Mobile Forensics
Why Mobile Forensics?
- Using mobiles for money transactions
- Internet connections made via mobile devices
- Number of malware’s targeting mobile devices
- Among all the malwares, ransomware malwares capable of obtaining unlimited rights on an infected device, and data stealers proved to be the most dangerous threats

Mobile Device Forensics
- Mobile phone forensics is the science of recovering digital evidence from a mobile phone under forensically sound conditions
- It includes recovery and analysis of data from mobile devices internal memory, SD cards and SIM cards
- The goal of mobile forensics is to identify the criminals responsible for crimes involving mobile phones.
Top Threats Targeting Mobile devices
Web and Network based Attacks
- Launched by malicious websites or compromised trustworthy websites.
- Targeting websites that take advantage of the browser on a device.
- Attempts to install malware or steal confidential data that passes through the browser
Malware
- Includes traditional computer viruses, computer worms and Trojan horse programs
- Example: IKee worm, targeted IOS-based devices
- Example: Pjapps enroll infected Android devices on the botnet
Social Engineering Attacks
- Leverage social engineering to trick users
- Attempts to get users to disclose sensitive information or install malware
- Examples include phishing and targeted attacks
Resource Abuse
- Attempt to misuse network, device or identity resources
- Example: Sending spam from compromised devices
- Example: Denial of Service attacks using computer resources of compromised devices Malware
Data Integrity Threats
- Attempts to corrupt or modify data
- The purpose is to disrupt operations of an enterprise or geared toward financial gain
- Can also occur unintentionally
Data Loss
- The biggest hazard to mobile devices is when an employee or hacker steals confidential data from a device or network, wither maliciously or accidentally.
SMiShing: SMS phishing is a type of phishing scam in which an attacker uses SMS to send text messages containing misleading links to malicious websites or telephone numbers to a victim. The attacker tricks the victim into clicking the link or calling the phone number and revealing their personal information such as credit card number, and online banking username and password.
No passcode/weak passcode: Many users choose not to set a passcode or use a weak PIN, passcode, or pattern lock, which an attacker can easily guess or crack to compromise sensitive data stored in the mobile device.
iOS jailbreaking: The technique of removing the security measures put in place by apple to stop malicious code from operating on the device is known as iOS jailbreaking. It provides root access to the OS and removes sandbox restrictions. Thus, jailbreaking involves many security risks as well as other risks to iOS devices, including poor performance, malware infection, and so on.
Android rooting: Rooting allows Android users “root access” or privileged control to Android’s subsystem. Like jailbreaking, rooting can result in the exposure of sensitive data stored in the mobile device.
Mobile Hardware and Forensics
- Mobile device forensics is highly dependent on the underlying hardware of mobile devices
- Investigators need to take different approaches for mobile forensics depending upon the mobile hardware architecture
- Hardware of mobile devices makes forensics acquisition difficult
- Knowledge of mobile hardware also becomes essential in case of a broken or damaged device when it is not possible to access device using data ports
Mobile OS and Forensics
- A mobile operating system controls the functions and features available on mobile devices, and manages the communication between the mobile device and other compatible devices
- This diversity in the mobile OS architecture may impact forensics analysis process
- Investigators require knowledge of underlying OS, architecture, and file systems of mobile device under investigation
- Knowledge of mobile OS booting process helps investigator to gain lower-level access
Mobile Forensics Challenges
The following are the various challenges involved in mobile forensic investigations:
- Mobile devices use various Operating Systems, storage types, and data structures, requiring investigators to learn several acquisition techniques and forensic tools.
- Investigators find it challenging to bypass the built-in security features such as PIN, passcode, pattern, fingerprint, etc. to access the protected data on mobile devices.
- As cloud-related data are saved on cloud storage instead of mobile devices, acquiring it is difficult due to legal constraints and requires specialized tools.
- Remote command executions could erase the evidence from mobile devices if they are not protected by being isolated from other networks.
- Jailbreaking or rooting the devices while performing physical data acquisition might lead to data loss or device booting.
- Anti-forensics techniques such as data wiping, data forgery, data hiding, and data deletion on many incorrect password attempts complicate the forensic investigation.
- As mobile devices are subjected to frequent updates and modifications, there is a possibility of data deletion or overwriting.
- There is a risk of loss of valuable volatile data when the device turns off during live data capturing.
- Investigators may encounter restricted access to devices or certain types of data due to the laws relating to privacy concerns and difficulty in obtaining consent to access.
- The evolving nature of technologies and cyber-attacks makes forensic investigations time-consuming and requires expensive, specialized tools and training.
- The incompatibility of various forensic tools with certain devices and data types can cause obstructions in the data-recovery process.
Understand Android and iOS Architecture, Boot Process, and File Systems
Mobile Device Architecture
The mobile architectural layer is a platform that enables mobile Operating Systems, applications, and mobile device hardware to work in coordination for successful operation on devices such as cellular phones, and smartphones.

Android OS Architecture
Android is a Linux-based OS designed for portable devices such as smartphones and tablets. It is a stack of software components categorized into six sections (System Apps, Java API Framework, Native C/C++ Libraries, Android Runtime, Hardware Abstraction Layer (HAL), and Linux kernel) and five layers.
