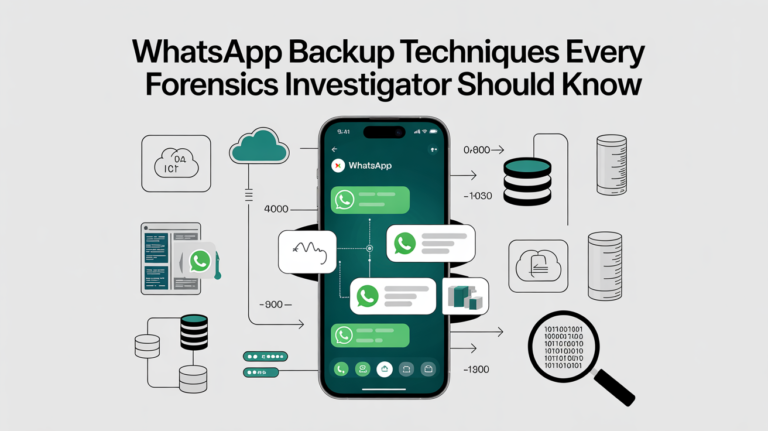
Discover the complete guide to WhatsApp backup methods for Android, including cloud and local backups. Learn how deleted chats can be recovered and why these techniques are essential for digital forensic investigations.
Unlock deep Android mobile data with Cellebrite UFED. Learn full file system extraction and forensic analysis techniques for digital investigations, law enforcement, and cybersecurity cases.
We investigated an accident image submitted for an insurance claim using forensic tools like metadata analysis, ELA, and deepfake detection.
Using advanced forensic techniques, we analyzed a suspect Windows system to uncover hidden evidence of fraud and tampering. This case reveals how digital forensics tools exposed the truth behind manipulated data and deceptive activity.