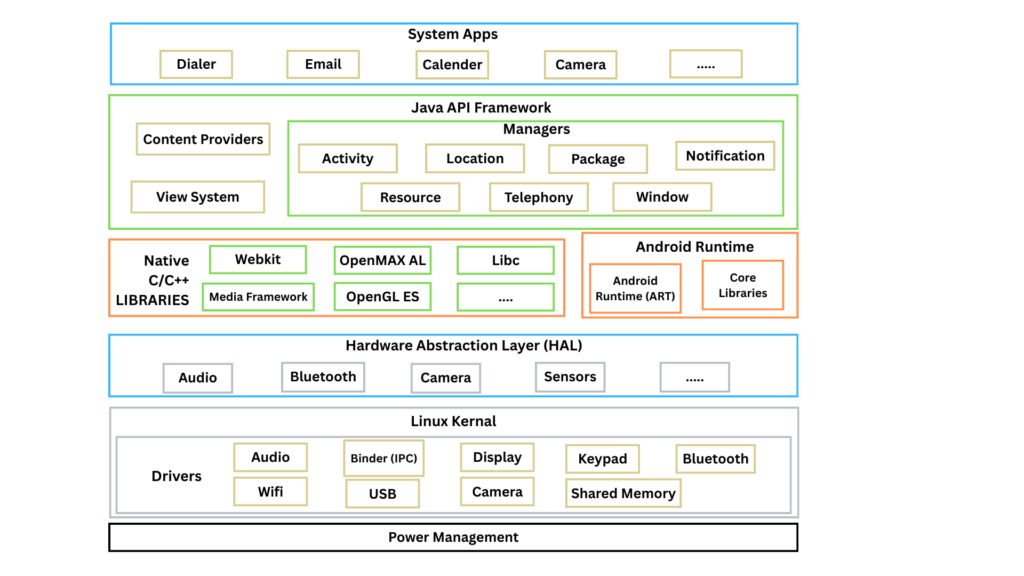
System Apps: All Android system applications are at the top layer. Any app developed should fit into this layer. Some standard applications that come pre-installed with every Android device include the dialer, email, calendar, camera, SMS messaging, web browsers, contact managers, and so on. Most Android apps are written in Java.
Java API Framework: The Android platform functions are made available to developers through APIs written in Java. The application framework offers many high-level services to applications, which developers incorporate into their development.
Android Boot Process
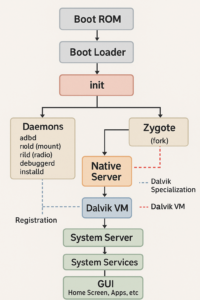
Step 1: When we power on an Android device, the Boot ROM code gets activated. This loads the boot loader into the device RAM and starts execution.
Step 2: Boot Loader is a program that is initialized before the Android OS is loaded. The boot loader sets up all essential services such as network and memory that are required to start the kernel. The location of the boot loader is given below: <android source>\bootable\bootloader\legacy\usbloader The original equipment manufacturers customize the boot loader to put their locks and restrictions on a device.
Step 3: The initialization process of the Android kernel is the same as that of the Linux kernel. It sets up everything required for the system to run. As the kernel starts, it initializes the interrupt controllers, setups memory protections, caches, and scheduling.
Upon successful initialization, the system can use virtual memory and launch the user space processes. The kernel then looks for the init process (under system/core/init) and launches it as the initial user space process.
Step 4: Init is the first user process that runs on a device. It is the parent of all processes and resides at the following address: <android source>/system/core/init init initializes the Zygote, runtime, and daemon processes; at this instance, the Android logo appears on the mobile screen. The init process is responsible for:
- Mounting directories such as /sys, /dev, or /proc
- Running the init.rc script located at <android source>/system/core/rootdir/init.rc
The init.rc script describes the system services, file system, and other parameters that must be set up.
Step 5: In Java, when a new app is launched, a separate VM instance occurs in the memory. Therefore, if multiple applications are launched simultaneously, multiple Dalvik virtual machine (DVM) instances occur, resulting in extensive memory and time consumption.
To avoid this, Android implements a system called “Zygote,” which enables code sharing across the DVM, resulting in low memory consumption and quick startup time.
Zygote is a VM process that is launched during system boot. It preloads and initializes the core library classes. When a new app is launched, Zygote forks a new VM and runs the app in its sandboxed environment. It provides a pre-warmed up VM instance for each APK to run, thereby reducing the startup time. In simple terms, the init process initializes the Zygote, which in turn initializes the DVM.
Step 6: After the completion of step 5, the runtime requests Zygote to launch the system server, which initializes services such as the power manager, battery service, and Bluetooth service.
The system server is the first Java-based component to launch on the device during the bootup sequence. The Android boot process is completed when all services are up and running on the device.
iOS Architecture
iOS is Apple’s mobile OS that supports Apple devices such as the iPhone, iPod touch, iPad, and Apple TV. iOS manages the device hardware and offers various technologies required to implement native apps. At the highest level, iOS acts as an intermediary between apps and the underlying hardware. Apps communicate with the underlying hardware via a set of well-defined system interfaces. The UI is based on the concept of direct manipulation, using multi-touch gestures.

The iOS architecture comprises five layers: Cocoa application, media, core services, core OS and kernel, and device drivers. The lower-level layers contain fundamental services and technologies, whereas the higher-level layers build upon the lower layers to provide more sophisticated services and technologies.
- Cocoa Application: This layer contains key frameworks that help in building iOS apps. These frameworks define the appearance of the apps, offer basic app infrastructure, and support key technologies such as multitasking, touch-based input, push notifications, and many high-level system services. Cocoa apps use the AppKit framework.
- Media: This layer contains the graphics, audio, and video technologies that enable multimedia experiences in apps.
- Core Services: This layer contains fundamental system services for apps. The key services are Core Foundation and Foundation frameworks (which define the basic types that all apps use). Individual technologies that support features such as social media, iCloud, location, and networking belong to this layer.
- Core OS: This layer contains low-level features on which most other technologies are based. Frameworks in this layer are useful when dealing explicitly with security or communicating with external hardware and networks. The services provided by this layer are dependent on the Kernel and Device Drivers layer.
- Kernel and Device Drivers: The lowest layer of the iOS architecture includes the kernel, drivers, BSD, file systems, infrastructure technologies such as networking.
iOS Boot Process
The iPhone boot process involves two boot modes. Depending on the purpose, an investigator should select the boot mode to be used while performing data acquisition on iOS devices.
- Device Firmware Upgrade Mode: This mode is part of bootROM, which is written into the hardware. It allows all devices to be restored from any state. Investigators can use iOS Forensic Toolkit to retrieve information such as device model and ECID/UCID (Exclusive Chip ID/Unique Chip ID) from the Device Firmware Upgrade (DFU) mode.
The importance of DFU mode from a forensics perspective varies based on the device model. Forensically, the DFU mode has the following importance:
- It allows the extraction of device information without cracking the passcode
- It allows investigators to bypass the USB restricted mode; however, it only grants access to limited information
- Recovery Mode: This mode is also known as the second-stage loader; it boots a device in the iBoot mode. The iBoot mode helps in upgrading a device to a new version of the OS. From a forensic perspective, investigators can use recovery mode to extract a limited but valuable set of artifacts.
Through recovery mode, investigators can retrieve information such as the device model, ECID/UCID (which represents the unique identification for each system on chip processor), serial number, and IMEI number.
Booting iPhone in DFU Mode
DFU is a part of bootROM, which is burned into the hardware. In iPhones, entering the DFU mode is a complicated procedure that involves a sequence of pressing, holding, and releasing buttons. When a device enters the DFU mode, its screen becomes blank. The procedure to enter the DFU mode varies depending on the iPhone model.
The main reason for connecting a device in the DFU mode is to change the firmware of the mobile phone. Using the DFU mode, users can downgrade the OS and firmware or use custom firmware. Generally, jailbreaking devices or SIM unlocking devices use this procedure.
Steps involved in booting an iPhone in DFU Mode (For A17 and later devices):
- Connect the iPhone to the workstation via a USB cable
- Quickly press and release the Volume Up button
- Quickly press and release the Volume Down button
- Press and hold the Side button until the screen goes black
- Continue holding the Side button and press the Volume Down button for 5 s; then, release the Side button
- The screen remains black, which is a clear indication that the iPhone is in DFU mode. iTunes (on Mac) will alert the user that it has detected an iPhone in recovery mode.
Note: The boot process of DFU mode varies depending on the iPhone’s processor used.
Booting iPhone in Recovery Mode
To boot the iOS device into recovery mode, connect the device to the computer (Mac) and open iTunes.
Steps involved in booting an iPhone in recovery Mode (for A17 and later devices):
- Press and release the Volume Up button, followed by the Volume Down button
- Press and continue holding the Side button until the device goes into recovery mode
Note: The boot process of recovery mode varies depending on the iPhone’s processor used.
Android File System
Android file system structure shares similarities with Linux as it is a framework built on top of the Linux kernel but has some unique characteristics. This file system is disk-based, and it has two storage areas: Internal and External. Internal storage is built-in and non-volatile memory, which is permanent and holds the operating system, application data, caches, and user files. External storage is physically mountable like a microSD card can be inserted into its slot, and other devices such as pen drives and hard disks can also be connected to the USB port using on-the-go (OTG) cables.
Android File System Hierarchy
The Android file system has partitions under a single directory such as root with multiple branches instead of drives and directories in Windows. The Android file system has six primary partitions on every device that includes /boot, /system, /recovery, /data, /cache, and /misc. Additionally, some Android devices may have a couple of additional partitions based on the device model, which may include /sdcard and /sd-ext. Each partition has its restrictions and requires permissions, which are discussed below:
- /boot: Android devices cannot boot without this partition, which contains the kernel and boot image, which are essential components in starting up the Android OS. Although this partition is read-only, the user cannot alter it; nevertheless, rooted Android devices may. Any desktop file management program or adb-sdk can be used to access and operate the device once it has been rooted, but any changes made could cause boot problems.
- /system: It is one of the critical components of the Android file system that includes the entire Android OS, including GUI components and pre-installed applications also known as bloatware. It contains files and directories such as fonts, bins, apps, frameworks, and much more. It is also read-only for users that can be modified only on rooted devices when the user needs to install a custom ROM or troubleshoot.
- /recovery: This partition is dedicated to data back-up, wiping, restoring devices, software updates, factory resetting, and other maintenance operations. It is also read-only for users and includes recovery images for device restoration that can be used in case of software failure.
- /data: This includes all user and app data, including contacts, settings, music, videos, images, apps, and app support files, among other things. Users can change and remove different applications, app data, and user files using its extensive read and write options. After a factory reset, this partition may be erased, hence a suitable backup needs to be made for the restoration.
- /cache: This partition includes all temporary files generated by both the OS and applications. The user holds read and write permissions for this partition, and it can be cleared by the user, OS, or even by third-party cache-cleaning apps. Accessing this partition is faster and, as a result, device performance and speed can be improved. Cleaning it can free up some space, but it will take time and use more CPU usage when opening applications.
- /misc: This partition includes miscellaneous settings data, such as carrier details, hardware settings, configurations, bootloader state, and device lock state. These are stored in the file known as misc.img. It is a crucial partition as it contains essential settings, and any unknown modification or deletion can lead to malfunction or corruption of software or even prevent the device for booting. This partition also contains over-the-air (OTA) update data to keep the device up to date with the latest version or need to upgrade.
- /sdcard: The internal storage of an Android device often emulates this partition, which the Android system and user can access. Even applications can access and store the data in this partition. Typically, it is mounted as /mnt/sdcard or /storage/sdcard0. It is also available on the desktop for file transfer operations when the Android device is connected to a PC. Most applications are designed to make this partition as the default location for storing application-generated data.
- /sd-ext: This partition can be used when users need additional storage space for their Android devices, especially if the internal storage is near full or running out of space. Memory for this partition is allocated when an external device such as an SD card is connected to the device. It will be mounted as /mnt/sd-ext or /storage/sdcard1. The user can access it using the built-in file manager or third-party applications. The files can also be browsed on a PC via a USB connection.
OS File System
The design of the iOS file system reflects Apple’s controlled ecosystem strategy for maintaining a high degree of efficiency and security. The latest versions of iOS devices feature the Apple File System (APFS), which was built to offer more reliability, security, and compatibility. Here are the different components of the iOS file system:
Apple File System (APFS): This file system was introduced in iOS 10.3 replacing the previous HFS+ file system. It provides optimized performance for SSD/flash storage. APFS features strong encryption, space sharing, cloning for files and directories, and snapshot capabilities for system state restoration.
Hierarchical Structure: Like other file systems, the iOS file system is also organized in a pyramid-like or tree-like form, where entities or components are organized according to levels of importance, authority, or complexity.
Root Directory (/): The top-level directory.
- Applications: Stores all the applications installed on the iOS device.
- User data: Contains users’ personal data, such as photos, music, and documents.
- System files: Holds the operating system files necessary for iOS to run.
Key Directories: Directories play crucial roles in organizing and managing files and resources within the iOS application. Some key directories include:
- /Applications: Contains all built-in and third-party apps.
- /Library: Holds various system files and preferences.
- /usr: Includes user-related utilities and applications.
- /var: Contains variable data like logs and temporary files.
- /tmp: Temporary files that get cleared on reboot.
Understand Mobile Forensics Process
The mobile forensics process is a structured approach to recovering, analyzing, and presenting data from mobile devices in a way that is legally admissible. It typically involves a series of steps, each crucial to the integrity and success of the investigation.
Collect the Evidence
Evidence plays a significant role in the mobile forensic investigation process. It must be collected carefully to ensure that no evidence is lost or damaged. Digital evidence on mobile devices can be easily altered, deleted, or destroyed. Investigators should collect data and ensure that the data is neither lost nor tampered with to maintain its integrity such that it can be used for further analysis and presented in a court of law when required.
USB Debugging Mode (in Android)
It is an Android developer feature that can be activated from the Developer Options menu. USB debugging allows an Android device to establish communication with a computer/workstation that runs Android Software Developer Kit (SDK). Therefore, investigators should enable the USB debugging mode during evidence acquisition from the following settings: For Android 9 (API level 28) and higher: Settings → System → Advanced → Developer Options → USB debugging
USB Restriction Mode (in iOS)
This feature, available in the latest iOS versions, makes it difficult for hackers and law enforcement agencies/investigators to unlock an iPhone. The USB restriction mode improves security by not allowing any new data connections that have been terminated after an hour. The device should be unlocked to allow new or any previous connections. Therefore, once the USB restriction mode is activated, it is difficult to get any data from the iPhone. An investigator can either enter the DFU mode or install jailbreak to collect evidence. Therefore, when investigators obtain a device at the crime scene, they should use appropriate lightning cables to prevent the device from entering the USB restriction mode.
Investigators can perform the following steps while collecting a mobile device:
- Step 1: Check whether the mobile device is connected to a computer
- Step 2: Confirm the power state of the device
- If the device is found “ON” and “Unlocked,” then enable the Stay Awake setting on the device to keep the device active and connect it to a power source to charge it
- If the device is found “ON” and “Locked,” connect the device to a power source to ensure that the device does not shut down
- If the device is “OFF,” then leave it in the turned-off state because turning it ON could alter the evidence on the device (same as computers)
- Step 3: If the owner of the device is present at the scene, the law enforcement agents can obtain a passcode from the owner. If they deny, the investigators can get a warrant and proceed legally
While handling locked iOS devices, the investigators should preserve the evidence such that it can be accessed for data acquisition and examination:
- Do not remove the SIM card to disconnect the device from any network connection. This could do the following:
- Lock the device
- Disable the biometric unlock feature (unlocks only after providing the passcode)
- Activate the USB restriction mode
- The investigators should be aware of the expiration rules of the iPhone’s biometric identification subsystem because the fingerprint and face ID features allow five attempts to unlock a device.
- If the device is powered off, then data acquisition becomes difficult because of the following reasons:
- The encryption keys are wiped off from the RAM
- The investigator must deal with the “before first unlock” (BFU) state
- Lockdown records that are useful during logical acquisition become useless
- Tools such as MOBILedit Forensic and Elcomsoft iOS Forensic Toolkit can import the lockdown files from the suspect phone
- The lockdown records help investigators perform logical acquisition on a powered-on and locked iOS device
Document the Evidence
The investigators should document the scene after investigating for analysis and future reference. In addition, they must preserve the evidence to protect its integrity. Documentation of evidence is required to maintain a chain of custody that can be used as reference in the court of law.
Phone Identification
- Write down all information on display (photograph, if possible) and record the date and time when the device was collected.
- Note the physical condition of the phone and take pictures of the SIM card and SD card with identifying information.
- Identify a phone by its brand, model, OS, and service provider that can help in selecting the appropriate tools for the acquisition process.
Preserve the Evidence
Mobile devices should be protected from signal interruption, which might lead to data overwriting. To accomplish this, enable the Airplane mode (if possible) and store the device in signal containment devices and bags.
Signal Containment Device/Bags
- Faraday Bag: Faraday bags block external signals from interacting with a mobile phone, thereby preserving the integrity of the forensic evidence by preventing any remote communications that might alter the data.
- Signal Disruption Bag/Wireless Stronghold: Bag It prevents any type of signal from reaching a mobile device and stops the changes that may occur in a phone due to receiving a signal.
- Aluminium Foil: Mobile devices are wrapped with three layers of aluminium foil to prevent incoming signals and secure the mobile data.
Different methods are used for mobile data acquisition, such as:
- Cellular data acquisition
- File system acquisition
- Logical acquisition of device
- Physical acquisition of device
- Cloud data acquisition
Before performing logical and physical acquisition of the mobile device, investigators need to deal with phone locking and rooting/jailbreaking the device. These methods are forensically sound, invasive, and technical. Therefore, an expert investigator may also require more time to perform data acquisition and analysis. Selecting the appropriate data acquisition method depends on various factors:
- Time constraints for performing data extraction
- The data acquisition types supported by the device
- Required live data
- Recovery of deleted data
- Third-party application data
- Available tools
Investigate Cellular Network Data
Investigations related to cellular network data can be in real time and non-real time. Real-time investigations deal with the transmission of evidence over a network at the time of crime, including ongoing calls, device geolocation, and browsing session. Non-real-time investigations include the details of deleted call history, text messages, CDR data, and billing information that could serve as potential evidence during an investigation.
CDR Contents
CDRs contain information about user activities with the mobile phone. The service providers record and store this information in their database.
CDRs contain several categories of information such as:
- Phone number of the subscriber from where the call originated (calling party, A-party)
- Phone number receiving the call (called party, B-party)
- Called telephone number or numbers
- Names and addresses of the subscribers or registered users
- Date and time of the start and end of a communication
- Telephone service used, e.g., voice, conference call, SMS, or MMS
- IMSI of the calling and called party
- IMEI of the calling and called party
- Location label (cell ID) at the start and end of a communication
- Data mapping between the cell IDs and their geographical location at the start and end of a communication
- Route through which the call entered the exchange ▪ Route through which the call left the exchange
- Additional digits on the called number used to route or charge the call
- Disposition or results of the call, indicating, for example, whether the call was connected
- Any fault condition encountered
Perform File System Acquisition
Performing file system acquisition is a crucial part of investigating a mobile device as this allows the investigators to obtain additional information compared to the logical acquisition. This is possible because it allows access to the file system data for more potential evidence.
Subscriber Identity Module (SIM)
A Subscriber Identity Module, often referred to as a SIM card, is a universal integrated circuit card that allows mobile devices to connect to the cellular network for communication purposes. A SIM card is a component that allows users to connect or communicate with other users. It is a removable component containing essential information about the subscriber. A SIM authenticates a user to connect to the network and enables access to subscribed services.
A SIM provides users with the benefit of storing information such as phone numbers and messages. It has both volatile and non-volatile memory. The file system of a SIM resides in its non-volatile memory.
International Mobile Equipment Identifier (IMEI)
The International Mobile Equipment Identifier (IMEI) is a unique 15-digit number that identifies mobile equipment in GSM-based systems. It represents the manufacturer, model type, and approved country. Each GSM, UMTS, and iDEN mobile phone has a different IMEI number, usually printed and located on the battery of the mobile phone. In some mobile devices (locked/unlocked), the IMEI number can be found on the SIM tray or the back of the mobile case.
The first eight digits of the IMEI are known as the Type Allocation Code, which provides information about the model and origin. For powered-on GSM and UMTS phones, the IMEI number can be retrieved by typing *#06# on the mobile keypad. The IMEI number is used for legitimate purposes and is used by GSM to identify devices and prevent access to stolen mobile phones.
SIM Cloning
For forensic investigation purposes involving the SIM cards of phones, forensic investigators should clone the SIM cards for further investigation to avoid accidental tampering with original SIM data. Investigators can use the MOBILedit tool to clone the original SIM card of a phone being investigated even without knowing the PIN or create new SIM cards with any ICCID. The purpose of this tool is to isolate a phone from its network for secure investigations.
SIM Data Acquisition Using Oxygen Forensic Extractor
Forensic officers acquire SIM card data to nab the culprit who is involved in mobile crimes. Investigators use specialized tools such as Oxygen Forensic Extractor for data extraction and forensic analysis of evidence acquired from the suspected mobile.
Oxygen Forensic Extractor is used for data extraction from mobile devices. The Extractor allows investigators to connect to a wide range of Apple iOS and Android devices, import various device backups to quickly recover valuable digital evidence. Once data is extracted, investigators can choose to save it to an OFB backup which can be later imported into Oxygen Forensic Detective, or export it immediately to any report formats, such as PDF, HTML, XML, etc.
To extract data from a SIM card and perform SIM card forensics, the target SIM card must be removed from a mobile device and placed in the SIM card reader, which is then attached to the forensic workstation.
Understand Phone Locks, Rooting, and Jailbreaking of Mobile Devices
Phone Locking on Android
Phone locking is a basic security feature provided by mobile device manufacturers to prevent unauthorized access to a phone. Android mobile phones use three types of phone lock schemes to prevent unauthorized user access, namely PIN lock, PATTERN lock, and PASSWORD lock. Android devices have several options to prevent others from accessing a device in comparison to iPhone devices. This phone lock adds a layer of security to mobile devices.
- PIN Lock: The personal identification number (PIN) is the easiest way to lock a mobile phone for local security. The selected PIN should be at least four digits in length; it can also be a longer, more complicated password containing both letters and numbers.
- Pattern Lock: It is an alternative to the PIN lock. It allows the device users to trace a unique pattern with their finger over a 3 x 3 grid of dots to unlock their mobile. Pattern lock is more convenient; users can quickly swipe on a particular path to unlock the device.
- Password Lock: A password lock has the same functionality as a PIN lock, except that the 4 to 16-digit access code contains letters and punctuations along with numbers.
If a device is found in the locked state, the primary task of the forensic investigator at the workstation involves unlocking the phone to gain access to it. Investigators can use various tools and techniques to bypass this security feature.
Bypassing Locked Android Devices
Investigators must evade the security lock of a suspected Android device found at the crime scene to detect and analyze potential evidence stored in it. The following are the different methods that investigators can use to bypass locked Android devices:
Method 1: Unlock Android Device without Password Using DroidKit
Investigators use DroidKit to remove all types of lock screens on Android devices without a password. It also helps in bypassing FRP lock on majority of Android devices.
Method 2: Bypass Android Lock Using Dr.Fone – Screen Unlock (Android)
Investigators use Dr.Fone – Screen Unlock (Android) to remove the Android lock screens. It does not just bypass Android pattern locks but also evades PINs, passwords, and FRP Locks.
Phone Locking on iOS
Setting up a passcode on an iOS mobile device is a significant part of securing data from unauthorized access. iOS devices prompt users to enter the passcode before using the device each time.
There are various types of passcodes in an iOS device.
- Numeric Passcode: A six-digit numeric password is the default security mechanism in iOS devices. Even if face unlock is enabled, Apple devices ask for a passcode when a user restarts the device, thereby offering enhanced protection in the case of a lost or stolen device.
- Face Unlock: Apple Face ID is a facial-recognition technology that replaced the fingerprint mechanism on the latest iPhone devices (iPhone X and above).
If the device obtained from a crime scene is in a locked state, it must be unlocked. If the iOS device is connected to the computer, the forensic investigator can use the lockdown records that are stored on the computer to perform logical acquisition without unlocking the device.
Rooting of Android Devices
The goal of rooting Android is to overcome the restrictions imposed by hardware manufacturers and carriers, thereby resulting in the ability to modify or replace system applications and settings, run apps that require admin privileges, remove and replace a device’s OS, remove applications pre-installed by its manufacturer or carrier, or perform other operations that are otherwise inaccessible to the typical Android user. Rooting allows Android users to attain privileged control (known as “root access”) within Android’s subsystem.
Rooting of Android Devices Using KingoRoot
During a forensic investigation, investigators come across different types of Android devices. In case a device is unrooted, investigators should use third-party rooting tools such as KingoRoot to root the device and perform a forensic examination.
Rooting can be performed on an Android device only after unlocking the bootloader, which is a security feature available since Android Lollipop (Version 5.0). If the bootloader of a mobile device is unlocked, the forensic investigator can root the device to perform data acquisition. To avoid data loss, the forensic investigator must remember to take a backup of the device data or perform logical acquisition before rooting the device.
Note: Physical acquisition can only be performed on rooted Android devices.
Jailbreaking of iOS Devices
Jailbreaking is defined as the process of installing a modified set of kernel patches that allow users to run third-party applications not signed by the OS vendor. It is the process of bypassing the user limitations set by Apple, such as modifying the OS, attaining admin privileges, and installing unofficially approved apps via “side loading.” You can accomplish jailbreaking by simply modifying the iOS system kernels. One reason for jailbreaking iOS devices such as iPhone, iPad, and iPod Touch are to expand the feature set restricted by Apple and its App Store or install third-party security tools for testing. Jailbreaking provides root access to the OS and permits downloading of third-party applications, themes, and extensions that are unavailable through the official Apple App Store. Jailbreaking also removes sandbox restrictions, allowing malicious apps to access restricted mobile resources and information.
Failure of Jailbreaks
The jailbreaking process exploits chains of vulnerabilities on the device to obtain root privileges. Because multiple vulnerabilities are exploited, this may result in failure of the jailbreaking process.
The jailbreaks developed for earlier versions involved patching the device kernel and attempting to bypass the system Kernel Patch Protection by patching other parts of the OS. This procedure could make the device unbootable, resulting in failure of the investigation process. However, the modern jailbreaks targeting later versions do not modify the device kernel; hence, the investigators need not deal with Kernel Patch Protection.
Perform Logical Acquisition on Mobile Devices
In mobile forensics, logical acquisition refers to the creation of a bit-by-bit copy of the logical storage on a mobile device.
The logical storage contains objects such as directories and files that are accessible to the user. Logical acquisition generally recovers data that is not deleted. System files and deleted data cannot be captured under logical acquisition.
Live data that can be acquired using logical acquisition includes call logs and text messages, passwords to active social media accounts, IMEI and electronic serial number (ESN) data, contact lists, data from installed applications, and saved photos and videos. A full device backup can also be considered as logical acquisition.
For Android devices, logical acquisition can be performed manually by running adb commands in a terminal window; however, for iOS devices, it can be performed through the Finder app if the investigator can determine or bypass the device passcode.
Android Debug Bridge (ADB)
When an Android device is used as digital evidence in the court of law, the forensic investigator must perform data acquisition on the device to extract useful artifacts that could help solve the case.
Android Debug Bridge (ADB) is a command-line utility that establishes a connection between a mobile device and computer over USB. The ADB commands facilitate device actions such as copying files back and forth, installing and uninstalling applications, and running shell commands on a device.
These commands allow investigators to acquire the device root shell that can be used to run various commands on the device. ADB is a client-server program that contains three components:
- Client: The client runs on the forensic workstation and issues adb commands to install or uninstall applications and acquire data from the device.
- Daemon: It is a background process that runs commands on a device.
- Server: It runs as a background process on a forensic workstation and manages the communication between the client and the daemon.
Logical Acquisition of Android Devices: Using “adb pull” Command
On an unlocked and unrooted Android device, the investigator can perform logical acquisition by connecting the device to the forensic workstation via USB and running the adb pull command to acquire data.
ADB is a command-line tool that establishes the connection between an Android device and a forensic workstation.
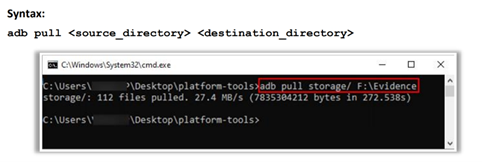
Note: Logical acquisition can only be performed if the investigator bypasses the device password.
The adb pull command fetches files & folders from the Android device to the forensic workstation. If the destination directory is not provided, the files will be pulled to the current directory location in the terminal.
Logical Acquisition of iOS Devices: Using Finder
On an unlocked and un-jailbroken device, the investigator can obtain backup of the device using Finder.
Steps to create an iPhone backup using Finder:
- Connect the iPhone to a Mac computer via a USB cable
- It will ask for the device passcode or to Trust This Computer
- Select the connected device name displayed in the sidebar of any window in the Finder
- Under Backups, select “Back Up all of the data on your iPhone to this Mac”
- Select Encrypt local backup; next, the system will ask for ‘password to protect the backup or click on Change Password’ to set the password
- Click on Back Up Now to start the backup
From Finder, investigators can retrieve shared files, media files, plist files, etc. which can serve as a potential source of evidence during an investigation even if the device is not jailbroken.
Note: When the investigator attempts to take a backup of the iPhone using Finder, the device prompts for a passcode. Hence, the passcode of the device must be known.
Extracting Data from Android Devices Using Magnet ACQUIRE
Magnet ACQUIRE allows forensic investigators to recover forensic images as evidence from various devices such as iOS, Android, hard drives, and USBs. This tool also helps investigators to perform data extraction from Android devices and analyze the acquired data.
Cloud Data Acquisition on Android and iOS Devices
Cloud forensics is a part of digital forensics that mainly focuses on the extraction of digital evidence from cloud storage. This includes the extraction of data including network assets, application data, server data, and data such as files or folders stored in different drives. Currently, all smartphones are integrated with cloud storage that provides extra storage space to users and helps them synchronize their data to the cloud. When synchronization is turned ON, the user activities are recorded in the cloud storage. Hence, the forensic examination of the device provides valuable evidence related to the activities performed on the device which could be helpful during the investigation.
Android devices include Google Drive storage, and users require a Google account to access this storage space. The latest versions of Android do not provide cloud backups like iOS. Instead, forensic investigators can legally obtain the user ID and passwords from the cloud service provider to access and examine the data stored on the drive. The data include Gmail, contacts, data stored on the drive, Google Chrome bookmarks, user location history, and registered Android devices, etc.
Apple users use iCloud storage as a cloud service. Investigators can obtain backups from iCloud that contain the same information as the backups created via iTunes. To obtain these backups, the investigator should contain an Apple ID and password or a binary authentication token from the user’s computer that is synced with/connected to the device. If the owner of the device is present at the scene, forensic investigators can legally obtain the user ID and password to examine the evidence.
Physical Acquisition
Physical acquisition involves extracting all data from a mobile device, including both allocated and unallocated space. The aim is to create a bit-by-bit replication of all data within the device, including hidden and deleted data. Performing physical acquisition of mobile phone data is challenging because device manufacturers do not allow arbitrary reading of the device memory.
Successful physical acquisition can provide forensic investigators with valuable information, such as deleted text messages, contacts, call logs, passwords, location data, GPS information, deleted files, photos, and videos.
Physical acquisition can be performed manually on rooted (Android) or jailbroken (iOS) devices. The advantage of physical data acquisition is that it eliminates the risk of compromising data integrity by using a write-blocker mechanism on the interface to create a copy of the original data. Once completed, physical data acquisition does not leave any traces of the investigation on the mobile device.
Investigators should use tools such as Cellebrite Premium, MOBILedit Forensic Express, and Elcomsoft iOS Forensic Toolkit to perform physical acquisition without the need for rooting or jailbreaking the devices.
Physical Acquisition of Android Devices: Using dd Command
A forensic image is acquired from a rooted Android device using dd command (Local Acquisition). To perform physical acquisition of an Android device, insert an SD card into the device with sufficient storage space for the evidence file.
Steps involved in acquiring the forensic image file from a rooted Android device:
- Connect the Android device to the forensic workstation via a USB cable
- Using SDK platform tools and adb commands, acquire the root shell of the Android device
- After entering the device root shell, identify the source destination drive and use the dd command to acquire the physical image of the device
Command: dd if=<source_drive> of=<output_drive> bs=512k
Note: Physical acquisition is possible only on rooted Android devices.
SQLite Database Extraction
SQLite databases extracted from mobile device memory dumps are of primary interest to forensic experts. The SQLite database software is an open-source, public domain database package. Mobile phones use database files to store important information related to the device owner. This information includes user contacts, text messages, email messages, and other sensitive data. The SQLite database usually has the file extension “.sqlitedb.” Some databases also use other forms of extensions such as “.db.” Investigators can extract this data from the SQLite database to perform forensic analysis. The SQLite database files can be extracted using SQLite browsing tools
Extracting the database information from an SQLite database:
- To extract the image data, use the SQLite “.dump”
command: $ sqlite3 AddressBookImages.sqlitedb
sqlite> .output AddressBookImages.txt
sqlite> .dump ABFullSizeImage
- To extract the target calendar events on an iPhone, investigators should analyze: /private/var/mobile/Library/Calendar/Calendar.sqlitedb
- Phone book: /data/data/com.android.providers.contacts/databases/contacts2.db
- SMS/MMS: /data/user/0/com.android.providers.telephony/databases/mmssms.db
- Calendar: /data/com.android.providers.calendar/databases/calendar.db
- User data: /data/system_ce/0/accounts_ce.db
- Web browser history: /data/data/com.android.browser/databases/browser2.db
- Dictionary: /data/data/com.android.providers.userdictionary/databases/user_di ct.db
Chip-off Forensics
Chip-off forensics refers to a complete bit-stream imaging of a device containing embedded flash
memory (NAND, NOR, eMMC, or eMPC). This process allows extraction and analysis of the data stored on flash memory chips, which may allow collection of all data stored on the subject evidence device. In chip-off forensics, data such as contacts, call data, SMS, instant chat messages, emails, web history, applications (all data), SIM data, and memory card data are extracted and analyzed.
In the chip-off procedure, the flash memory of mobile devices is physically removed for data acquisition. Investigators can make a binary image of the removed chip and perform chip-off forensics. This method will allow the investigators to extract data from password locked devices or damaged devices.
Chip-off Forensics Process
The chip-off forensic process involves the examination of data on the chips. The data extraction process is complex and challenging with the available variety of chip types that contain different data formats. Investigators require professional training to perform this type of data extraction.
The processes involved in chip-off forensics are as follows:
- Assessment: In this phase, the investigators should study the device and be updated regarding its functionalities. The strategy of mobile forensic investigation differs for each device. There is no prescribed standard process that should be followed.
In any chip-off process, the primary step involves the identification of the evidence and performing research to confirm that no other physical extraction process is applicable.
- Acquisition: In this phase, the investigator removes the memory chip physically and cleans or repairs it if required. Chip programmers and adapters are used to acquire a bit-stream image.

- Analysis: The raw bit-stream image is analyzed for evidence. Despite the differences in the device OS, file systems, and data storage structures, the forensic investigator should understand the low-level characteristics of the flash memory.
Android Logs
An Android log is a record of messages and events which are generated by the Android Operating System or Android applications. Analyzing these logs helps the forensic investigators to acquire information of application behavior, warnings, errors, crashes, and other critical data in the form of distinct log of messages that can be useful for further analysis during an investigation.
Importance of Android logs in Forensic Investigation
Android logs play a significant role in forensic investigation of an Android device by providing information such as:
- Different events that can be reconstructed by forensic investigators in a chronological way by capturing system activities and actions taken by a device user.
- Detect various suspicious events such as malware installation, lock bypass, data breach, or unauthorized access.
- Analyze user behaviour by understanding digital footprints such as app usage patterns, connection activities, browsing history, and much more.
- In case of data loss or deletion, logs can help investigators in data recovery by examining logs of deleted files or metadata associated with user actions. In addition, investigators can analyze the Android logs to identify the remains of deleted files and recover them if required during the investigation process.
The components of the Android Log Buffer are as follows:
- Events: It consists of system event information.
- Main: It refers to the main application log.
- Radio: It consists of phone-and radio-related information.
- System: It consists of debugging and low-level system messages.
The log message comprises of the following:
- Tag: It signifies the source of the log.
- Timestamp: It refers to the time the message was generated.
- Message log level: It refers to the priority level of the log message.
- Message: It consists of complete error description, information, or exceptions, etc.
Examining Android Logs Using Logcat
Logcat is a command line and debugging tool for Android that can display the device logs generated in Android devices in real time. Forensic investigators can use this tool to obtain critical device information such as errors, tags, messages, etc. In addition, investigators can view and filter the logs in both the command line and Android Studio.
Investigators can query the logs using key-value pairs, which will narrow down the size of logs and investigators can focus on specific logs. Some of the key queries that can be used by the investigators are as follows:
- tag: Filters based on tag field of logs
- Package: Filters based on package of logging app
- process: Filters based on process name of logging app
- message: Filters the logs if contains queried message
- level: Filters based on logs severity
- age: Filters log timestamp within specified queried duration
Logcat will automatically notice if any process has crashed or restarted by logging PROCESS ENDED and PROCESS STARTED respectively. These logs will help investigators reconstruct the timeline of application events, track any bypass of security applications, and retrieve much more information for investigations.
Android Log Analysis Tools
Investigators can also use tools such as Lograbbit for analyzing the Android logs on a macOS workstation to import, filter, and analyze those logs as described below:
- LogRabbit: It is a macOS based tool that helps investigators import, filter, and analyze the Android logs. Investigators can filter the logs based on application name, log level, tag field, keywords, timestamp, process ID, thread ID, etc. In addition, the filters can be combined to avoid unnecessary logs and list the required precise logs. Investigators can also save and open the logs for further investigations.
Collecting WhatsApp Artifacts from Android Devices
Forensic investigators can extract WhatsApp artifacts from a compromised Android device either by gaining root access to it or by acquiring a physical memory dump of the Android file system. In an Android device, WhatsApp artifacts can be found at the location /Android/media/com.whatsapp/WhatsApp/ as three folders:
- Backups: This folder contains encrypted backup copies of WhatsApp data such as the WhatsApp contacts, wallpapers, stickers, chat settings, etc. in crypt14 file format. The two important WhatsApp backup files in this folder are as follows:
- db.crypt14: It is a database file that contains information about the WhatsApp user’s contacts such as the contact ID, status, display name, timestamps, etc.
- db.crypt14: It is a database file that stores the backup copies of the graphics stickers shared via WhatsApp Messenger.
- Databases: This folder contains encrypted copies of sent and received WhatsApp chat history, including the contact number, message content, status, timestamps, and information about attached files. It stores seven database files that hold the last 7 days’ WhatsApp data in msgstore-YYYY-MM-DD.1.db.crypt14 format, and their incremental backup copies.
Media: This folder contains all the multimedia content shared via WhatsApp Messenger. Investigators can extract these shared multimedia artifacts from the following subfolders:
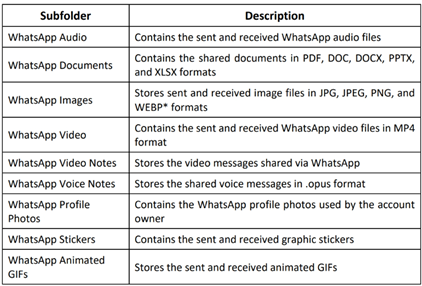
Analyzing Android Chrome Artifacts
Chrome artifacts are activity clues associated with Android devices. These artifacts may include cookies, cache, bookmarks, history, etc. which play a significant role during the investigation. Understanding which browsers were installed on the suspect mobile device and their artifacts’ extraction could provide valuable information for identifying the culprit. Investigators can use tools such as Magnet AXIOM and AXIOM Cyber to extract these artifacts from an Android device.
Investigators can find Android Chrome artifacts in the following locations:

Analyzing iOS Safari Artifacts
Safari artifacts are activity clues associated with iOS devices. These artifacts may include cookies, cache, bookmarks, history, etc. which play a significant role during the investigation. Understanding which browsers were installed on the suspect mobile device and extracting their artifacts could provide valuable information for identifying the culprit. Investigators can use tools such as Magnet AXIOM and AXIOM Cyber to extract these artifacts from iOS.
Investigators can find iOS Safari artifacts at the following locations:


Reading this evokes the sensation of observing sunlight shift across a quiet landscape. Each sentence illuminates detail subtly, revealing nuance and layered meaning, while creating a reflective space where the reader can linger, consider, and absorb the depth of thought and emotion present.